A ransomware family named FireCrypt will encrypt the user’s files, but also attempt to launch a very feeble DDoS attack on a URL hardcoded in its source code.
This threat was discovered today by MalwareHunterTeam. Below is an analysis of the ransomware’s mode of operation, provided by MalwareHunterTeam and Bleeping Computer’s Lawrence Abrams.
FireCrypt comes as a ransomware building kit
Malware is usually generated by compiling it from source code, or by using automated software that takes certain input parameters and outputs a customized malware payload on a per-campaign basis.
The latter are known in the industry as malware builders and usually come as command-line applications or GUI-based tools.
The author of the FireCrypt ransomware uses a command-line application that automates the process of putting FireCrypt samples together, allowing him to modify basic settings without having to tinker with bulky IDEs that compile its source code.
FireCrypt’s builder is named BleedGreen (seen below), and allows the FireCrypt author to generate a unique ransomware executable, give it a custom name, and use a personalized file icon. Compared to other ransomware builders, this is a very low-end application. Similar builders usually allow crooks to customize a wider set of options, such as the Bitcoin address where to receive payments, the ransom demand value, contact email address, and more.
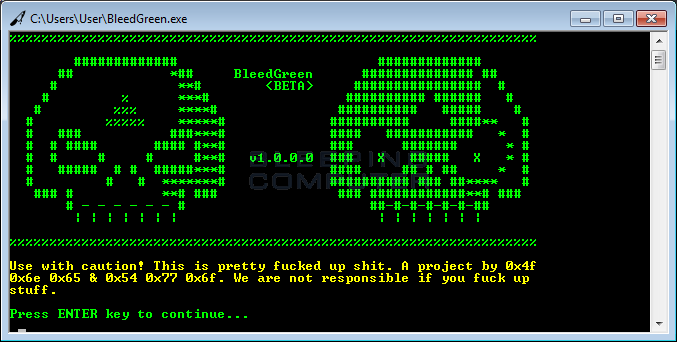
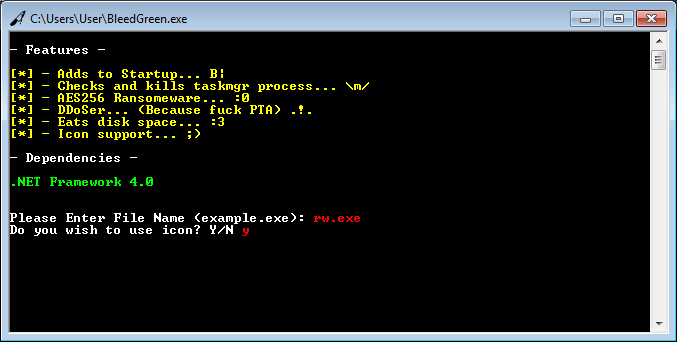
The builder’s role, besides disguising an EXE file under a PDF or DOC icon, is also to slightly alter the ransomware’s binary, in order to generate a file with a different hash at every new compilation.
The technique is often used by malware developers to create so-called “polymorphic malware” that’s harder to detect by standard antivirus software. According to MalwareHunterTeam, “the builder is very basic, so this shouldn’t help anything against real AVs.”
Nevertheless, this also tells us that FireCrypt author has at least some sort of experience in developing malware, and isn’t your regular script kiddie that downloaded open-source ransomware from GitHub.
FireCrypt infection process
The FireCrypt infection process hinges on the ransomware’s distributor’s ability to trick users in launching the EXE file they just generated.
Once this happens, FireCrypt will kill the computer’s Task Manager (taskmgr.exe) and begin to encrypt a list of 20 file types. FireCrypt encrypts files with the AES-256 encryption algorithm.
All encrypted files will have their original file name and extension appended with “.firecrypt”. For example, a file named photo.png will be renamed into photo.png.firecrypt.
