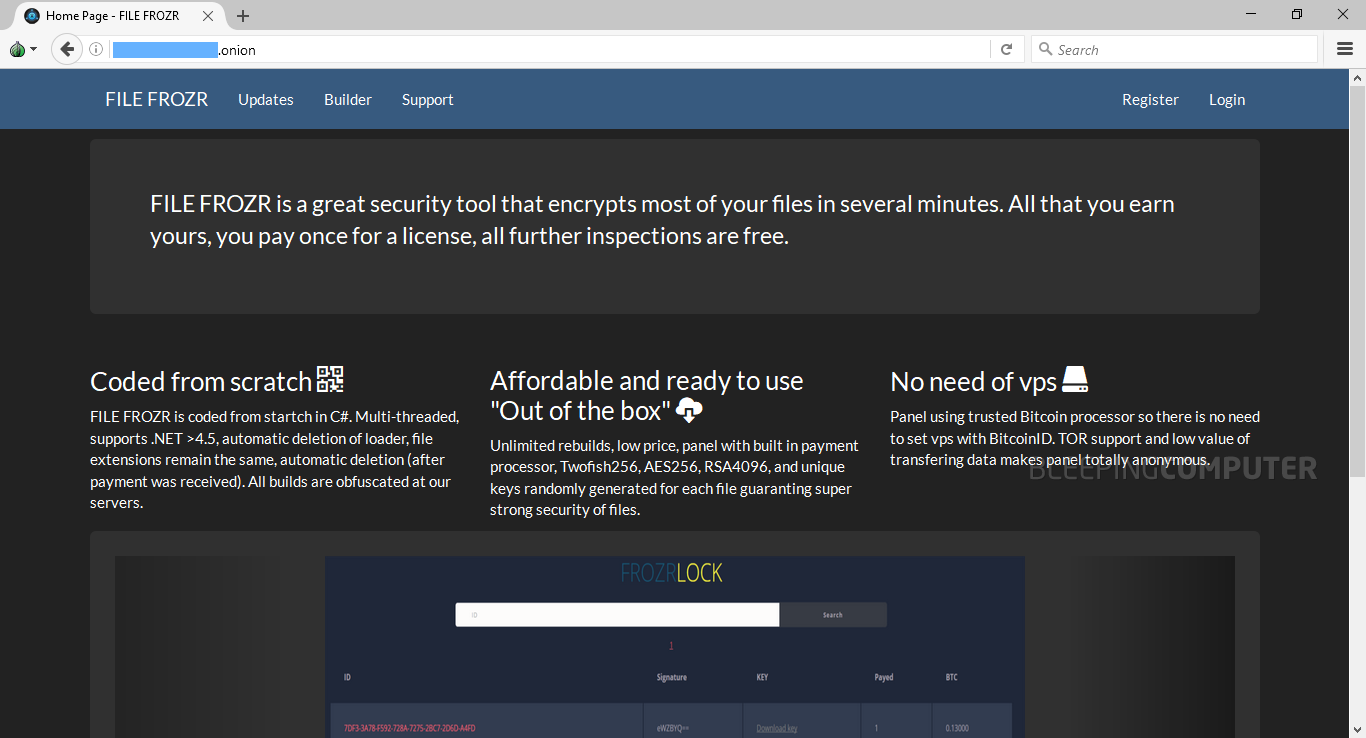
A new Ransomware-as-a-Service has become available on the Dark Web, named FrozrLock, available for only $220, and advertised under the tagline of “great security tool that encrypts most of your files in several minutes.”
Bleeping Computer received a tip about FrozrLock’s existence from security researcher David Montenegro, and with help from Avast security researcher Jakub Kroustek, we were later able to tie it to previous ransomware infections as early as April 16.
“First detections were from Russia, without making any conclusions about its origin,” Kroustek said in a private conversation. “[It was] spreading via JS downloaders named as Contract_432732593256.js,” he said.
