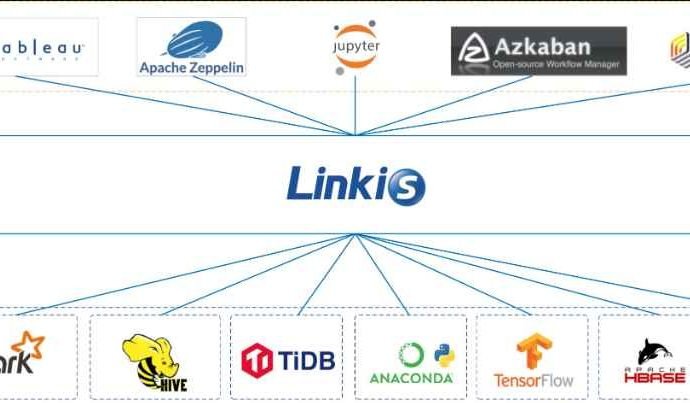
Critical Remote code execution flaw in Apache Linkis
Apache Linkis creates a compute middleware layer to unify task and engine governance and orchestration while enabling cross-engine context sharing. It also provides standardized interfaces (REST, JDBC, WebSocket, etc.) toRead More →