Zimperium, the mobile security company that discovered the Stagefright bug in the summer of 2015, announced yesterday its intention to buy fully-working exploits for former Android and iOS zero-days.
Zero-days are security bugs that are used in live attacks, but for which there’s no available patch. Once the vendor affected by the zero-day issues a security update, the zero-day becomes an N-day, or regular security flaw, which users can mitigate by applying the latest product update.
In the underground hacking scene, hackers and security researchers can sell the zero-days they discover for thousands of dollars. Sometimes, depending on the the zero-day’s impact and exploitability, zero-days have been known to reach hundreds of thousands of dollars or even millions.
For example, a company called Zerodium has been known to offer millions for remotely-exploitable zero-days in Apple’s most recent iOS version, an offer that’s still standing even today. Below is a chart with the prices Zerodium is known to pay for various types of zero-days.
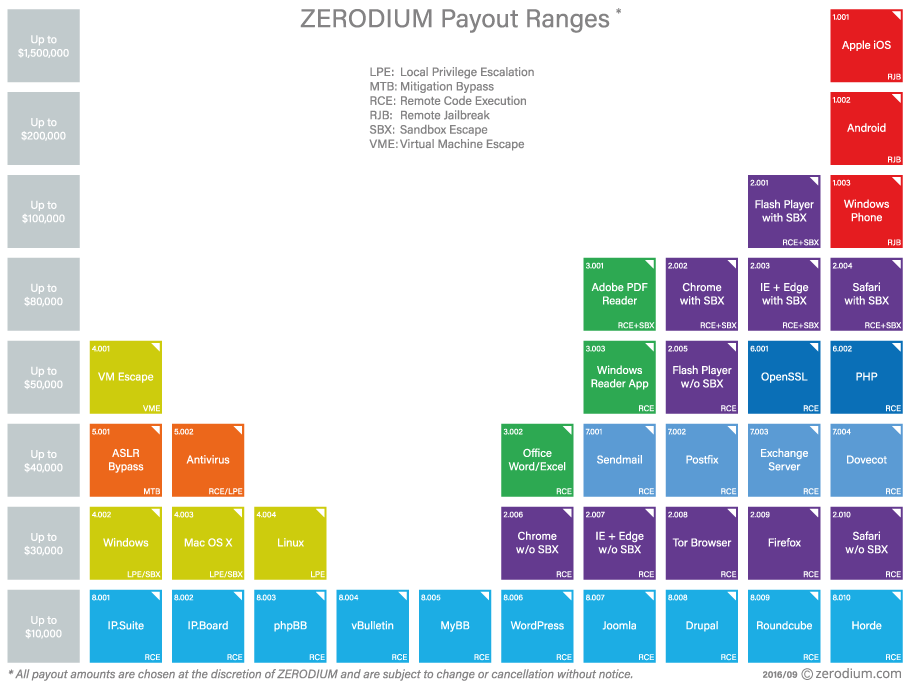
But this thriving market will suddenly go cold when vendors get wind of the flaw and patch the zero-day.
In most cases, a patched zero-day is worth $0. Despite this, many of these zero-days, and their exploit chain, never come to light, and attackers still use the for months or years, attacking users using outdated devices and software versions.
Zimperium launches N-day Exploit Acquisition Program
Here’s where Zimperium’s offer comes in. The company hopes that hackers and security researchers will sell these used zero-days, instead of keeping them secret.
Zimperium didn’t provide details about how much it’s willing to pay per N-day exploit, but the company said it’s doing it to boost the efficiency of its z9 scanning engine, deployed via the company’s apps on the phones of thousands of enterprises around the globe.
Further, Zimperium also plans to release the N-day exploit code publicly, so other researchers and security firms can protect their clients against similar attacks, learn from the exploit routine, and use the knowledge to identify similar security bugs.
N-day exploit code to be shared with vendors, mobile carriers
Additionally, the N-day exploit will also be shared with members of the Zimperium Handset Alliance (ZHA), which includes big names such as Samsung, Blackberry, Telstra, and other mobile carriers and handset vendors, who’ll have 30 days to issue patches before Zimperium makes the exploit code public.
Zimperium said it allocated $1.5 million to finance the first stage of the Exploit Acquisition Program, which is around the maximum payout a researcher could get from selling a fully-working zero-day to Zerodium.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











