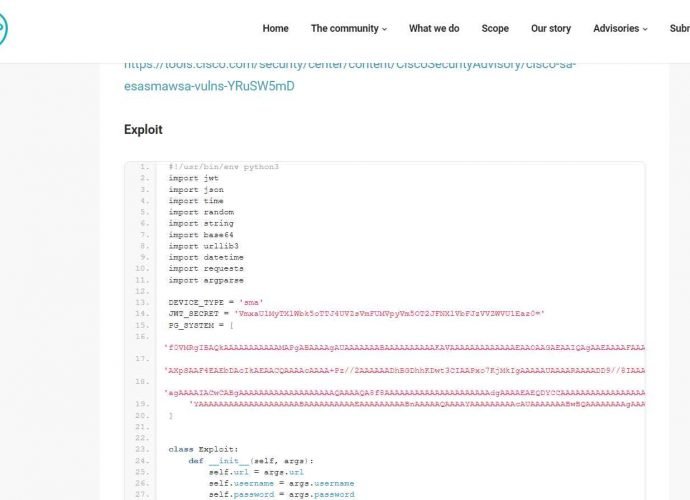
This exploit code allows Low level privileges user to get full admin privileges on vulnerable Cisco Secure Manager Appliance and Cisco Email Security Appliance
Two vulnerabilities in Cisco’s product line, including high-severity flaws in the Cisco Email Security Appliance, Cisco Secure Email and Web Manager, and Cisco Secure Web Appliance Next Generation Management products,Read More →