Sensors in phones running both iOS and Android reveal all kinds of sensitive info.
Smartphones know an awful lot about us. They know if we’re in a car that’s speeding, and they know when we’re walking, running, or riding in a bus. They know how many calls we make and receive each day and the precise starting and ending time of each one. And of course, they know the personal identification numbers we use to unlock the devices or to log in to sites that are protected by two-factor authentication. Now, researchers have devised an attack that makes it possible for sneaky websites to surreptitiously collect much of that data, often with surprising accuracy.
The demonstrated keylogging attacks are most useful at guessing digits in four-digit PINs, with a 74-percent accuracy the first time it’s entered and a 94-percent chance of success on the third try. The same technique could be used to infer other input, including the lock patterns many Android users rely on to lock their phones, although the accuracy rates would probably be different. The attacks require only that a user open a malicious webpage and enter the characters before closing it. The attack doesn’t require the installation of any malicious apps.
Malicious webpages—or depending on the browser, legitimate sites serving malicious ads or malicious content through HTML-based iframe tags—can mount the attack by using standard JavaScript code that accesses motion and orientation sensors built into virtually all iOS and Android devices. To demonstrate how the attack would work, researchers from Newcastle University in the UK wrote attack code dubbed PINLogger.js. Without any warning or outward sign of what was happening, the JavaScript was able to accurately infer characters being entered into the devices.
“That means whenever you are typing private data on a webpage and this webpage for example has some advert banners at the side or the bottom, the advert provider as part of the page can ‘listen in’ and find out what you type in that page,” Siamak F Shahandashti, one of the Newcastle University researchers who demonstrated the attack, told Ars. “Or with some browsers as we found, if you open a page A and then another page B without closing page A (which most people do) page A in the background can listen in on what you type in page B.”
No easy fix
The specific conditions under which various types of attacks worked varied from browser to browser, and, to a lesser extent, also depended on which operating system each browser ran on. The browser provided by the Chinese-US Web services company Baidu, whether running on iOS or Android, had the greatest access to sensors. As a result, the browser provided sensitive sensor data when a malicious webpage was loaded directly into an open or background browser tab, was loaded as an iframe into an open or background tab, or even when the malicious page was loaded directly or as an iframe when the device screen was locked. More widely used browsers, by contrast, restricted access to sensor data, but they still presented an opportunity for abuse.
Chrome for iOS, for instance, served sensor data to malicious sites that were loaded directly, as an iframe or as an ad into an active tab. The Google browser, however, blocked access to all sites loaded into background tabs or when the iPhone was locked. Chrome for Android worked similarly with the exception of not providing sensor data to ad servers. Firefox on Android also had access to sensors when the JavaScript was hosted directly or through an iframe on an active tab but not background tabs. Safari, meanwhile, had the same access as Firefox, but the Apple-made browser also accessed the code when the iPhone screen was locked. A full summary of the conditions for various browsers is in the table below:
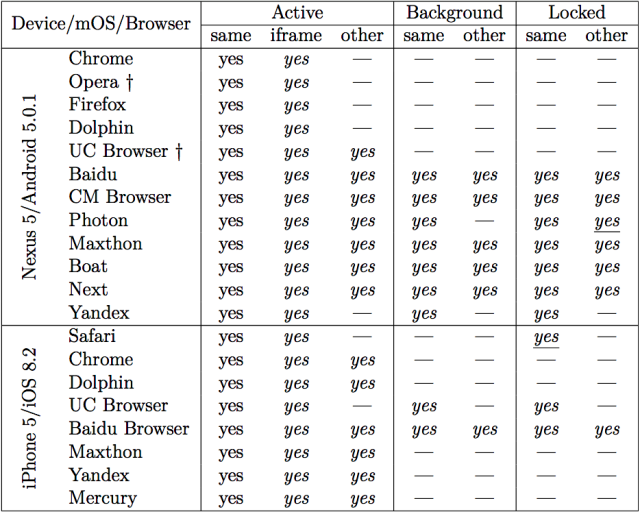
The researchers reported the results to the makers of Chrome, Firefox, Safari, and Opera. Mozilla issued a partial fix in version 46, in which Firefox restricted JavaScript access to motion and orientation sensors to top-level documents and same-origin iframes. In Apple Security Updates for iOS 9.3 released in March 2016, Safari took a similar countermeasure by suspending the availability of motion and orientation data when a page is hidden. While an effective means of thwarting the PINLogger attack, the updates also prevent the browsers from supporting useful features, such as those provided by fitness and exercise websites. Chrome, meanwhile, continues to make sensor data available to webpages that are loaded into an active tab. Chrome developers publicly acknowledged the issue here. (It wasn’t immediately clear how Opera developers responded.)
