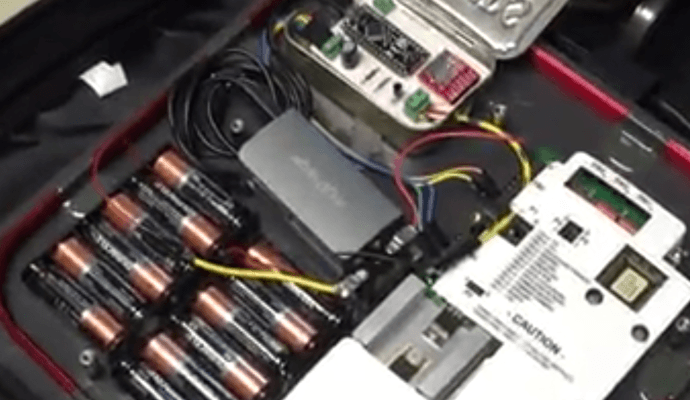
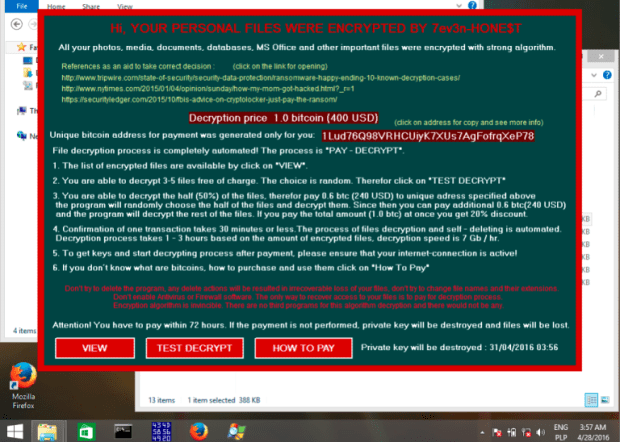
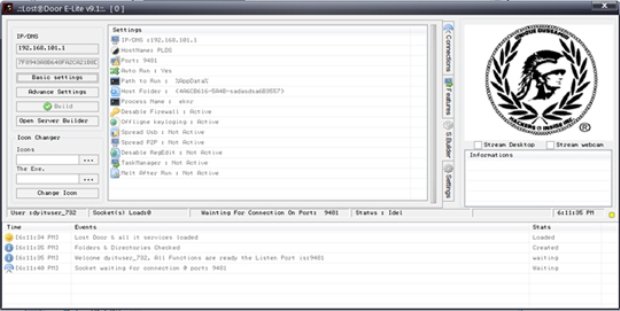
Hackers can break into a facility by spending $700 on Amazon or eBay
Hackers demonstrated to the Tech Insider how to break into any office by purchasing from Amazon and eBay $700 worth of electronic parts to clone access cards. Breaking into aRead More →