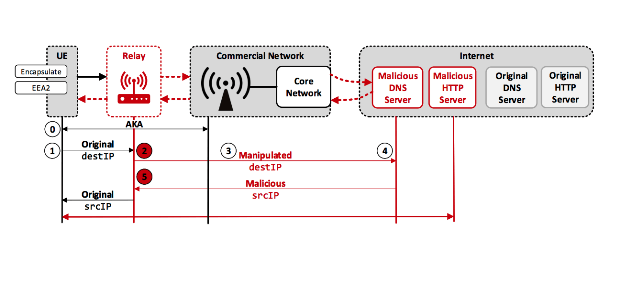
LTE network critical vulnerability: An attacker can impersonate any cell phone using another device
One of the most well-known security standards in telecommunications and mobile networks is mutual authentication, which allows a smartphone and mobile network to verify their identities. In the Long TermRead More →