Apple mitigates but doesn’t fully fix critical iOS Airdrop vulnerability
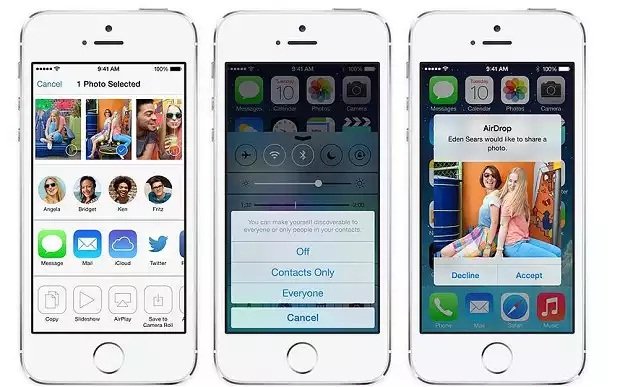
Proof-of-concept exploit installs malicious app on nearby iPhones. Apple has mitigated a critical iOS vulnerability that allows attackers within Bluetooth range of an iPhone to install malicious apps using theRead More →