While helping a large organization with improving their overall security posture, I came across an interesting endpoint which I have never come across before. It immediately sparked my interest. The branding exposed the company and the product in its login page.

The login page itself gave away a good amount of information. Different people are wired differently, a hacker is no different, we have a profile in which drives our actions. A hacker’s immediately next step (like reflex) is to take the information to get more information. Immediately, I turn to everybody’s friend, Google.
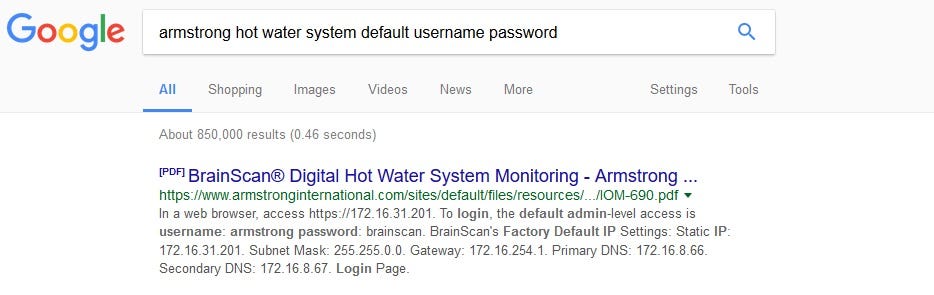
Yes, most people laugh at default password when they hear it on the news. You probably saying to yourself as you are reading this there is 0 chance this will work. I am not here to judge, I am here to test and let the result tell me what to do and drive my next steps.
I was lucky there was a pdf document published on the company’s website so I took that information and tried it without knowing what’s going to happen.
