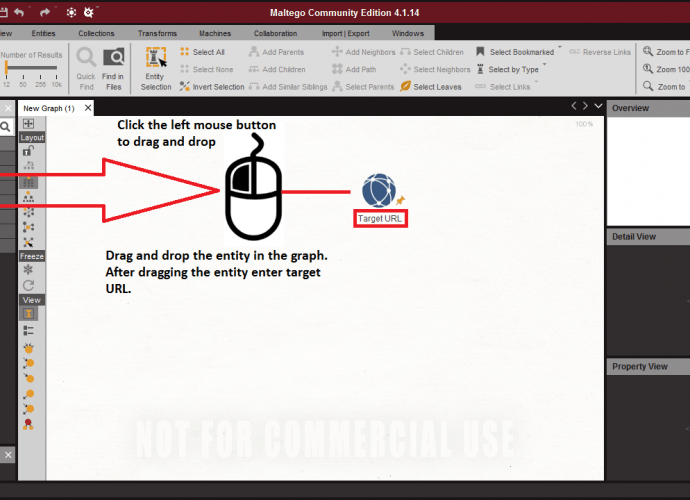
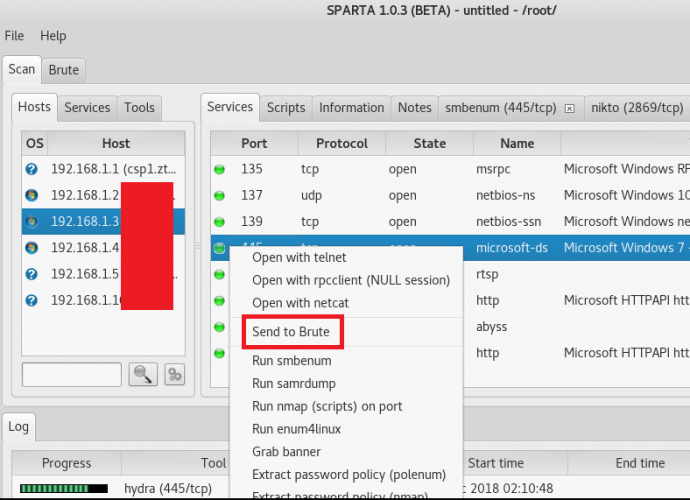
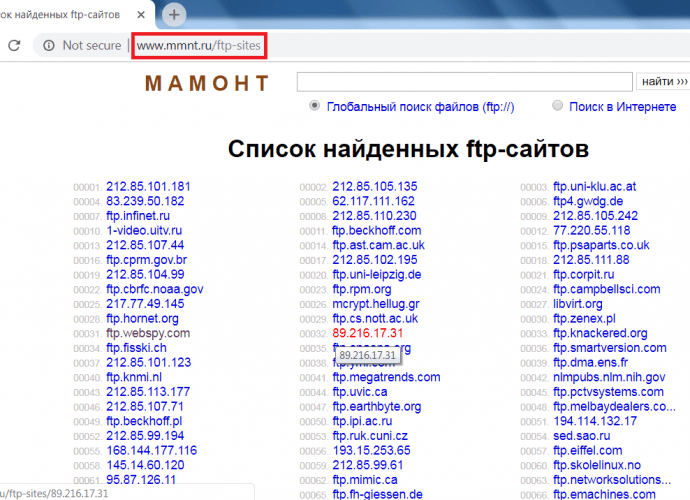
Do Hacking with Simple Python Script
Pentesting is all about showing and reporting problems in web/mobile applications. This is the most popular part of cyber security which every researcher/security enthusiast want to do. Because it givesRead More →