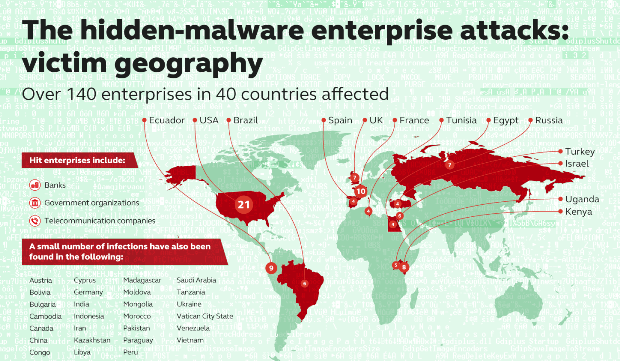
Fileless attacks against enterprise networks
2017-02-09
During incident response, a team of security specialists needs to follow the artefacts that attackers have left in the network. Artefacts are stored in logs, memories and hard drives. Unfortunately,Read More →