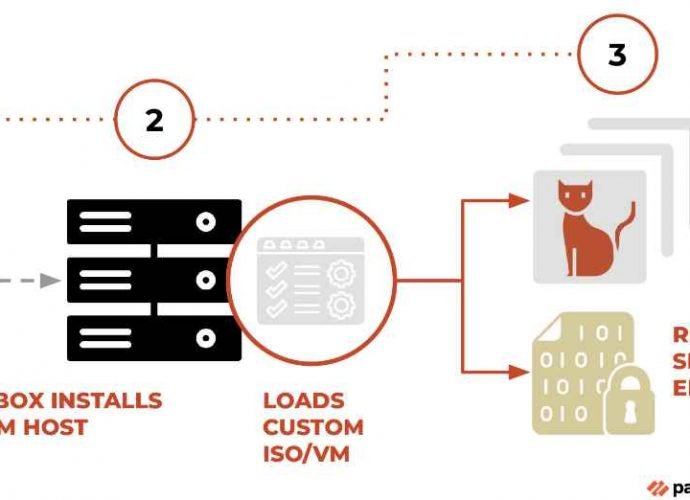
Redcliffe Labs, India’s Medical Diagnostic Company leaks 7 TB of customer data. Will it pay 250 crore fine?
Redcliffe Labs is one of the most comprehensive testing facilities in India. It provides more than 3,600 different diagnostic tests for illnesses and wellbeing. Users of the mobile application haveRead More →