On Monday, US authorities announced the arrest of a suspect who used Tor to disguise his online identity and coerce underage female victims into sending sexually explicit images and videos in a tactic commonly referred to as “sextortion.”
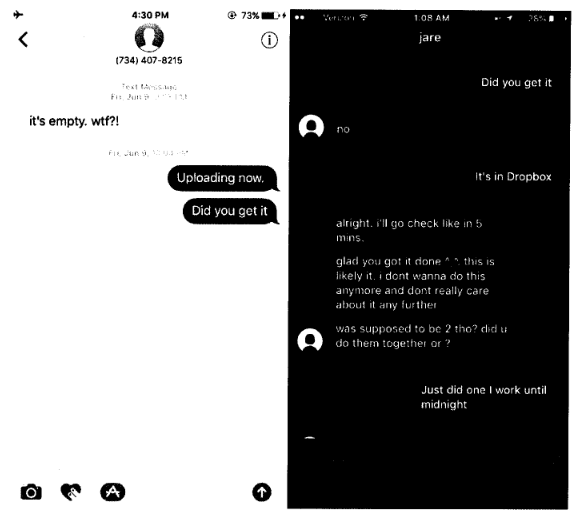
According to court documents, the FBI managed to catch the suspect in June 2017 after it created and deployed a custom NIT (Network Investigative Technique) that relied on appending de-anonymizing code inside a video file.
Booby-trapped video leads FBI to California home
FBI agents hosted the file on a Dropbox account shared by the sextortionist and one of his victims, and when the suspect downloaded and opened the file, the code within called back to FBI servers, exposing the alleged crook’s real IP address.
The IP address led agents back to a Bakersfield, California home, where with a judge’s approval they set up video surveillance and used a pen-trap device to intercept the Internet traffic coming and going from the suspect’s home.
Following weeks of watching the home and the couple living there, agents discovered that whenever the female resident would leave for work, the male resident would connect to the Tor network and carry out covert communications.
Suspect’s sextortion activity goes back to 2012
This and other evidence allowed the FBI to conclude they correctly tracked down the main suspect of a series of sextortion cases that have been going on since 2012, but of which the FBI became aware in December 2015, when one of the victims came forward.
According to court documents, the main suspect is a 26-year-old man named Buster Hernandez. The FBI claims he used a fake online identity named Brian Kil (and others) to reach out to underage girls, some as young as 9 and 12.
The suspect would ask if victims were aware that strangers viewed photos of their naked body. If victims replied affirmatively, the FBI says Hernandez would threaten the victims to send the photos to friends and relatives if they didn’t send him new sexually explicit photos and/or videos.
Hernandez allegedly went as far as to threaten sextorted victims with physical violence or with murder. Other messages obtained by the FBI hint that Hernandez — under the Brian Kil persona — made bomb threats and threatened to kill police officers. The threats led authorities to close down two high schools and one shopping center.
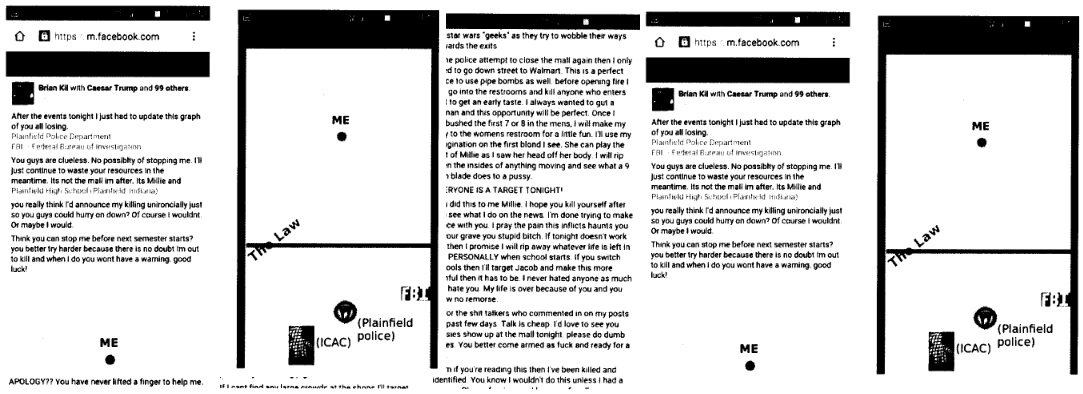
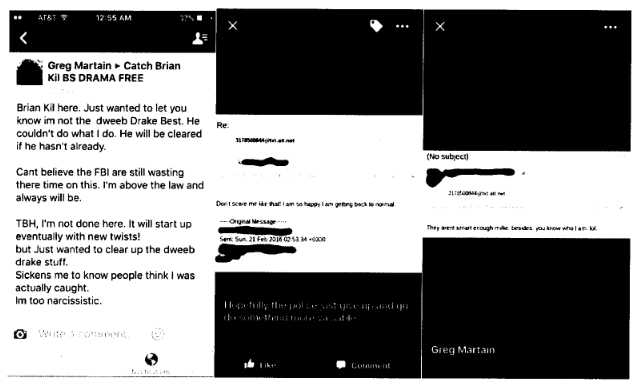
Investigators also claim that Hernandez, under another persona, also made fun of investigators for not being able to catch him.
