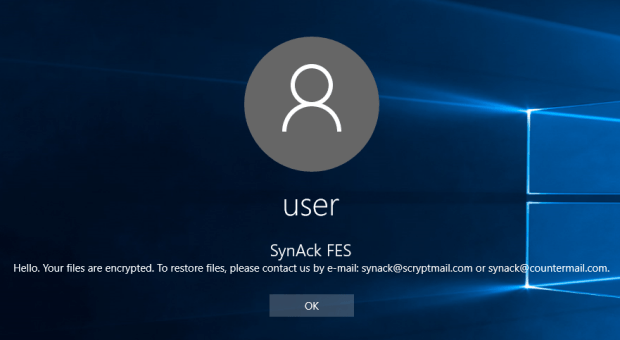
Ransomware attack causes blackout on screens of Bristol Airport
Airport officials refused to pay the ransom and opted to manual re-establishment of all affected systems The flight information screens at Bristol Airport (UK) suffered a blackout last weekend. AccordingRead More →