Even worse: Thousands of other sites are making the same facepalm-worthy mistake.
Five days before Patreon.com officials said their donations website was plundered by hackers, researchers at a third-party security firm notified them that a serious programming error could lead to disastrous results. The researchers now believe the vulnerability was the entry point for attackers who went on to publish almost 15 gigabytes’ worth of source code, user password data, and private messages.
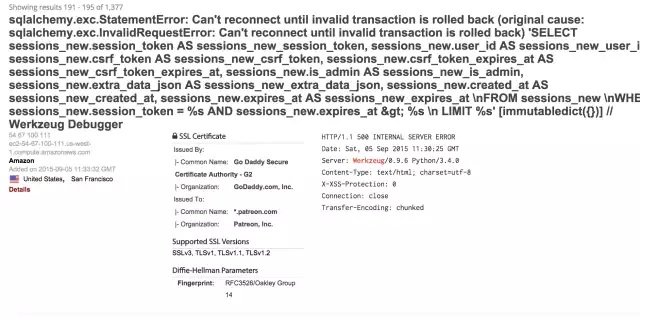
The error was nothing short of facepalm material. Patreon developers allowed a Web application tool known as theWerkzeug utility library to run on a public-facing subdomain. Specifically, according to researchers at Swedish security firm Detectify, one or more of Patreon’s live Web apps on zach.patreon.com was running Werkzeug debugging functions. A simple query on the Shodan search servicebrought the goof to the attention of Detectify researchers, who in turn notified Patreon officials on September 23. Adding to their concern, the same Shodan search shows thousands of other websites making the same game-over mistake.
Remote code execution by design
The reason for the alarm was clear. The Werkzeug debugger allows visitors to execute code of their choice from within the browser. Werkzeug developers have long been clear about this capability and the massive risks that stem from using it in production environments. But in case anyone missed the warning, an independent blogger called attention to the threat last December.
“This is basically Remote Code Execution by design,” Detectify researcher Frans Rosén wrote in ablog post published Friday morning. “An RCE is basically game over. You can inject code directly to the application, exposing all data on the server which the application has access to.”
He said the code-execution capability is supposed to be triggered only after a developer enters a secret key that’s generated when the debugger first loads. But by design, the debugger will get activated whenever a covered Web app experiences an error or exception. As a result, even unauthorized people who visited Patreon could activate the debugging tool, as long as they could trigger some sort of bug on the site. That’s precisely the way Rosén said he suspects hackers breached Patreon.
“Most certainly they created an interactive shell which connected to them remotely, which would make it possible for them to walk around the server and push all data over to the attackers,” Rosén wrote in an e-mail to Ars. “The good thing is that since all communication of the commands sent into Werkzeug are done via GET-requests, [Patreon officials] will most certainly be able to see exactly what commands that was being issued. However, it’ll probably just reveal a creation of an interactive shell which [the hackers] then used to extract all the data.”
The Detectify version of events is consistent with the official notification delivered Thursday by Patreon CEO Jack Conte. In it, he said the unauthorized access was caused by “a debug version of our website that was visible to the public. Once we identified this, we shut down the server and moved all of our non-production servers behind our firewall.” But that discovery came on September 28, five days after Detectify said it notified them of the error.
Patreon officials have yet to respond to Ars’ queries about the misconfigured debugger and Detectify’s account that they knew of it long before the unauthorized access is said to have happened. This post will be updated if they get back to us later.
Source:https://arstechnica.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.