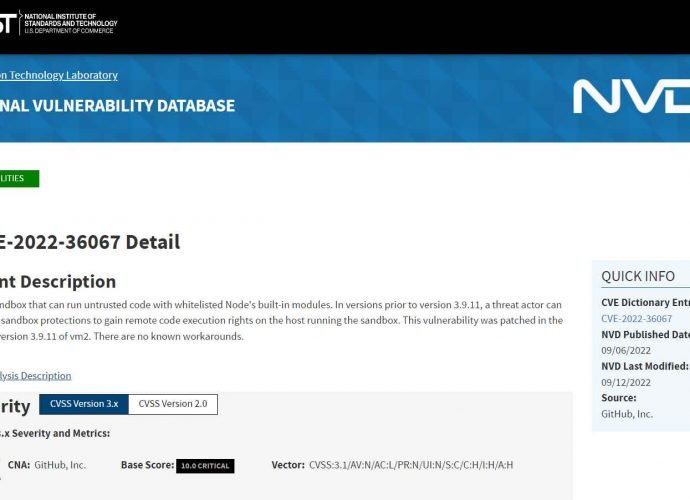
2 important vulnerabilities (XXE & RCE) in VMware Cloud Foundation. Patch immediately
The serious XML External Entity (XXE) and remote code execution (RCE) vulnerabilities in Cloud Foundation have been patched, according to VMware. CVE-2021-39144 The first of the issues is a remoteRead More →