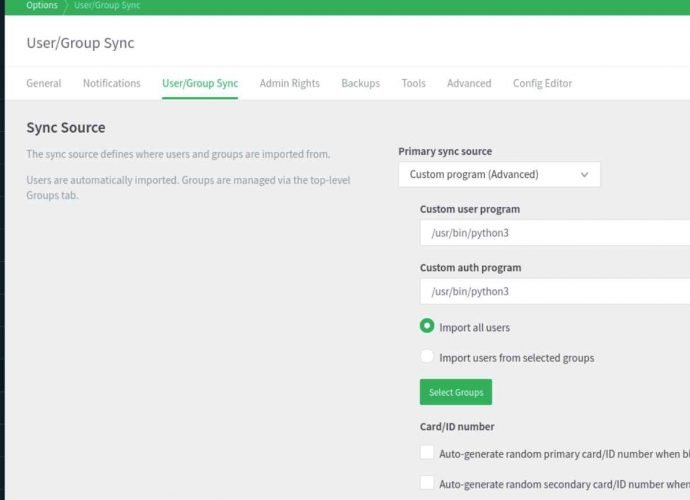
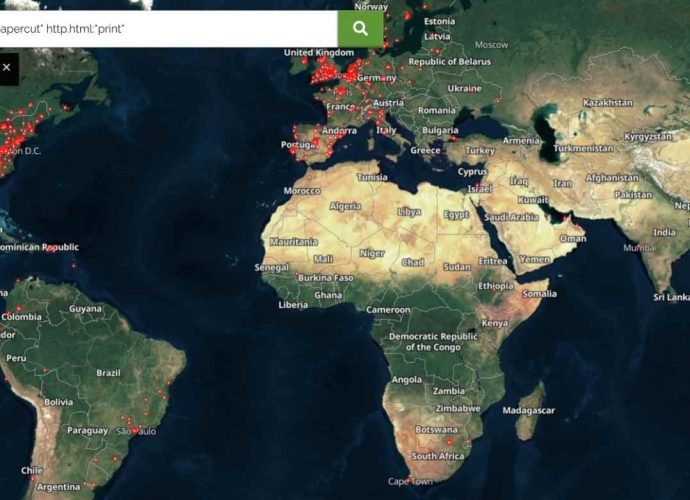
Easily get root user privileges in Linux 6.3.1 using this vulnerability via exploit code
The Linux kernel is the most important part of the Linux operating system. It is in charge of managing system resources, delivering necessary services, and guaranteeing the general stability ofRead More →