How to use headphones or Bluetooth to hack and take control of any Android device
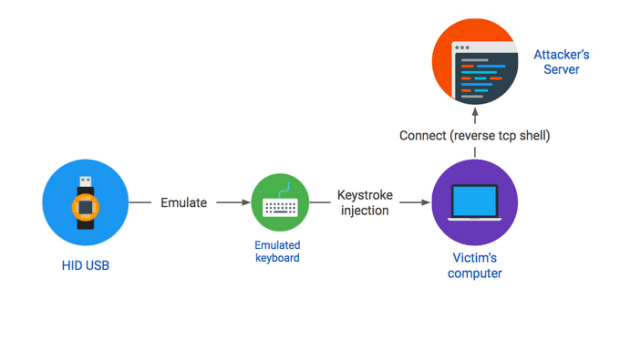
A recent research published by vulnerability testing specialists from Purdue University details a new exploit that abuses some Android operating system smartphones through the use of malicious peripheral devices (specificallyRead More →