Facebook also helped with the investigation. Below is an image of an undercover FBI agent posing as one of the victims and supplying the booby-trapped video to the Brian Kil persona.
Arrested suspect faces between 15 and 30 years imprisonment
Investigators arrested the suspect earlier this month, and on Monday, they charged him with threats to use an explosive device, threats to injure and sexual exploitation of a child, cyber threats to female victims, and producing child pornography.
If found guilty and convicted, Hernandez faces a sentence ranging from 15 to 30 years in prison.
The official court documents only include details from three sextorted victims, but investigators believe Hernandez is behind sextortion cases in as many as ten different federal districts. The FBI is also asking other Brian Kil sextortion victims to step forward, reach out, and file a report.
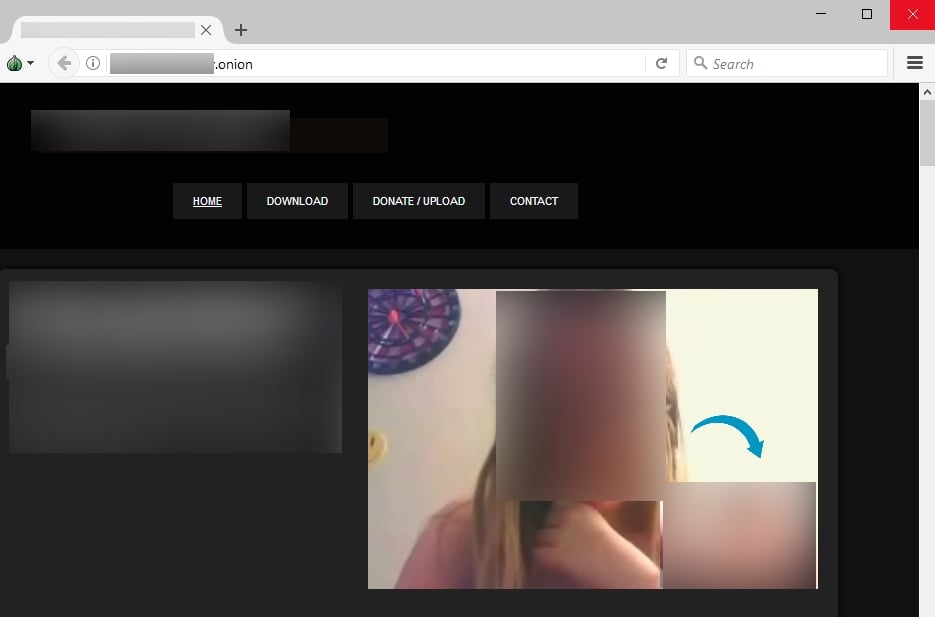
In some cases, sextortionists keep the materials they obtain from victims for themselves, but in some cases, some of these images and videos end up on 4chan, Imgur, or specialized Dark Web portals that sell the files for profit. It is unclear what Hernandez did with the materials he obtained.
Source:https://www.bleepingcomputer.com/news/security/fbi-used-booby-trapped-video-to-catch-suspected-sextortionist-hiding-behind-tor/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