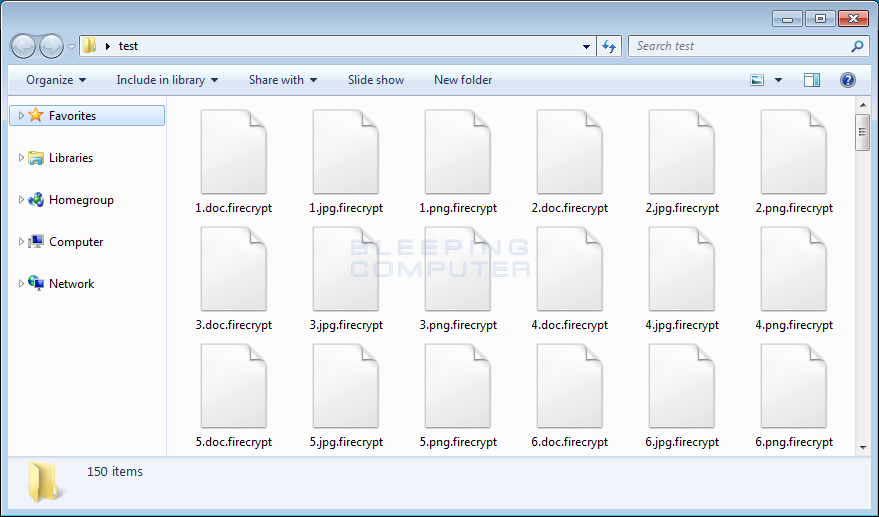
Once the file encryption process ends, FireCrypt drops its ransom note on the user’s Desktop.
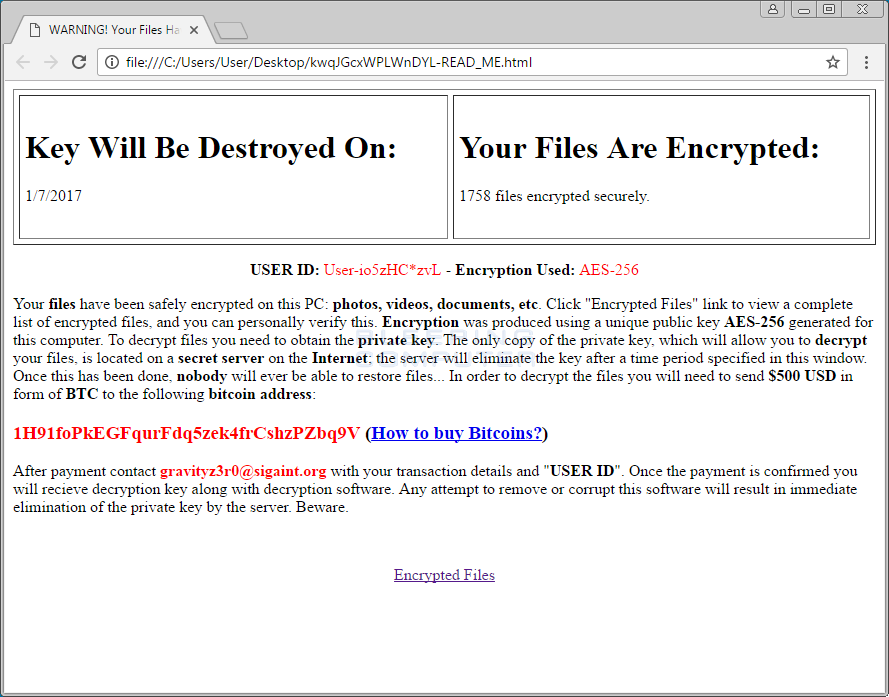
The ransom note is a nearly identical copy of the ransom note used by the Deadly for a Good Purpose Ransomware, discovered on October 14 by the same MalwareHunterTeam.