At the time, the ransomware had no name, but we called it AutoDecrypt in the Weekly Ransomware round-up of that week, based on the name of its decrypter.
In the meantime, more details have surfaced. Below is the homepage of the FrozrLock RaaS in full.
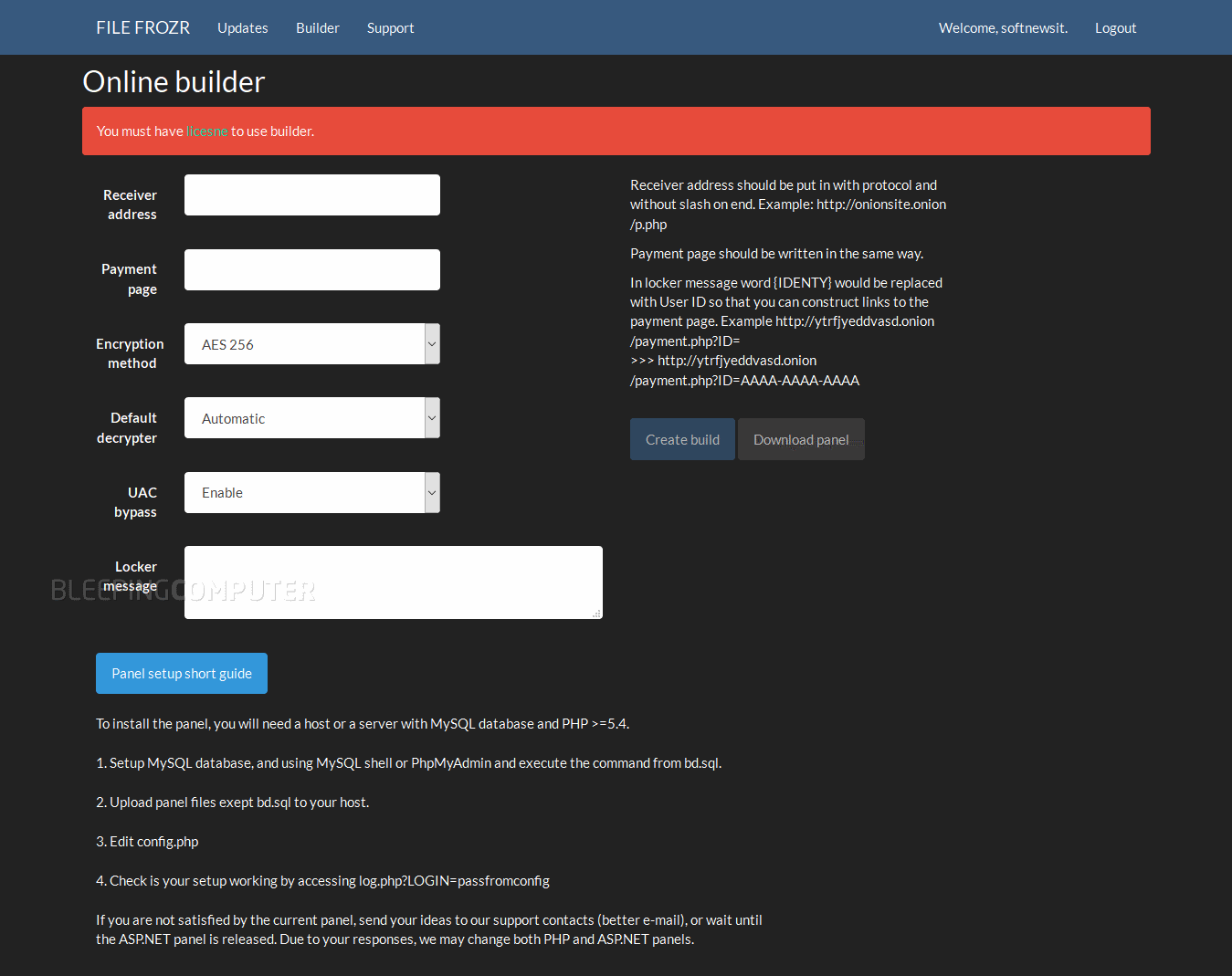
Based on the details listed on the homepage, we extracted the following FrozrLock features (not confirmed):
Multi-threaded
Supports .NET > 4.5
Automatically deletes loader after infecting victim
Doesn’t alter file extensions
Self-deletes after payment was received
