Ransomware on Your TV, Get Ready, It’s Coming
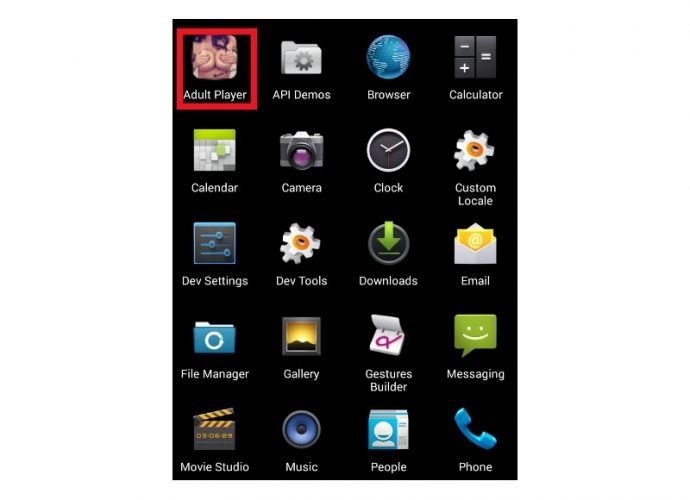
A PoC shows the future dangers for smart TV sets.Many cyber-security vendors view ransomware as 2016’s biggest threat, and to help drive this point home, a Symantec security researcher demonstratedRead More →