A new tool is making the rounds on the criminal underground. Called Katyusha Scanner, this is a hybrid between a classic SQL injection (SQLi) vulnerability scanner and Anarchi Scanner, an open-source penetration testing tool.
Discovered by security researchers from Recorded Future on an underground hacking forum, the tool was put together by a Russian-speaking criminal and is meant to be installed on a web server, but also uses a Telegram channel to manage its interface, in addition to a classic web-based administration panel.
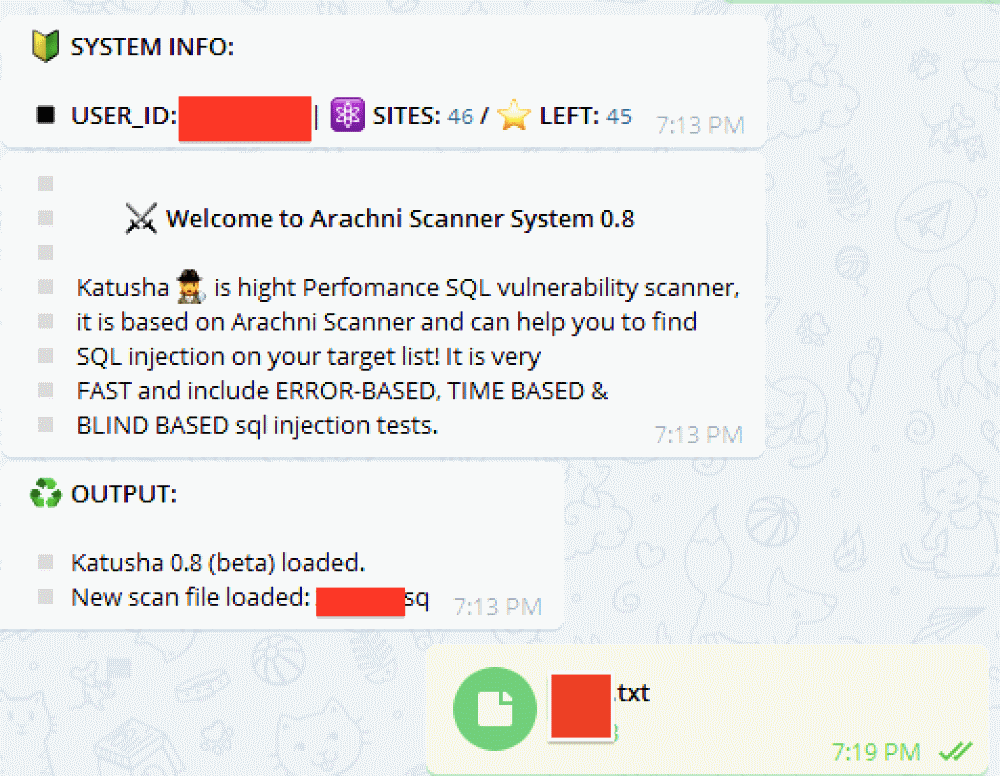
The benefit of this design choice is that Katyusha customers can access the tool from their mobile phones, just by connecting to the Telegram channel they set up during installation, and run commands to start SQLi scans or deploy web shells on sites found to be vulnerable.
Tool available for download or as a hosted service
Launched in April, the tool has become very popular, despite its high price of $500 for a one-time purchase. Because of the tool’s high demand, a month later, in May, Katyusha’s author released a “light version” for only $250 for crooks who couldn’t afford to pay for the full package.
The tool’s immense popularity was proven again in June when Katyusha’s author expanded his operation with the launch of a service where wannabe hackers can rent access to a hosted version of Katyusha for only $200 per month.
 |
 |
 |
 |
Recorded Future expert Andrei Barysevich says the tool’s success is driven by the customer support the tool’s author provides to customers, but also by the Katyusha’s large set of features.