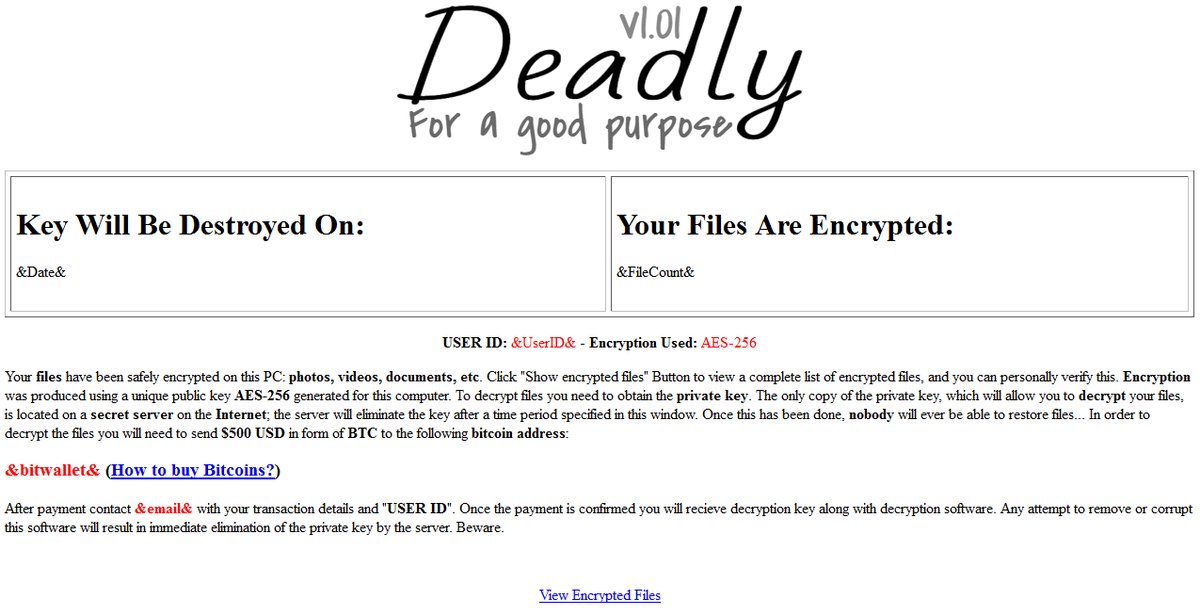
At the time it was discovered in October 2016, the Deadly for a Good Purpose Ransomware appeared to be under development, as its source code would begin the file encryption process only if the victim’s computer date were for a day in 2017 and later.
Compared to FireCrypt, the only difference is that the Deadly for a Good Purpose Ransomware also featured a logo at the top of the ransom note, now missing in FireCrypt. But, at a close inspection of Deadly’s source code, MalwareHunterTeam was able to discover that both ransomware versions used the same email and Bitcoin addresses, showing a clear connection between the two, with FireCrypt being a rebranded version of the original Deadly for a Good Purpose Ransomware.
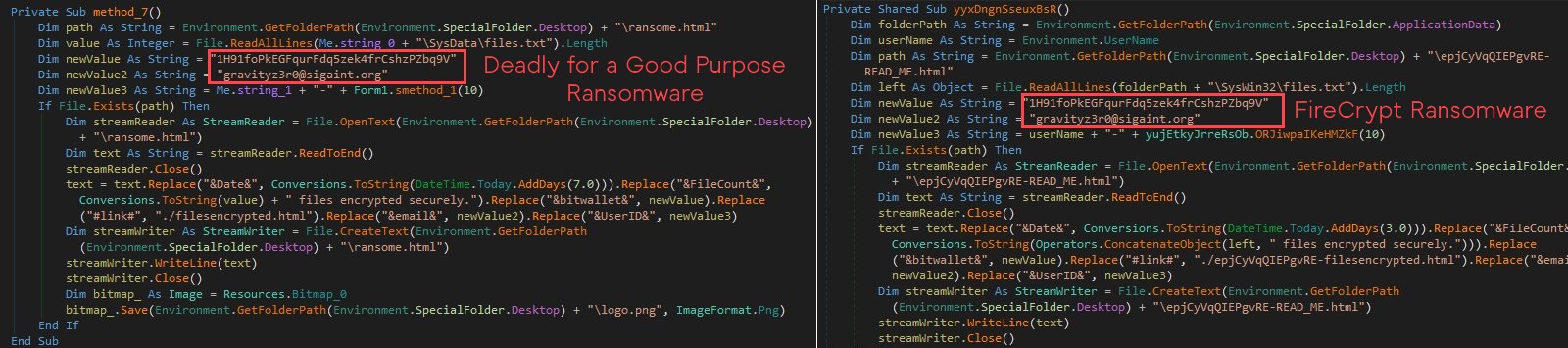
The DDoS function that fills your hard drive with junk files
After dropping the ransom note, FireCrypt doesn’t stop its malicious behavior. Its source code contains a function that continuously connects to a URL, downloads its content and saves it to disk in a file in the %Temp% folder, named [random_chars]-[connect_number].html.
