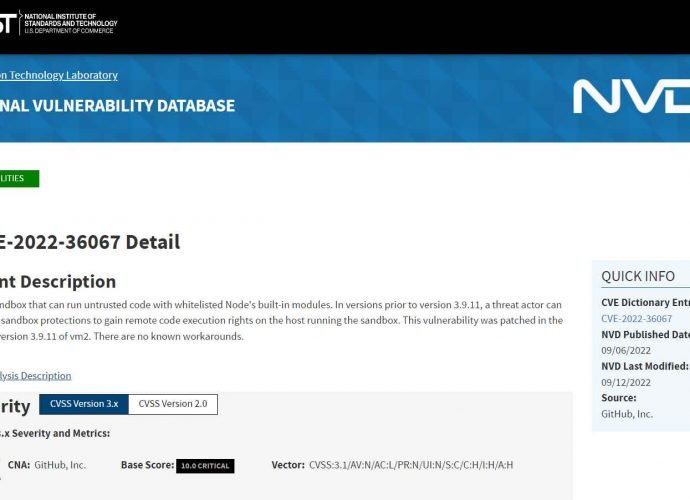
5 critical remote code execution vulnerabilities in Linux kernel. !Patch immediately!
The Linux kernel WiFi stack has five serious flaws, according to research, which a hacker might use to execute arbitrary code or inflict a denial of service. CVE-2022-42719 The vulnerability,Read More →