“There is no straightforward fix to the problem without also breaking potentially useful Web applications in the future,” another Newcastle University researcher, Feng Hao, told Ars. “No one is able to come up with a definite solution yet.”
It knows when you are sleeping
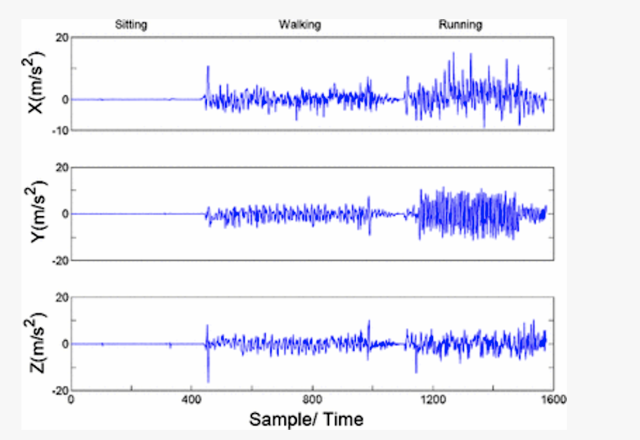
By accessing accelerometer and gyroscope sensors, the Web-hosted JavaScript measures subtle changes in a phone’s angle, rotation, movement speed, and similar characteristics. The data, in turn, can reveal sensitive information about the phone and its user, including the precise start and end of each phone call, if the person using it is stationary, walking, running, on a bus, in a car, or on a train. The researchers experimented using the Maxthon browser running on a Nexus 5 phone running Android version 5.1.1. Different devices running other browsers likely would behave similarly. The title of the paper is Stealing PINs via mobile sensors: actual risk versus user perception.
Of all the information the sensors reveal, the keystrokes being entered are almost certainly the most sensitive. The researchers used artificial neural network training to tie certain sensor measurements to specific characters contained in 50 four-digit PINS. PINLogger was able to infer subjects’ PINs with 74 percent accuracy on the first attempt and with nearly 100 percent accuracy in five attempts. By comparison, a random guess from a set of 50 PINs would have only a 2-percent chance of being correct on the first attempt and only 6 percent accuracy in three attempts.
“One might argue that the attack should be evaluated against the whole 4-digit PIN space,” the researchers wrote. “However, we believe that the attack could still be practical when selecting from a limited set of PINs since users do not select their PINs randomly. It has been reported that around 27 percent of all possible 4-digit PINs belong to a set of 20 PINs, including straightforward ones like ‘1111’, ‘1234’, or ‘2000’.”
The researchers went on to perform a separate round of training that evaluated all possible four-digit PINs. The training included two modes. The first, known as multiple-users mode, was trained using several subjects. The other mode, known as same-user mode, relied on the training of the individual being targeted in the attack. The researchers wrote:
The results in our multiple-users mode indicate that we can infer the digits with a success probability of 70.75, 83.27, and 94.03 percent in the first, second, and third attempts, respectively. This means that for a 4-digit PIN and based on the obtained sensor data, the attacker can guess the PIN from a set of 34 = 81 possible PINs with a probability of success of 0.92064 = 71.82 percent. A random attack, however, can only predict the 4-digit PIN with the probability of 0.81 percent in 81 attempts. By comparison, PINlogger.js achieves a dramatically higher success rate than a random attacker.
In same-user mode, the success probability of guessing the PIN in 81 attempts is 85.46 percent.
“Crucial open problem”
Right now, there’s no ideal way to prevent attacks. That’s because, as noted earlier, browsers that can’t access sensor data at all are likely to prevent many useful sites from working properly. For people using Chrome, a good practice is to close tabs as often as possible. The researchers warned that unless browser and OS makers figure out a better, long-term solution, the threat is likely to grow.
“Access to mobile sensor data via JavaScript is limited to only a few sensors at the moment,” they wrote. “This will probably expand in the future, especially with the rapid development of sensor-enabled devices in the Internet of things. Hence, designing a general mechanism for secure and usable sensor data management remains a crucial open problem for future research.”
Source:https://arstechnica.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











