Hackers are hiding hundreds or thousands of username/password combinations in one single XML-RPC request. WordPress sites are being abused once again and there is no surprise since the platform is the most popular CMS on the Internet, and the attack surface is literally enormous when compared to other website-building solutions.
This time around, Sucuri’s security researchers have identified a variation on the classic brute-force attack which uses WordPress’ built-in XML-RPC feature to crack down admin/password credentials.
XML-RPC, one of the simplest protocols for exchanging information between computers across the Internet, has been used before in WordPress brute-force attacks. Actually, the protocol has been plagued by security holes in the past, for a long time being disabled by default, and being activated only after the release of WordPress 3.5.
Attackers found a way to amplify their brute-force attacks
This time around, though, the attackers found a method through which to amplify their attacks many times over, allowing them to go undetected by normal brute-force mitigation products or locally hosted solutions.
To better understand, a simple explanation of how brute-force attacks work in WordPress is needed.
When a hacker wants to break a user’s account, he tries thousands of username/password combinations via the login page. Each of his attempts is logged and can then be used to ban IPs or user agent strings.
While this attack is usually performed via HTTP/HTTPS, it can also be carried out via XML-RPC. This time around, as Sucuri explains, the attackers used the XML-RPC protocol in conjunction with the protocol’s system.multicall method to hide themselves.
Because the system.multicall method allows developers to send multiple instructions via XML-RPC, attackers have been bundling together hundreds and thousands of username/password combinations that they wanted to check in one single XML-RPC call.
This meant that by sending a few XML-RPC requests at larger intervals of time so firewalls and brute-force protection systems won’t be triggered (usually a few failed authentication requests per hour), attackers would have been able to test tens of hundreds of thousands of credentials per day, without being detected.
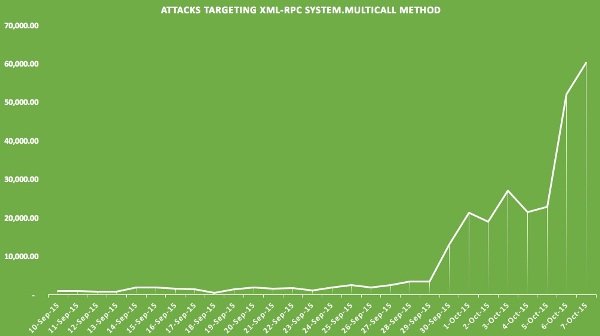
Sucuri saw the first attack of this type on September 10, which steadily increased along time until September 29 when it sky-rocketed to around 60,000 per day on October 7.
How to prevent amplified brute-force via XML-RPC
Sucuri’s team provided some advice on how to block these types of attacks. If you’re not using plugins that use the xmlrpc.php file, you can simply go on ahead and rename/delete it, so it won’t be referenced anymore.
If this feature is used by plugins (like JetPack, for example) and blocking, it would result in some broken functionality on your site, webmasters could block XML-RPC system.multicall requests via a Web firewall. A good option would be Sucuri’s products since they’ve already been upgraded to protect their clients from this threat.
This is also the perfect article in which we can mention that Sucuri had previously launched a public dashboard where WordPress administrators could track worldwide brute-force attack trends.
Source:https://news.softpedia.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











