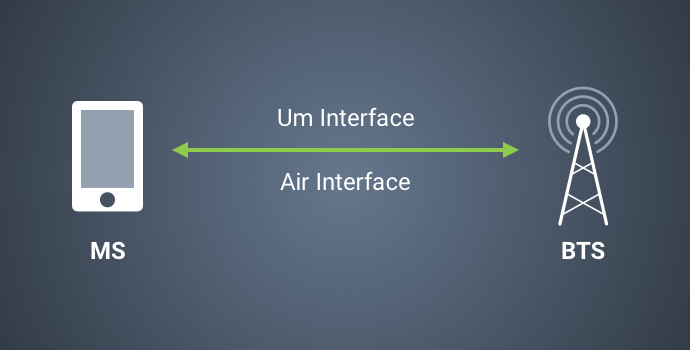
Critical Flaws Let Attackers Hijack Cellular Phone Towers
2016-08-24
During the last weeks we’ve been investigating multiple aspects of GSM security such as protocol vulnerabilities as well as source auditing the world’s most common open source software products thatRead More →