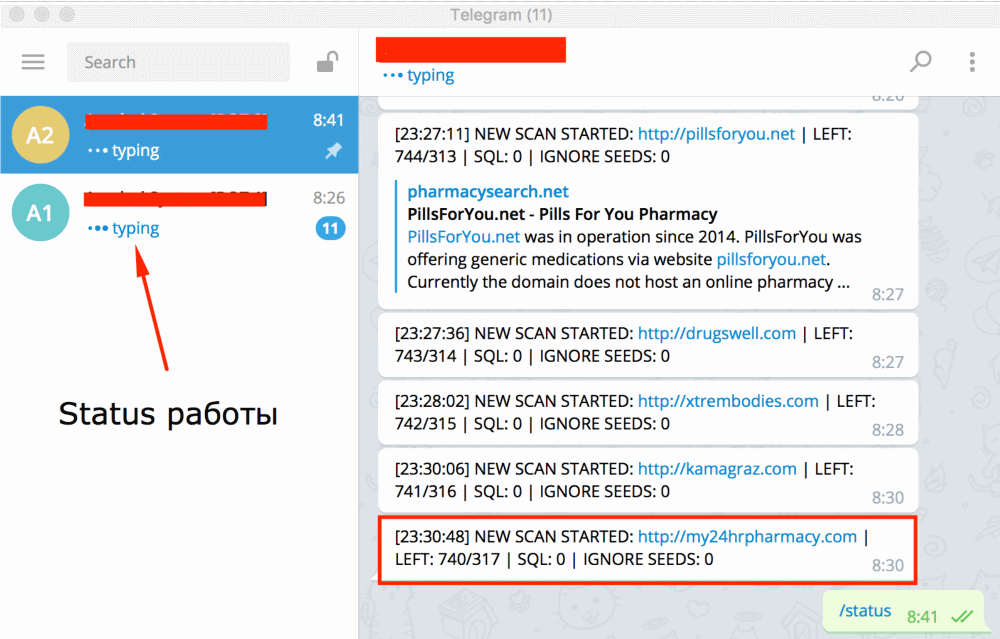
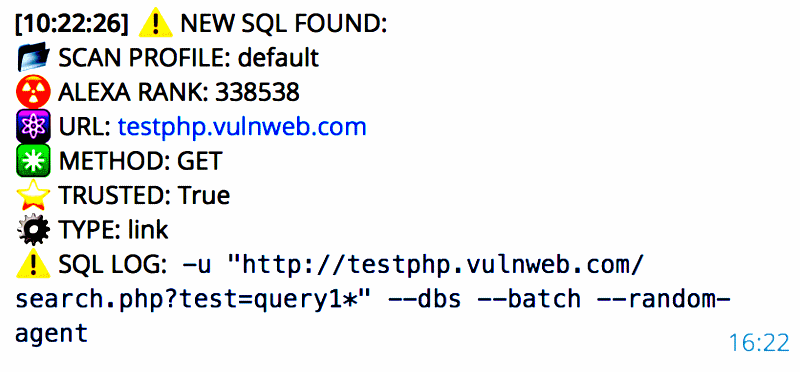
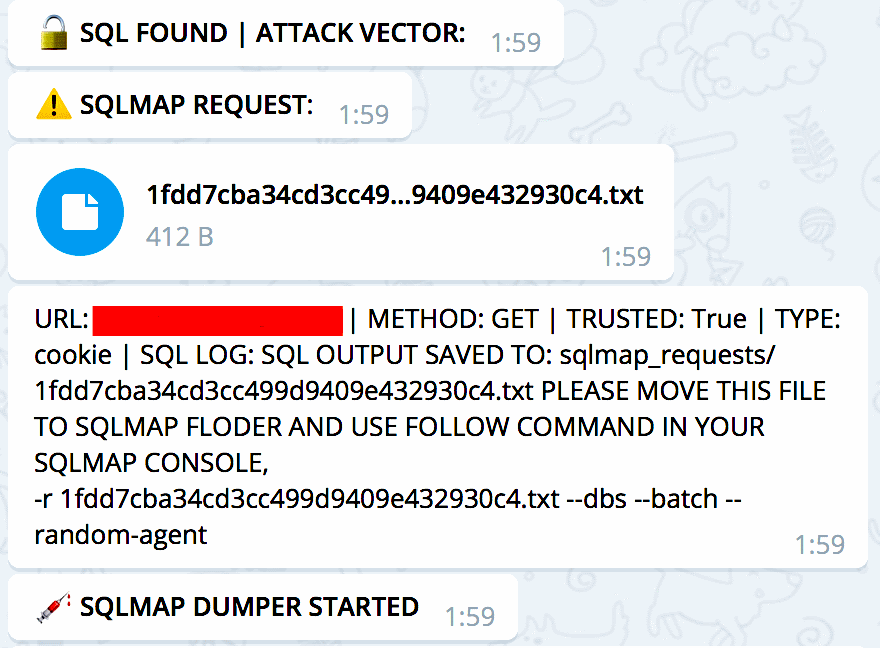
For example, buyers can feed a list of websites and Katyusha will go through each one and attempt to scan for various types of SQLi attacks. Once a site is detected, the tool can exploit the flaw, deliver a web shell, upload other types of files, or dump databases automatically.
Furthermore, Katyusha can also be used for login credentials brute-force attacks and supports a wide range of database systems. Below is a copy of one of the Katyusha ads, currently found in several hacking forums.
Product Specifications:
Search and export of email/password credentials
Module framework
Multi-threaded and support of concurrent sessions
Telegram messenger interface
Web interface
Automatic dumping of databases
SQLMAP reports
File upload (the list of targeted websites)
Linux/Windows support
Web Shell Module Specifications:
CMS family identification (Bitrix, WordPress, OpenCart, etc.)
Login credentials brute-forcing (concurrent with SQLi scan)
Automatic web shell upload
Scanning Options:
SQL injection (sql_injection) — Error-based detection
Oracle
InterBase
PostgreSQL
MySQL
MSSQL
EMC
SQLite
DB2
Informix
Firebird
SaP Max DB
Sybase
Frontbase
Ingres
HSQLDB
MS Access
Blind SQL injection using differential analysis (sql_injection_differential)
Blind SQL injection using timing attacks (sql_injection_timing)
MySQL
PostgreSQL
MSSQL
While there are various ways to protect against SQLi scanners, the easiest solution is to deploy a WAF (Web Application Firewall) to protect your sites from basic exploitation attempts, such as SQLi scans, port scans, or brute-force attacks.
Source:https://www.bleepingcomputer.com/news/security/telegram-based-sql-injection-scanner-available-for-500-on-hacking-forum/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.