To my surprise, it did work. Well, not that surprsied if you put yourself in the shoes of the company. The person who was setting this up, his/her goal was to make this system work. He/she followed the documentation and got it to work, securing it was probably not on top of mind.
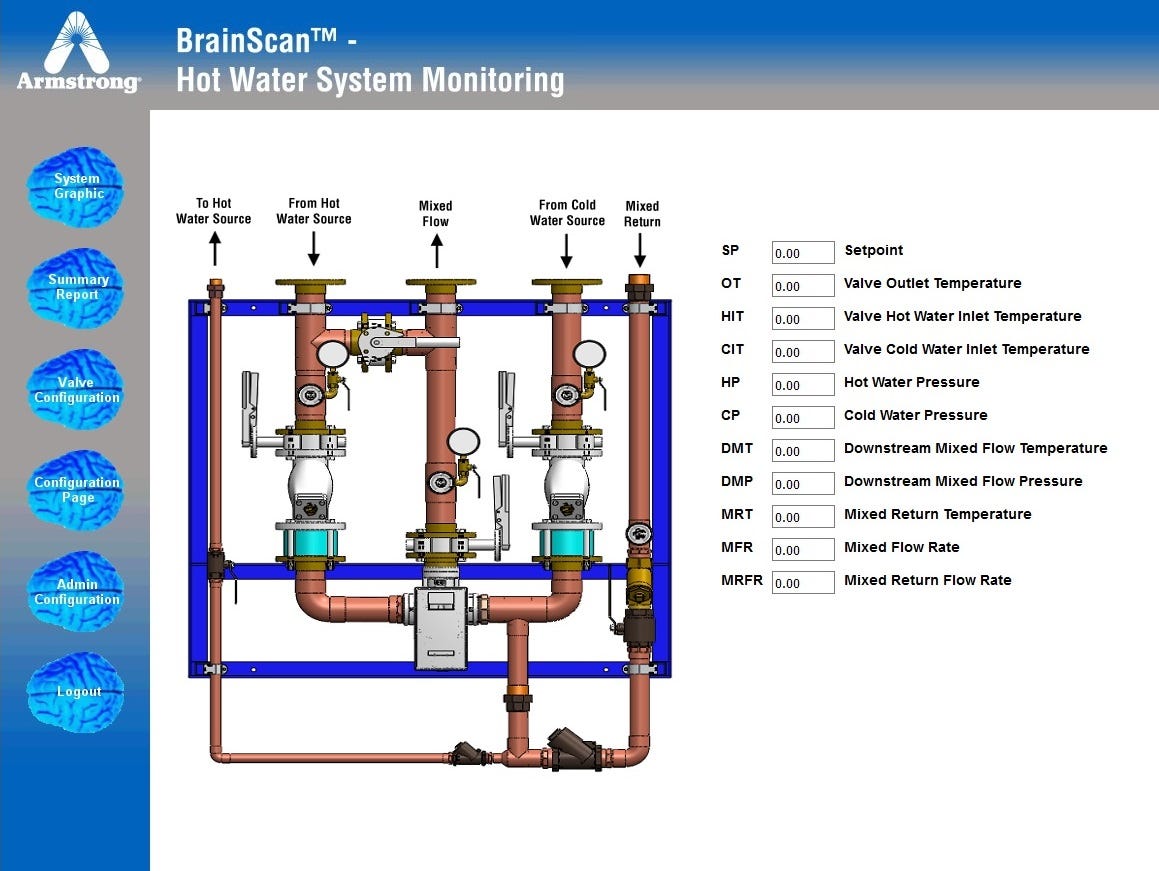
Once I got access into the system, I was like a kid in a candy store. Everything is new to me and everything is interesting! I want to try everything, adrenaline rushing but first had to remind myself I am a whitehat. It’s important to explore and learn but not touch!
Whitehats simply won’t get the glory but I get to talk about it and share my experience and spread good for the next generation of whitehat hackers.
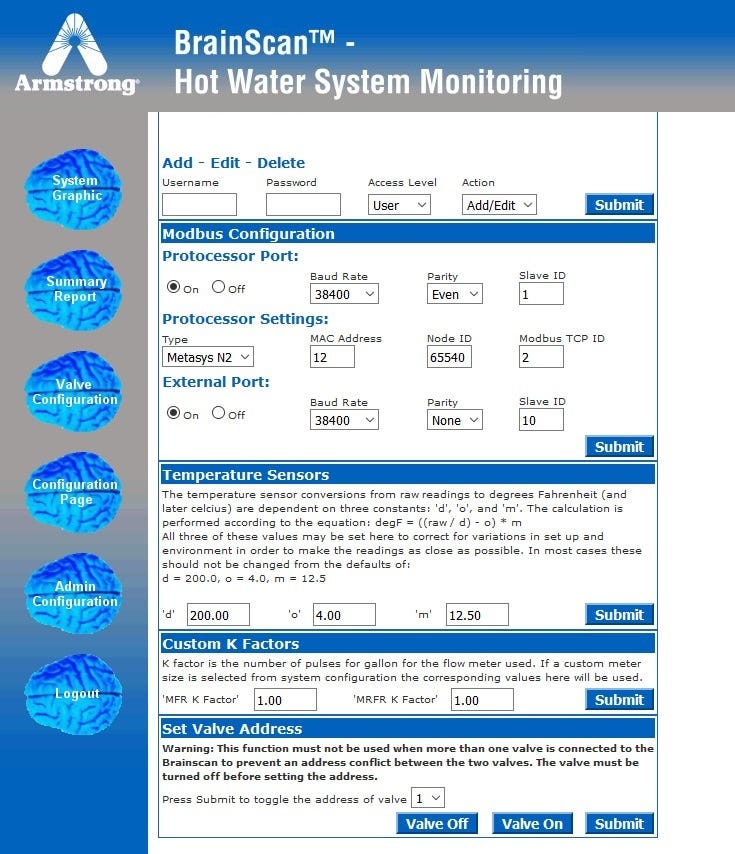
As I explore, I can see all the features of this product and while most people see it from a functional perspective, I have to to temporarily put on the black hat to imagine a scenario where someone can take advantage of this issue and to understand the impact of this issue.