All ransomware builds are obfuscated on the RaaS server and offered for download to customers
Tor-based control panel
Customers get unlimited rebuilds
Ransomware uses unique keys for each encrypted file
Can use Twofish256, AES256, and RSA4096 encryption
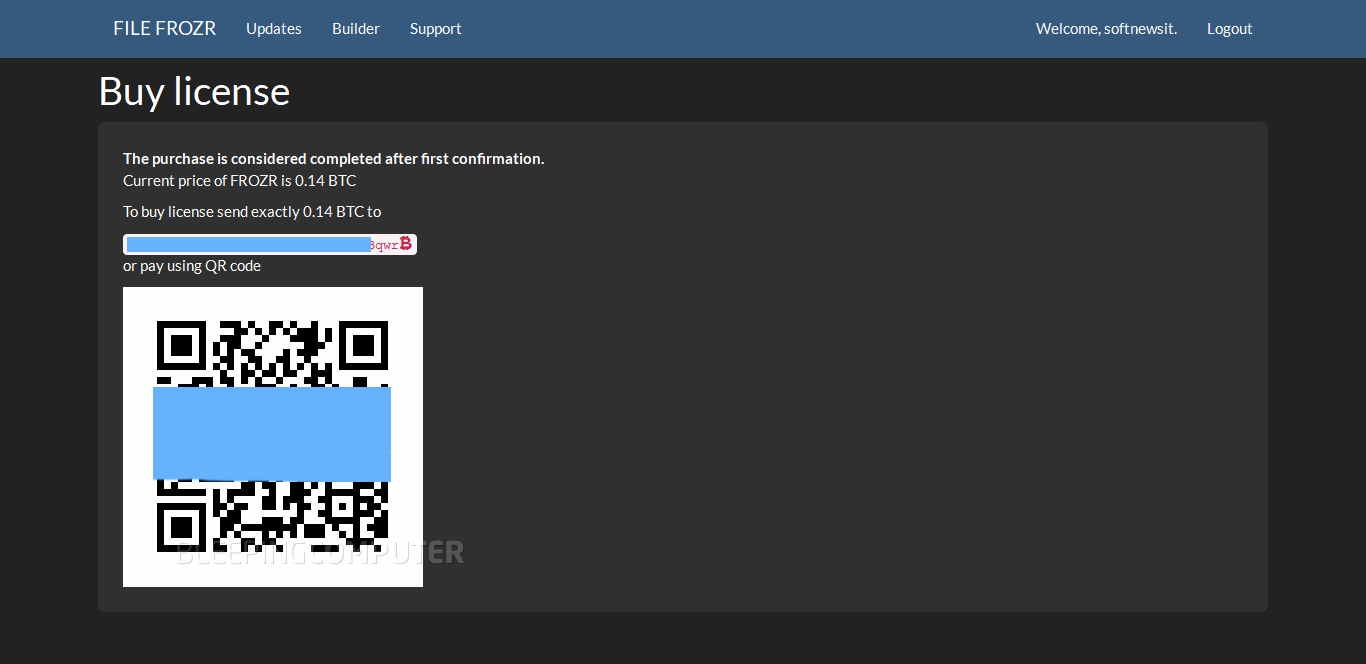
Wannabe crooks that had their interest piqued by this offering must register on the site to gain access to an account. Once they’ve created an account, they’re granted access to the ransomware’s web-based builder interface. To use the builder and produce a fully-working ransomware, clients must buy a license, currently worth 0.14 Bitcoin (around $220).
