Eight high-severity vulnerabilities in Splunk Enterprise Software allow threat actors to take control of a network
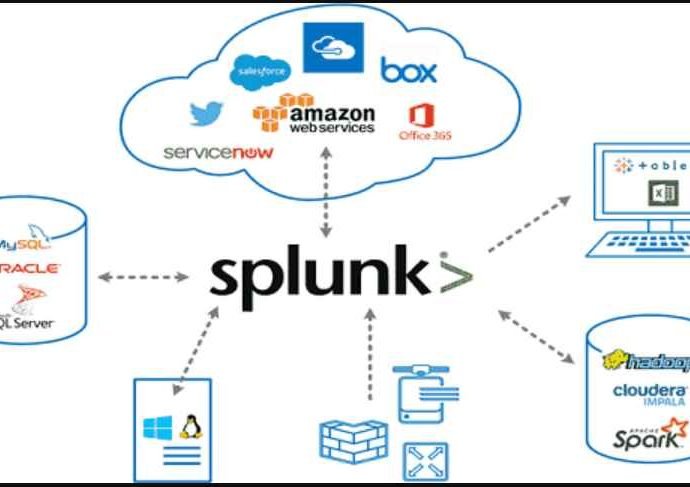
With the use of the Splunk software, real-time data can be collected, indexed, and corroborated in a searchable repository from which graphs, reports, alarms, dashboards, and visualizations may be produced.Read More →