Hack-Proof Your Cloud: The Step-by-Step Continuous Threat Exposure Management CTEM Strategy for AWS & AZURE
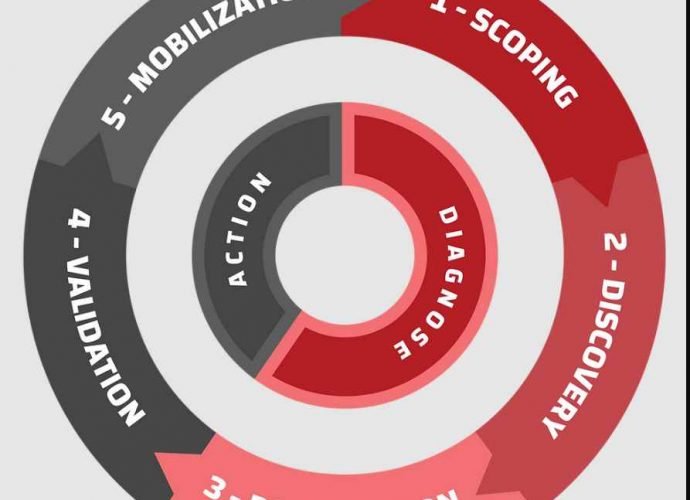
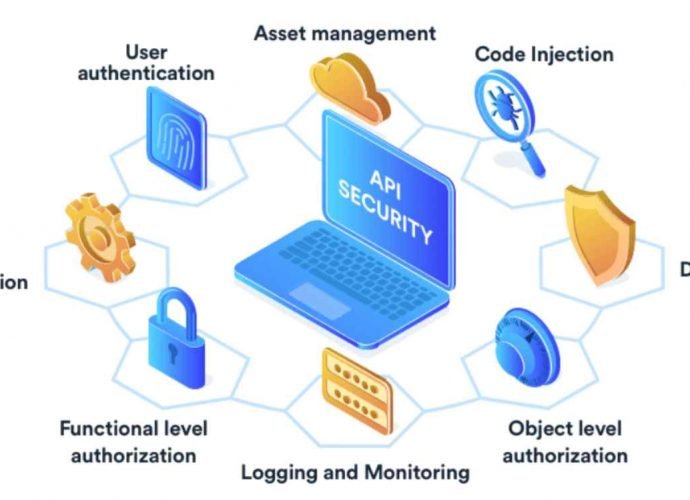
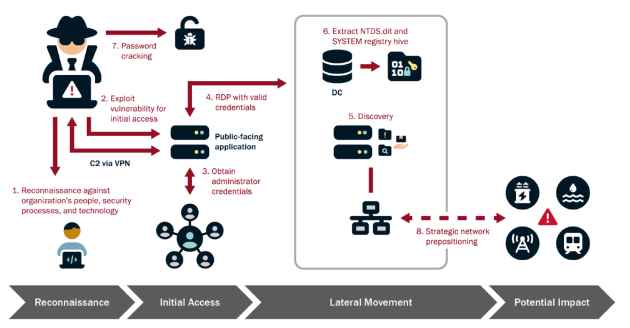
Continuous Threat Exposure Management (CTEM) is an evolving cybersecurity practice focused on identifying, assessing, prioritizing, and addressing security weaknesses and vulnerabilities in an organization’s digital assets and networks continuously. UnlikeRead More →