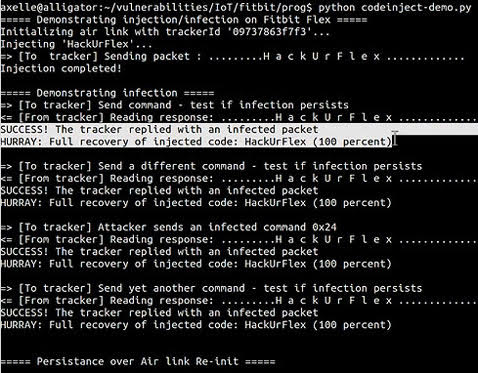
Fitbit trackers can easily be infected with malware, and spread it on
Security researcher Axelle Apvrille has managed to deliver malware to a FitBit Flex fitness tracker, and to spread the infection to any computer that the device is subsequently connected to.Read More →