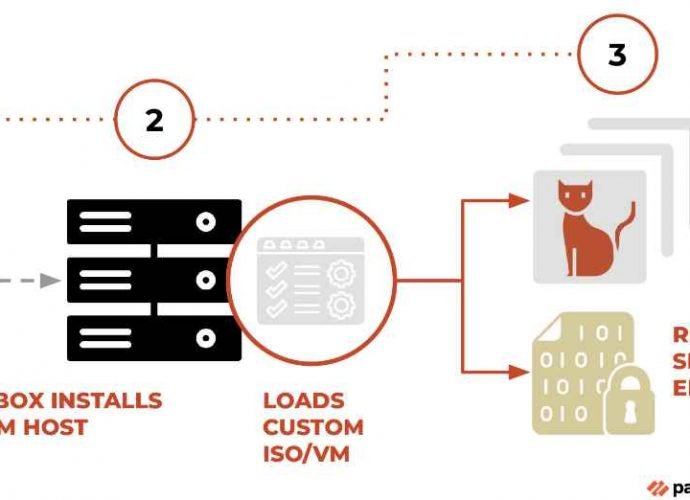
How APT28 Infiltrates Networks in French Universities & Nuclear Plants Without Detection
According to a recent study published by the leading cybersecurity agency in France, a hacking organisation affiliated with Russia’s military intelligence agency has been spying on French colleges, corporations, thinkRead More →