If users aren’t aware of this function, FireCrypt will quickly fill the %Temp% folder up with junk files.
Current versions of the FireCrypt ransomware will download the content of https://www.pta.gov.pk/index.php, which is the official portal of Pakistan’s Telecommunication Authority. This URL cannot be modified using the ransomware’s builder.
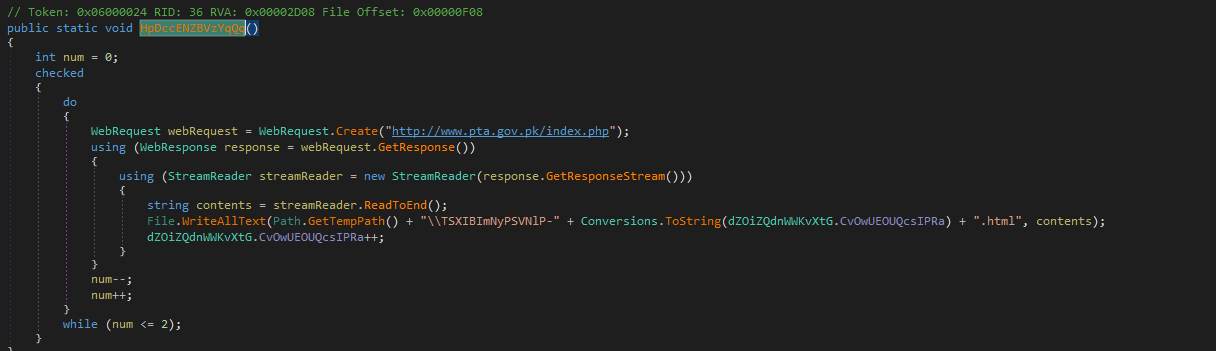
The FireCrypt author calls this feature as a “DDoSer,” but this would be a stretch. The crook would have to infect thousands of victims before launching a DDoS attack large enough to cause any problems to the Authority’s website.
Furthermore, all victims should be infected at the same time, and have their computers connected to the Internet in order to participate in the DDoS attack.
At the time of writing, there’s no known method of recovering files encrypted with FireCrypt. Victims infected with this threat that are unable or unwilling to pay the $500 ransom demand should keep a copy of their encrypted files around, as a decrypter might be possibly released in the future.
Targeted file extensions:
.txt, .jpg, .png, .doc, .docx, .csv, .sql, .mdb, .sln, .php, .asp, .aspx, .html, .htm, .csx, .psd, .aep, .mp3, .pdf, .torrentFiles associated with FireCrypt ransomware:
%AppData%\Microsoft\Windows\Start Menu\Programs\Startup\[random_chars].exe - Startup Executable
%Desktop%\[random_chars]-READ_ME.html - Ransom Note
%AppData%\SysWin32\files.txt - List of Encrypted Files
%Desktop%\random_chars]-filesencrypted.html - List of Encrypted Files
%Temp%\random_chars]-[connect_number].html - Files downloaded during the DDoS attackHashes associated with the FireCrypt ransomware:
BleedGreen builder (VirusTotal scan is currently at 2/57 detections):
SHA-256: e77df2ce34949eb11290445a411a47fb927e8871e2580897581981d17730032dA FireCrypt ransomware binary sample (VirusTotal scan is currently at 13/57 detections):
SHA-256: d49240e38603c29b38db86b6c11795f166e63d8385e8626232131f750cdb434fEmail Address and Payment Contacts:
EMAIL: gravityz3r0@sigaint.orgSource:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