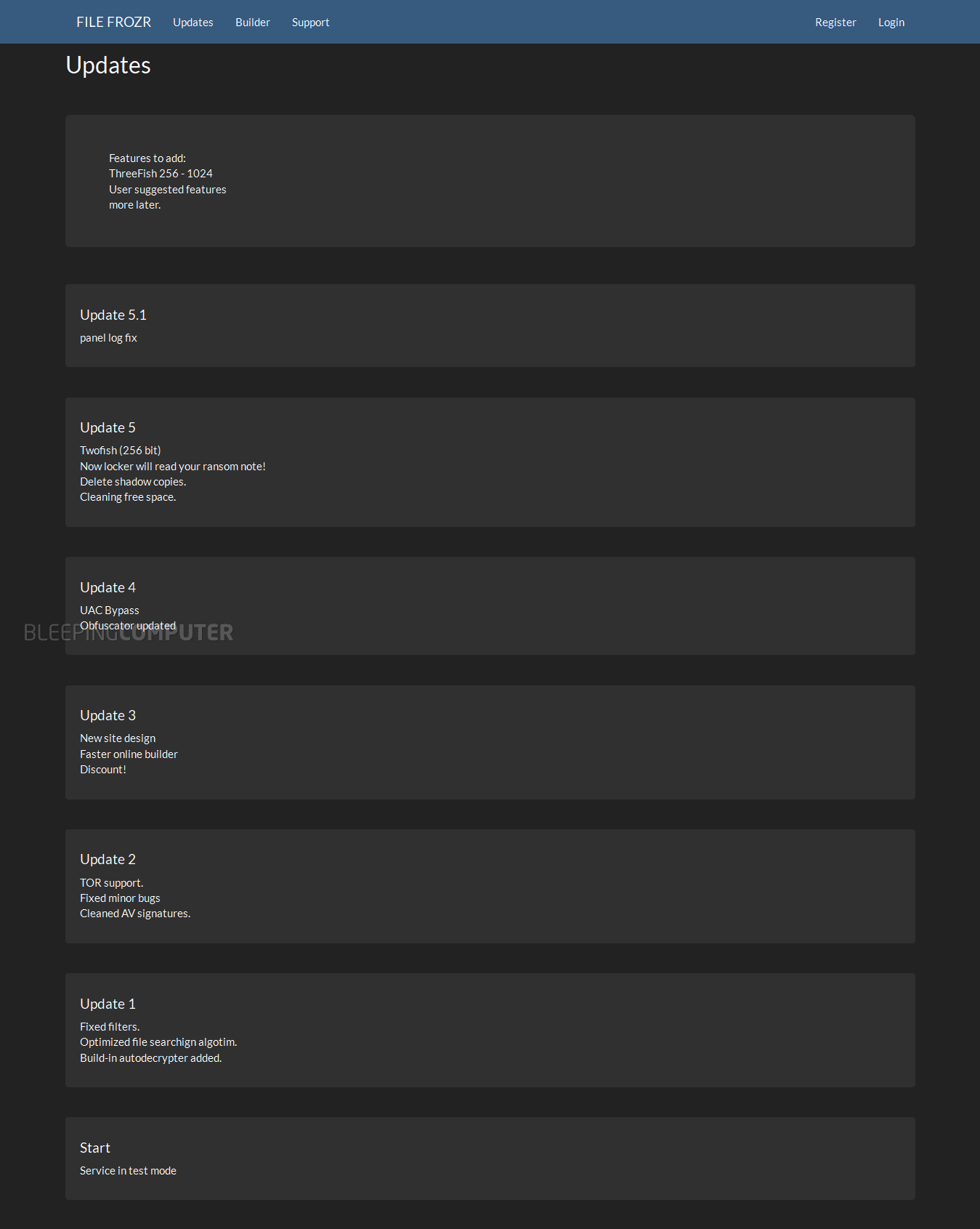
The ransomware’s evolution is also recorded in a professional-looking changelog.
