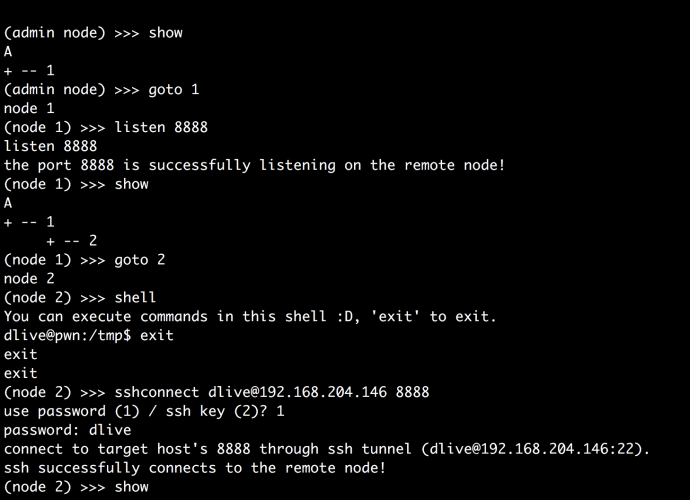
How Ship Satellite Communications are hacked and how to keep them safe
What is Ship Satellite Communication ? According to the ethical hacking researcher of International Institute of Cyber Security, Ship security satellite is a process where external devices like sailor 100Read More →