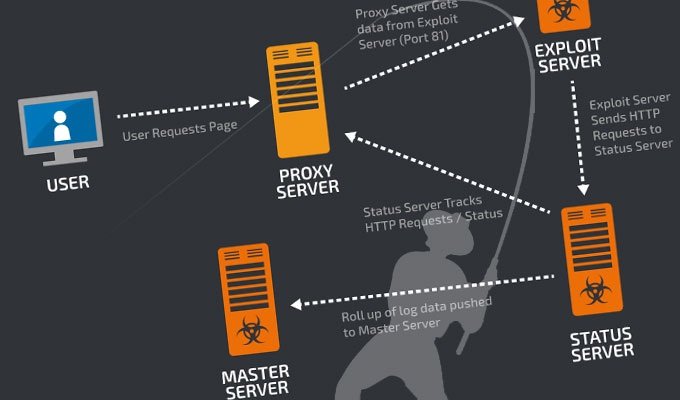
Abusing Windows Management Instrumentation (WMI) to Build a persistent, Asynchronous and Fileless Backdoor
Matt Graeber showed the method on performing WMI attacks and its effects, but he didn’t talk much about the details. Therefore, this paper mainly details about using powershell to implementRead More →