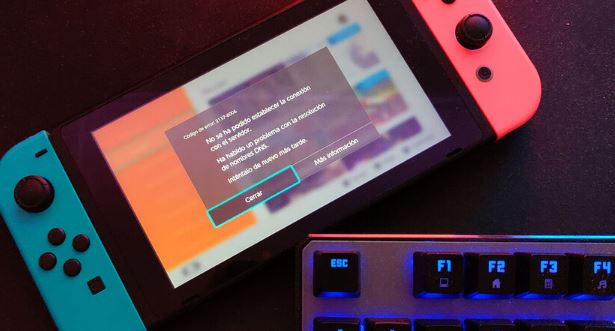
Nintendo hacked completely. Source Code for N64, Wii & GameCube published
Network security course experts have closely followed Nintendo-related news recently. One of the most striking facts of the cybersecurity community is a massive data leak from the video game company,Read More →