|
|
|
|
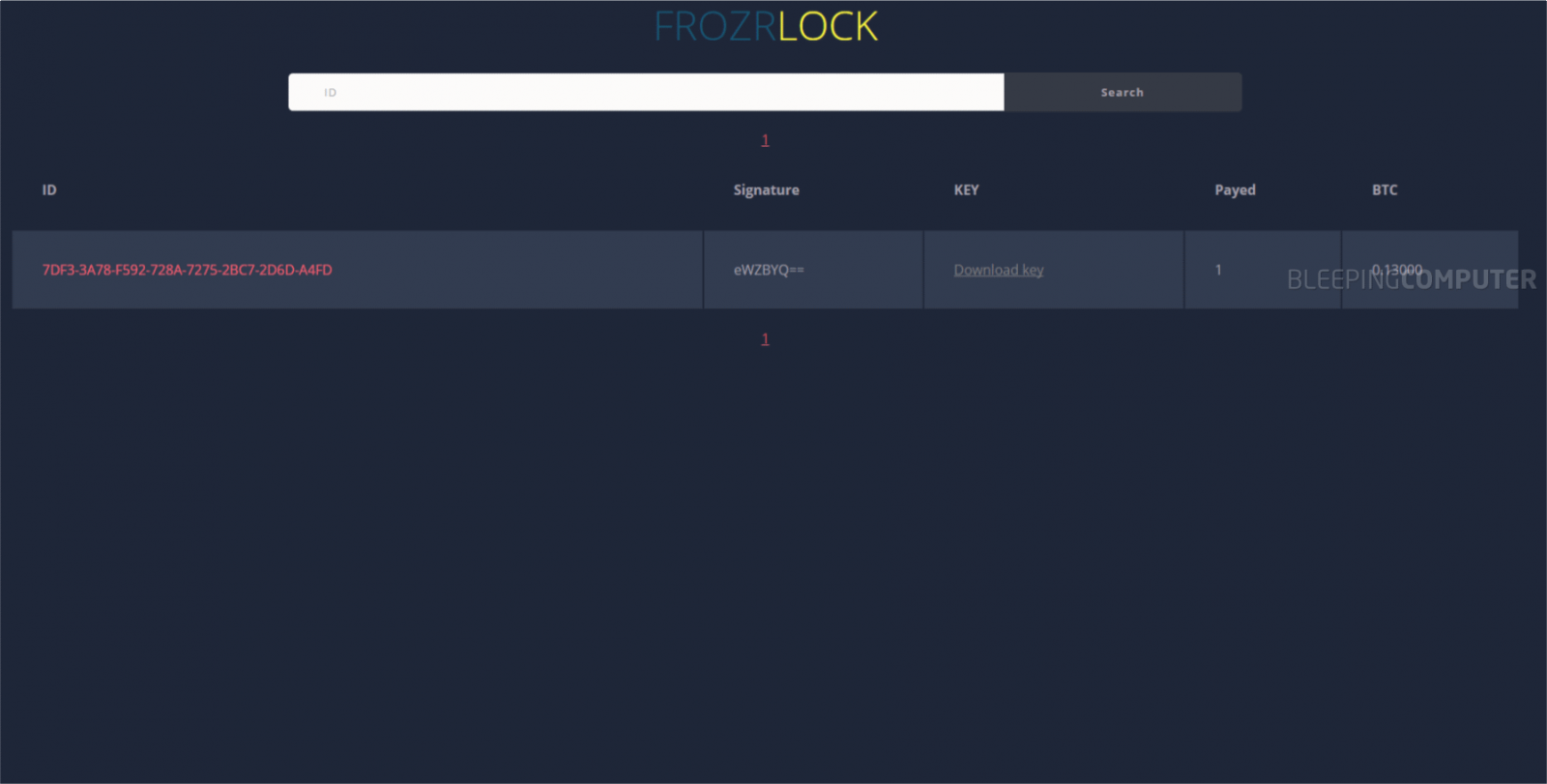
The homepage lists the FILE FROZR name, but once users register and buy a license, the dashboard displays the FrozrLock name instead. Below is an image of the FrozrLock customer dashboard where customers can monitor infections.
