Webhosting company loses 13 million plaintext passwords, says “thanks for your understanding”
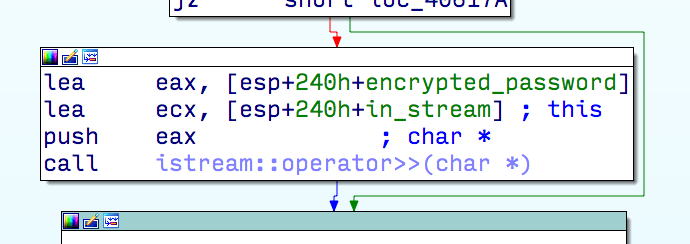
There’s another data breach to report – and it’s a big one, affecting approximately 13 million customers of the “free” web hosting company 000Webhost. The breached data, which includes customerRead More →