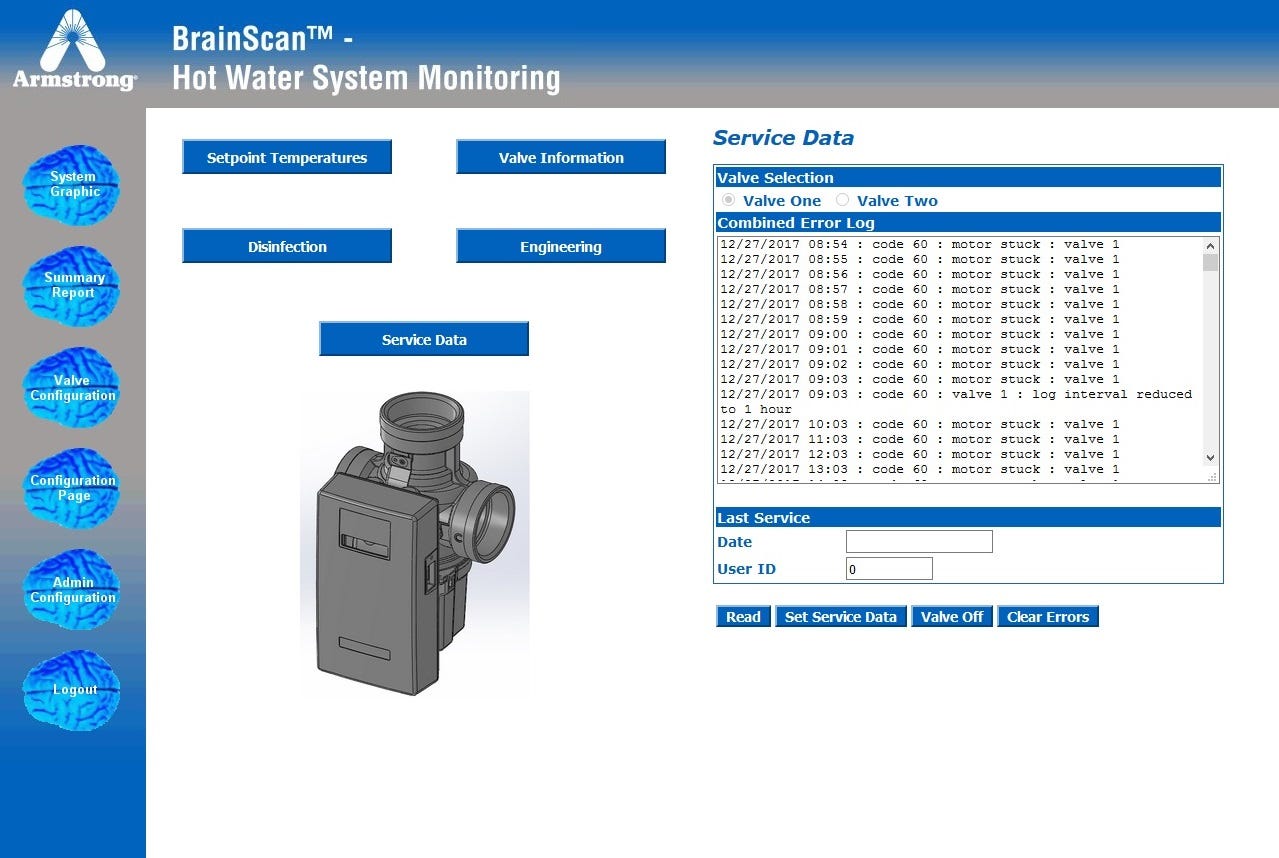
Set temperatures, change flow rate, run disinfection, open/close valves..
I am no water pressure expert but I am sure there is a right way of setting this up and a very very wrong way of setting this up. If I was a malicious, first things first. Change the administrative password to lock out the company, later I’d imagine that setting the hot water pressure to be maxed and max water flow and max temperature may potentially be dangerous. (especially over a long period of time and with no way to change it back after being locked out)
There are configuration recommendations on there, and special call outs to what not to do. Of course, like robots.txt, those are the things that immediately gets our attention.
To make sure the dreamed up scenarios does not ever happen, I immediately disclosed this information to the organization and make sure they take recommended remediation steps to secure this system.
This reminded me a little about the mr. robot show in season two relating to the UPS. Did I just save the lives of many people that live or work in or near this facility? I won’t know but what I do know is that the company is safer with this vulnerability closed and that I made it happen. To me, that’s a good day’s work, my work is impactful and that helps me when I go home and face my family.
source:https://medium.com/@tbmnull/how-hackers-can-save-lives-5c9cd6f62b74

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