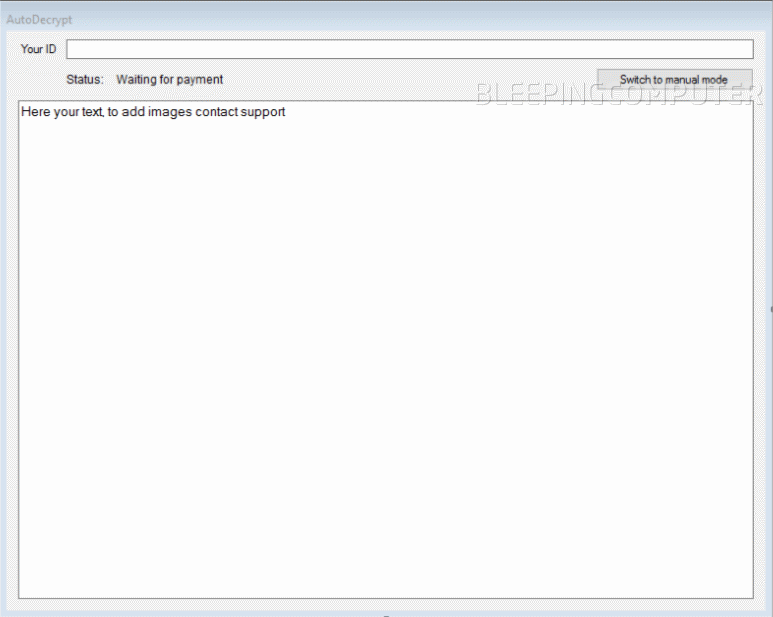
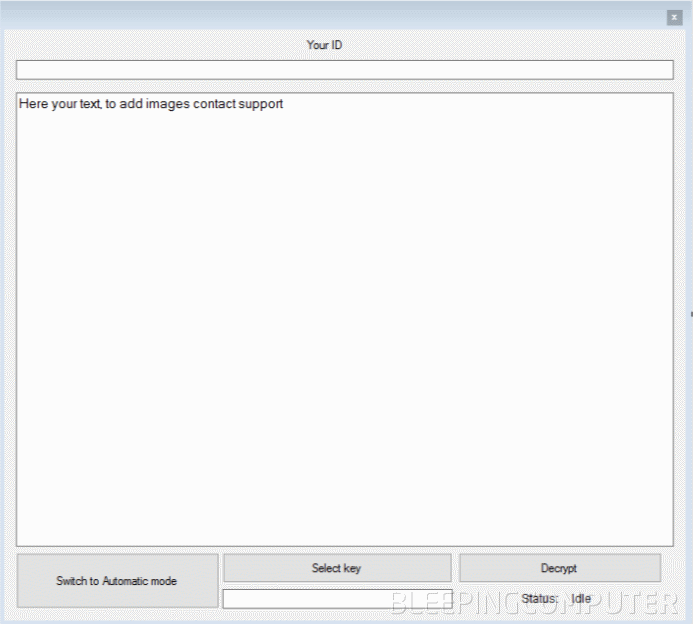
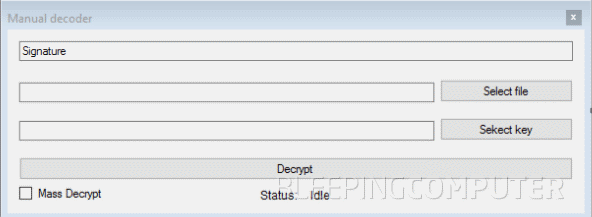
The service also provides customers with a decrypter that they can deliver to paying victims. The decrypter has three operation modes: auto, manual, and an alternate manual.
