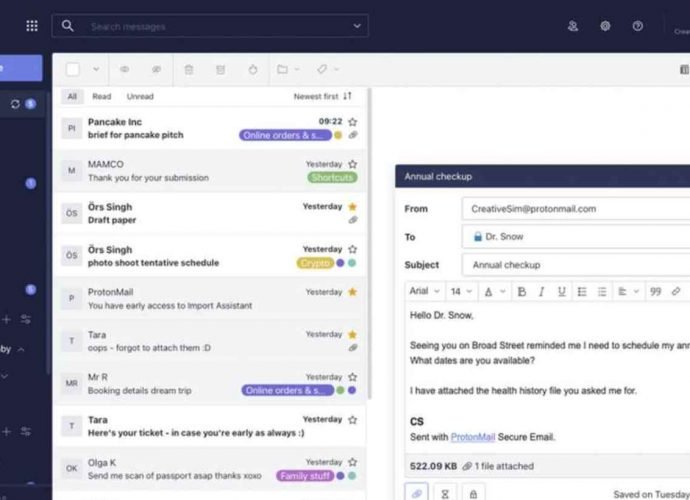
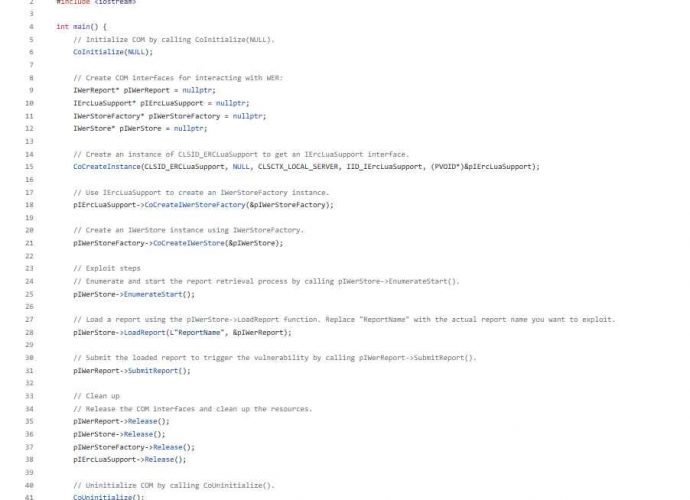
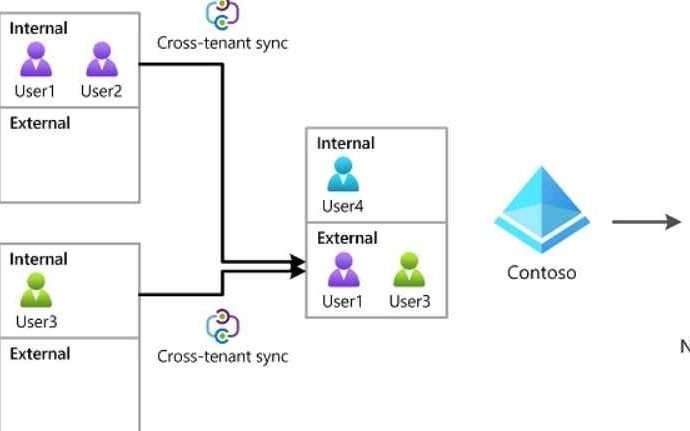
Proton Mail vulnerabilities allow stealing decrypted emails and impersonate users
A webmail service known for its emphasis on users’ privacy, Proton Mail, has serious code flaws that were discovered by a group of researchers. These vulnerabilities might have put theRead More →