Another major exploit kit (EK) looks like it’s heading for the EK graveyard as activity from the RIG EK has fallen to less than 25% of what the exploit kit used to handle three months ago, in March 2017.
RIG EK’s decline in activity fits a pattern observed on the entire EK market in the past year, as several major and minor exploit kits have shut down.
The list includes Angler, Nuclear, Neutrino, Sundown, Sweet Orange, and Fiesta. If things continue to decline, we may soon add the RIG EK to that list in just a few months.
Browser security has improved, EK development has stalled
There are many reasons why exploit kits are no longer popular. First, browsers are getting harder to hack. Chrome, Firefox, and most recently Edge, have used bug bounty programs to improve the security defenses in their codebases, taking away many of the loopholes EK owners were exploiting to infect users’ computers while navigating the web.
Second, Flash usage is declining. This comes as browsers makers are moving to an “HTML5 by default” policy and shipping Flash disabled for most users.
Third, Internet Explorer usage is also going down, as users move to Windows 10 where Edge is the default browser, or they are abandoning the outdated IE on their own, for newer browsers such as Chrome, Vivaldi, Brave, and others.
The decline of Flash and IE is an important factor why most exploit kits are dying off. Most of today and yesteryear’s EK come with impressive arsenals of Flash and IE exploits and former zero-days.
With the userbases of these two apps going down, exploit kit authors are having a hard time discovering new flaws in modern browsers, which, as said before, have been combed down for vulnerabilities by security researchers, and fixed through bug bounty programs.
A year has passed since an EK featured a zero-day exploit
In addition, cyber-security firm Proofpoint points out that it’s been more than a year since any EK has featured a zero-day exploit, which means that either browsers have become super-secure, or the people behind today’s exploit kits aren’t as talented as the people that ran former EKs such as Angler or Nuclear.
All these factors leave many exploit kits running on an empty tank, with no new exploits and using older flaws. The most obvious example of this is the recent death of the Neutrino exploit kit.
A researcher who says he spoke with the Neutrino author claims the exploit kit became less effective at infecting users and stopped being financially profitable for its author, who decided to shut it down.
Security companies have crippled exploit kit infrastructure
RIG’s recent decline also appears to be related to recent movements in the cybercriminal underground.
Exploit kits, which are nothing more than web apps installed on servers, need someone to send traffic to their main exploitation URL, named a “landing page.”
Crooks who rent the exploit kit can also rent traffic from owners of botnets made up of hacked websites, which redirect traffic to the EK landing page.
According to Brad Duncan, a researcher for Palo Alto Networks, two of the biggest botnets — named “campaigns” — have stopped redirecting traffic to RIG EK.
For example, the EITest campaign has switched to redirecting traffic to websites running tech support scams, as former EK clients realized EK infection rates were going down and decided to switch to new operations. In addition, the pseudo-DarkLeech campaign has shut down for good over the winter.
These actions have resulted in less traffic coming to RIG EK landing pages. Furthermore, an operation mounted by RSA and GoDaddy has also crippled a vast section of RIG EK’s network by removing many of the domains the RIG EK and its “campaigns” were using to infect victims. Similarly, a Cisco operation last year has also crippled many of RIG EK’s traffic funneling operations.
These two actions mounted by security firms have had an impact. Since March, the RIG EK has taken a major blow, losing almost 75% of its traffic, as the chart below clearly shows:
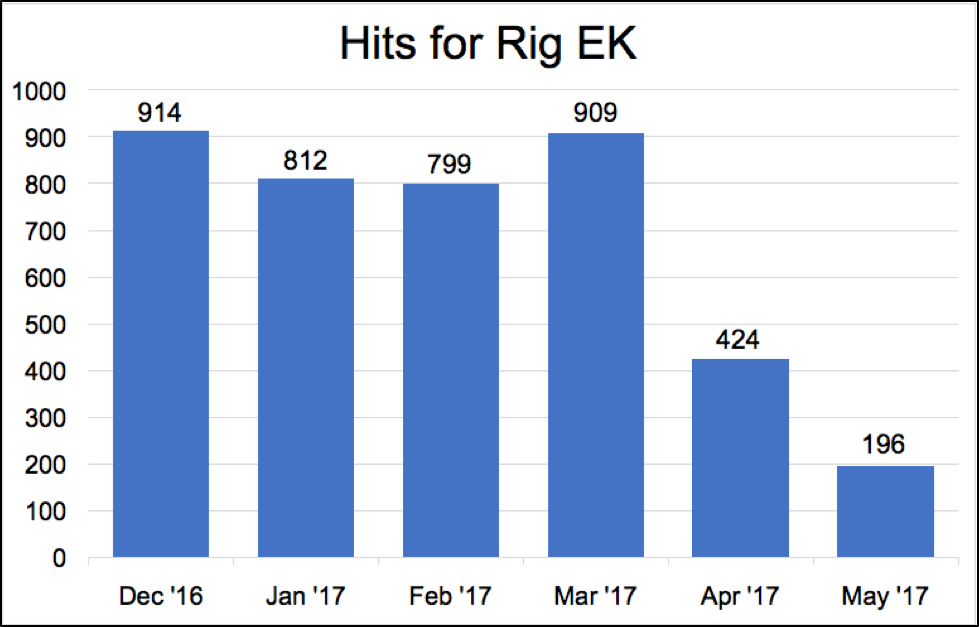
Currently, the RIG EK is still kept alive by campaigns such as RoughTed and Seamless, but Duncan says “recent [RIG activity] levels are their lowest since we began tracking this EK.”
Crooks moving away from exploit kits
The way things are going, we’ll have less than ten active exploit kits by the end of the year, which is good news for most users. According to Kahu Security, the following exploit kits are currently active: RIG EK, GreenFlash-Sundown, Neutrino-v, Magnitude, KaiXin, Astrum, Blaze, Neptune, Eris, and Solar. Outside RIG and Magnitude, most of these are small time players, barely scraping by.
In the future, Duncan, who is an expert in analyzing malicious web traffic and known for his work on MalwareTrafficAnalysis blog, says users have to watch out for social engineering scams.
Duncan expects to see malicious traffic campaigns redirect users to more tech support scams, sites offering fake installers, and social engineering schemes like the ones running the HoeflerText popup scheme.
“EKs are a relatively minor factor in today’s threat landscape compared to social engineering schemes and malspam,” Duncan says. “Users who follow best security practices are much less likely to be affected by the EK threat [today].”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











