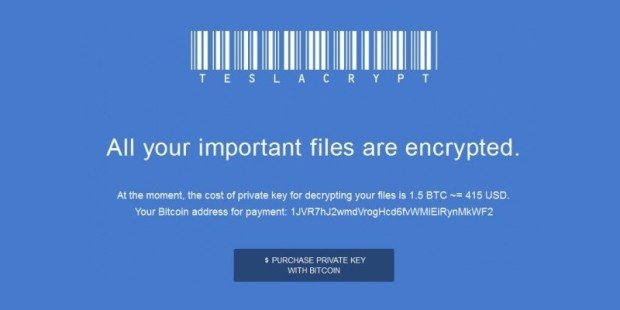
TeslaCrypt Decrypted: Flaw in TeslaCrypt allows Victim’s to Recover their Files
For a little over a month, researchers and previous victims have been quietly helping TeslaCrypt victims get their files back using a flaw in the TeslaCrypt’s encryption key storage algorithm. The information thatRead More →