 |
 |
 |
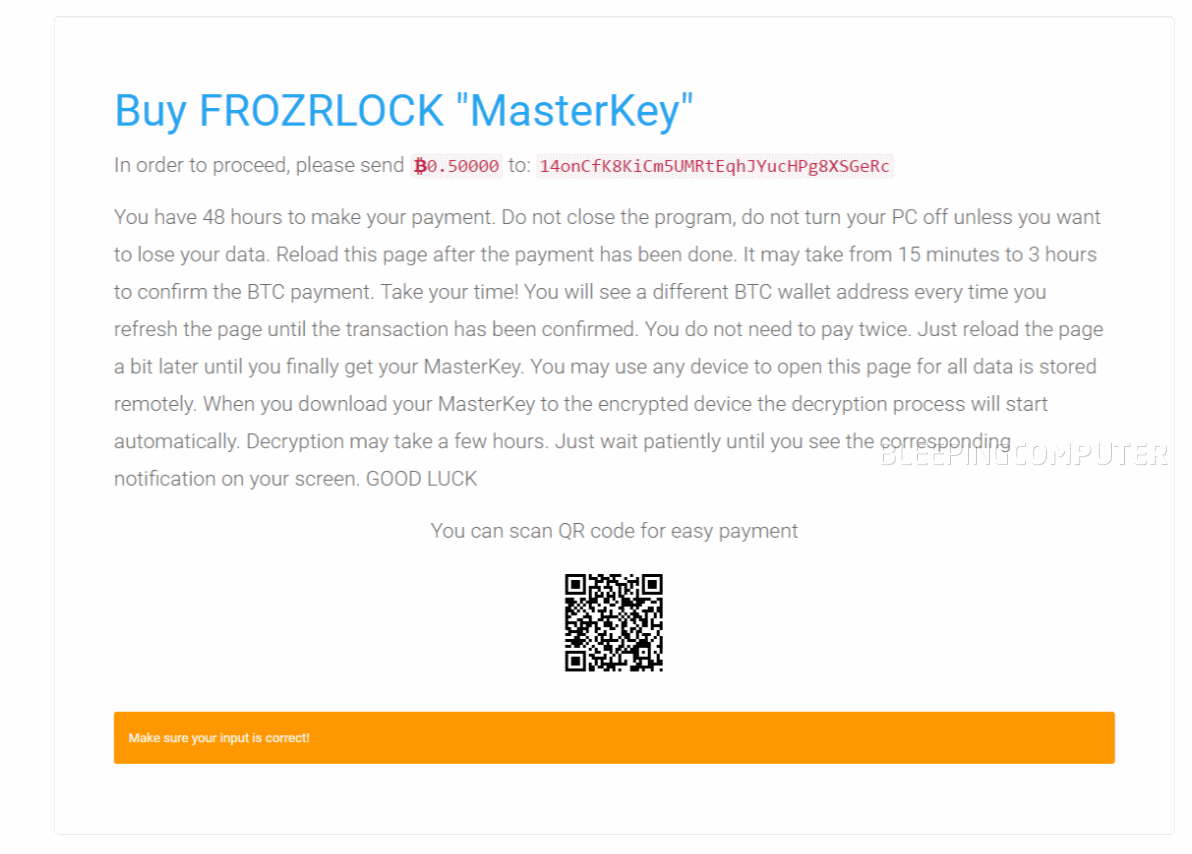
A typical ransom note shown by a FrozrLock ransomware variant looks like the image below.
FrozrLock’s author(s) declined to comment for this article.
SHA256 hash: 2aa4c7708a49a6f1f462f96002dd2ce6fd27c7daf69647162116919b2df5abcd
If you’re a security researcher and you stumble upon a new RaaS or ransomware sample, don’t be shy and reach out via our Twitter account with a tip.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.