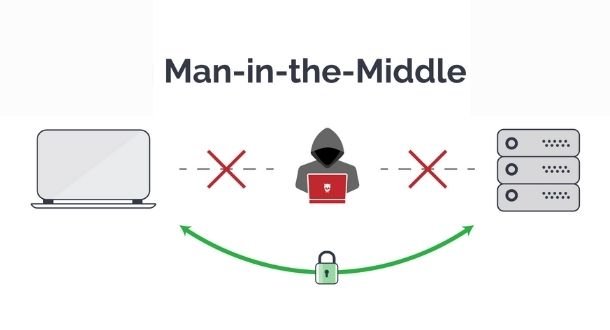
The best 6 MiTM (Man-in-The-Middle) attack tools that every ethical hacker should have
Man-in-The-Middle (MiTM) attacks are one of the most popular hacking techniques nowadays, and occur when a third party arbitrarily breaks into an established network session or in a data transferRead More →