For almost two years, hackers could have easily stolen your prized stash of bitcoins if you were keeping them in the popular software wallet Electrum, thanks to a critical security vulnerability that went unpatched until now.
The vulnerability allowed any website (and anyone controlling the site a victim browsed, like a hacker) to steal bitcoins stored using Electrum, as long as the software was running and there was no encryption password set up, according to security researchers. The bug was initially reported by Github user “jsmad” on November 24, 2017. Electrum, however, didn’t fully patch the bug until Sunday, January 7, and only after Google security researcher alerted them to how serious the bug really was.
“The bitcoin wallet Electrum allows any website to steal your Bitcoins,” Ormandy tweeted on Saturday. “I was gonna report it… but there was already an open issue from last year. I pointed out this is kinda critical, and they made a new release within a few hours.”
Mustafa Al-Bassam, a postgraduate researcher at University College London, told me over Twitter that the hackers could have exploited the bug since February 2016, almost two years ago, when developers released Electrum 2.6.
“[The bug] allows any malicious website to control your Electrum wallet, including stealing all your Bitcoin if the wallet isn’t encrypted with a password,” Al-Bassam told me via Twitter direct message. Even if the wallet does have a password, he explained, a hacker could still redirect bitcoins from the wallet to their address.
An initial patch for the bug was released on Saturday, but confusion ensued as the patch didn’t actually fix the whole issue, according to Electrum itself. The company said on Twitter that its initial patch (3.0.4) “did not completely address the vulnerability.” The final patch only came later, on Sunday.
Electrum’s founder, Thomas Voegtlin, explained over email that the company didn’t realize how critical the bug was back in November, because even the researcher who made the initial report didn’t know. “That is why we did not consider the initial bug report as critically urgent,” Voegtlin told me in an email.
“When a zero day exploit is made public, it is important to address the vulnerability as soon as possible, because attackers are going to use the exploit,” Voegtlin wrote me in an email. “This is why we released 3.0.4 immediately, before password protection was ready.”
For some, however, Electrum’s slow turnaround in patching the vulnerability is bound to bring up bad memories. Last year, millions of dollars worth of Ethereum’s cryptocurrency was locked up forever, allegedly by accident, thanks to a bug that was known to the wallet developers but left unaddressed for months.
The Electrum bug is now fully patched, but there’s a chance hackers could still take advantage of it, if users haven’t updated their software. Electrum doesn’t automatically update, so many victims might be vulnerable unless they proactively check and apply the patch, according to Al-Bassam.
“I think this bug will be exploited for a while, since Electrum doesn’t have a built-in upgrade mechanism on Windows and Linux,” he added. Twitter user “h43z” showed how the bug can be easily exploited in a short proof-of-concept video showing a bare-bones site they developed to attack their own wallet.
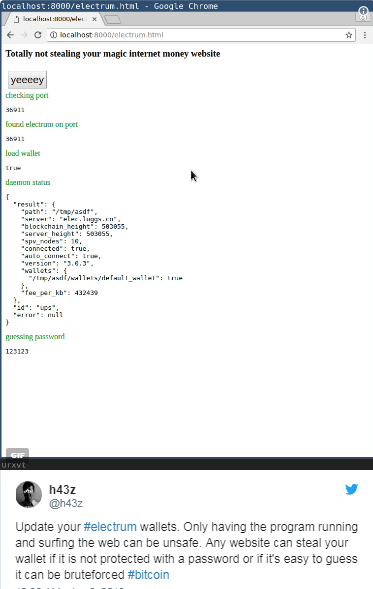
The vulnerability was in Electrum’s JSON-RPC interface, which wasn’t properly secured. JSON-RPC is a simple protocol that allows data and other code to be exchanged between clients and servers, which is also used by several other digital wallets or software, such as wallets for Ethereum, a competing cryptocurrency.
It’s unclear if Electrum’s JSON-RPC vulnerability, specifically, was ever actually exploited by hackers. But in recent months, security researcher Dimitrios Slamarisand others noticed that criminal hackers have tried to find vulnerable Ethereum wallets by scanning the internet for JSON-RPC interfaces exposed on the internet. This interface, as Bleeping Computer reported, should in theory be only exposed locally, but if it is exposed to the wider internet then it can be used to steal cryptocurrency.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











