The VirLocker ransomware made a comeback this past week with a new and very virulent version, but the Malwarebytes security team says there’s a way for victims to recover files by entering a special code in the payment field.
VirLocker, also known as VirLock or VirRansom, is a ransomware family that was first spotted by Bleeping Computer in 2014 and was first referred to as Operation Global III.
The ransomware never went away after its first versions and kept a low profile, never being at the heart of massive spam campaigns like the ones that pushed TorrentLocker, CryptoLocker, TeslaCrypt, and more recently Cerber and Locky. New versions continued to come out, like this one in 2016, and the one discovered by Malwarebytes this week.
VirLocker can be removed with one code
According to long-time Bleeping Computer forum user and Malwarebytes security researcher Nathan Scott, this recent version can be defeated, even without a special decryptor.
The trick, Scott says, is to enter 64 zeros in the VirLocker ransom note, in the “Transfer ID” section.
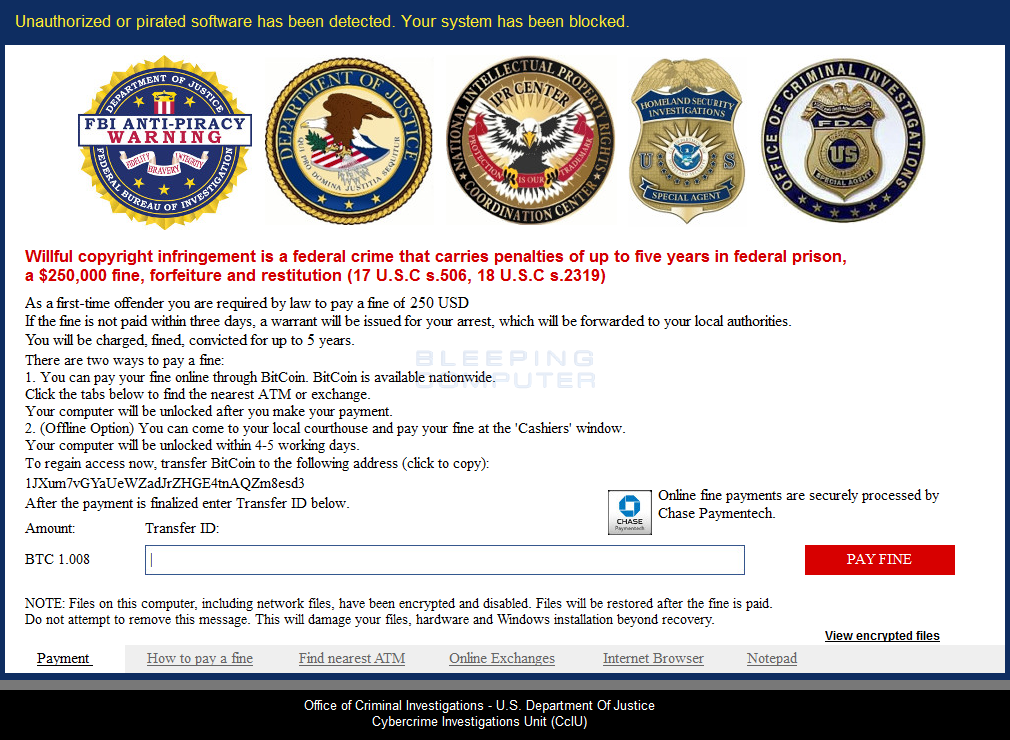
This code will trick the ransomware into thinking the user has paid the ransom. But the user’s work is not yet done, and it’s actually only beginning.
VirLocker encrypts and packs all files inside executables
The VirLocker infection process is in large part the same as it was in 2014, and works by taking a victim’s files and wrapping them inside an EXE shell. This means that all files are encrypted and then repackaged as an executable.
For example, an image file named photo.png will become photo.png.exe. Since most Windows installations hide the last file extension, users will only see photo.png, and not know the file is a binary.
But it gets even worse as every one of these EXE files also contains a copy of the VirLocker ransomware, meaning that some users could be spreading malicious files to their friends, or backing up a copy of VirLocker without even knowing. The fact that VirLocker creates actual EXE files, and not just appends a fake .exe extension, makes VirLocker extremely dangerous, allowing it to spread with ease.
Decrypting all your files will take a while
Scott says that victims that entered the 64-zeroes code should immediately start opening all their important files, the ones they want to save.
He says users should double-click the EXE file corresponding to important files. The EXE file (and the embedded VirLocker variant) will see that the ransomware has been paid, and will extract and decrypt the original file from inside the EXE file, creating a copy on disk.
For example, double-clicking photo.png.exe will create a second file called photo.png, which is the original file. Beware that the contaminated EXE file will remain on disk, next to the original.
There’s no automated decryption process, and victims have to go over their hard drive and extract files manually.
Victims should recover original files and wipe their hard drive
Once they’ve finished this operation, Scott recommends that victims move all their original files to a backup drive, paying special attention not to copy any of the EXE versions that include the live VirLocker ransomware. Copying one of the rogue EXE locked files would either spread the VirLocker infection to new hosts, or reinfect the PC later on.
After backing up their data, users should wipe their computer clean and reinstall their operating system, as there’s a high chance they might get reinfected from a rogue file left on disk.
“You can no longer trust a single file that is on the affected machine,” Scott wrote in a blog post that also explained how the recent VirLocker version works in great detail. Below are more screenshots of the VirLocker ransom screen.
Sourcehttps://www.bleepingcomputer.com

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











