Microsoft dismisses DoublePulsar infection estimates, but otherwise remains silent.
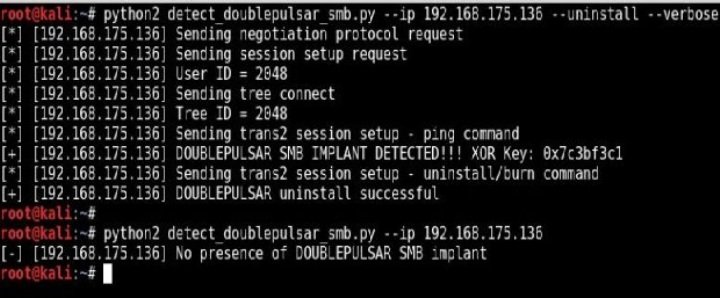
After Microsoft officials dismissed evidence that more than 10,000 Windows machines on the Internet were infected by a highly advanced National Security Agency backdoor, private researchers are stepping in to fill the void. The latest example of this open source self-help came on Tuesday with the release of a tool that can remotely uninstall the DoublePulsar implant.
Both numbers are in the conservative end of widely ranging results from scans independently carried out by other researchers over the past week. On Monday, Rendition Infosec published a blog post saying DoublePulsar infections were on the rise and that company researchers are confident the scan results accurately reflect real-world conditions. Rendition founder Jake Williams told Ars that the number of infected machines is “well over 120k, but that number is a floor.”
On Tuesday, security firm Countercept released an update to the DoublePulsar detection script it published last week. It now allows people anywhere on the Internet to remotely uninstall the implant from any infected machine. Researcher Kevin Beaumont told Ars that detecting DoublePulsar involves sending a series of SMB—short for server message block—queries to Internet-facing computers. By modifying two bytes of the query, the same person can remove the infection from any computers that test positive. The script isn’t the only way to clean compromised devices. As Ars reported last week, the ultra-stealthy DoublePulsar writes no files to the hard drives of computers it infects, a feature that causes it to be removed as soon as the computer restarts.
As Ars reported 11 days ago, DoublePulsar is a weapons-grade implant released by the Shadow Brokers, a mysterious person or group that since August has leaked top-secret documents and software later confirmed to have been stolen from the NSA. In an unusual series of events that have not been explained, Microsoft patched the vulnerabilities DoublePulsar exploits exactly one month prior to its release. The implant provides a stealthy and reliable way for infected machines to communicate with an attacker-controlled command-and-control server.
In a statement issued Tuesday, a Microsoft representative wrote, “Customers with up-to-date software are protected from this malware, which requires an already-compromised machine to run. We encourage customers to practice good computing habits online, including exercising caution when clicking on links to web pages, opening unknown files, or accepting file transfers. For more information on protecting computers against malware, please visit https://aka.ms/bm9atl.”
Of course, a computer that didn’t receive the patch Microsoft released in March could easily be compromised by another zeroday exploit included in the latest Shadow Brokers release.
It’s almost inevitable that people are going to use the updated Countercept script to mass uninstall DoublePulsar from infected computers. Unless people own the compromised machines, such actions are almost certainly subject to criminal or civil legal actions in most jurisdictions. And even then, machines disinfected of DoublePulsar are likely still compromised by other types of malware. Readers should beware. Still, amid the radio silence Microsoft is maintaining, the tool will no doubt prove useful to admins responsible for large fleets of aging computers.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.