The Kangaroo ransomware is the latest ransomware from the developer behind the Apocalypse Ransomware, Fabiansomware, and Esmeralda. What makes this version stand out a bit more is the use of a legal notice as a ransom note that is displayed to all victims before they login to their computer. This makes it so a victim has to view the ransom note before they are able to login to Windows.
Also, due to the ransomware terminating the Explorer processes when started and preventing the launching of Task Manager, it essentially locks a user out of Windows until they pay the ransom or remove the infection. Though the screenlocker can be disabled in Safe Mode or by pressing the ALT+F4keyboard combination, for many casual computer users this would essentially prevent them from using their computer.
Kangaroo is installed manually by Hacking into RDP
Unlike most other ransomware infections, this family is not spread through exploit kits, cracks, compromised sites, or Trojans, but instead by the developer manually hacking into computers using Remote Desktop. When the dev hacks into a computer and executes the ransomware, a screen will be shown that contains the victim’s unique ID and their encryption key.
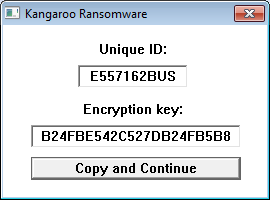
When the developer clicks on Copy and Continue, the information will be copied into the Windows clipboard so that developer can save it. The ransomware will then begin to encrypt the computer’s files and will append the .crypted_file extension to an encrypted file’s name. This ransomware also performs the strange practice of creating an individual ransom note for every file that is encrypted. These ransom notes will be in the format of filename.Instructions_Data_Recovery.txt. For example, test.jpg.Instructions_Data_Recovery.txt.
When finished Kangaroo will display a lock screen that displays a fake screen implying that there is a critical problem with the computer and that the data was encrypted. It then provides instructions on how to contact the developer at kangarooencryption@mail.ru to restore the data.
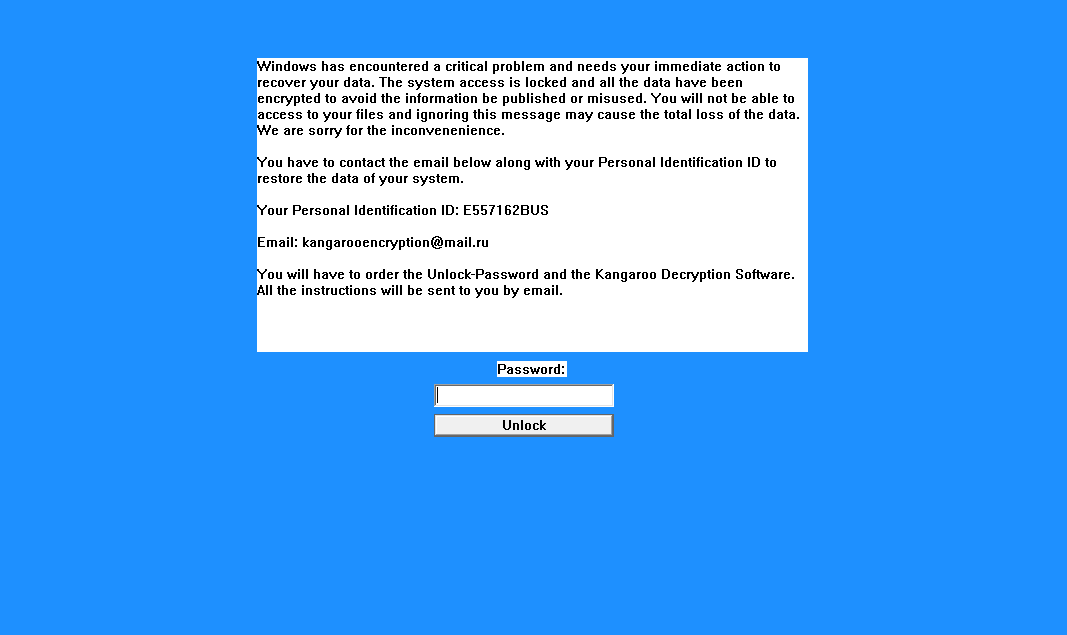
This ransomware will also configure the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon “LegalNoticeText” registry value so that it shows a legal notice that a user must read before they are shown the Windows login prompt. This guarantees that a victim, or a computer’s administrator, will see the ransom note the next time they login.
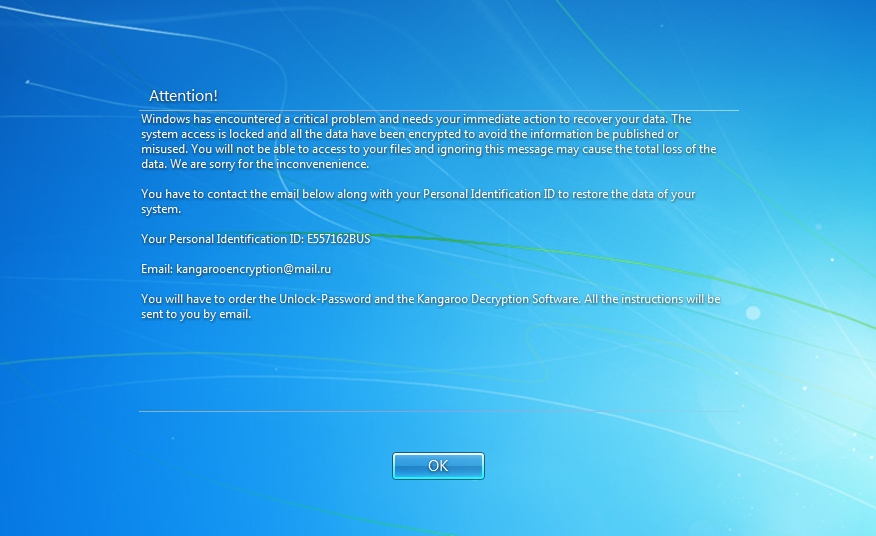
While at this time, there is no way to decrypt the encrypted files for free, it is possible to remove the screenlocker portion so that victims can use their computer again. For those who need help with this, I provide instructions in the next section.
Removing the Kangaroo ScreenLocker
Warning: Only follow these steps if you do not plan on paying the ransom. By deleting the ransomware executable, you will not be able to pay for and decrypt your files at a later date.
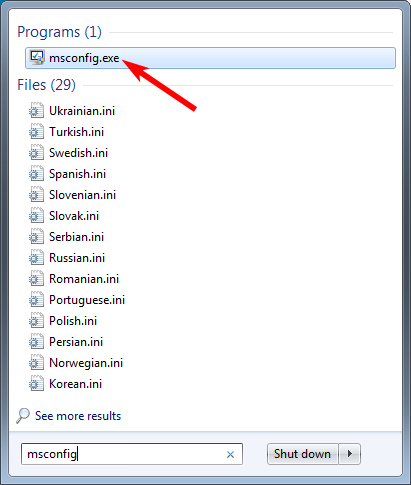
In order to gain access to the Windows desktop again, a victim will need to disable the Kangaroo executable from running. To do this, a victim needs to boot the computer into Windows Safe Mode so that they will have access to the Windows desktop again. Once logged into Windows Safe Mode, they can run the msconfig.exe and disable the malware from running.
To start msconfig, simply click on the Start button and in the search field, type msconfig. When the search results show msconfig.exe as seen in the image below, please click on it.
When Msconfig starts, click on the Startup tab and uncheck the entries that have the C:\Program Files (x86)\Windows NT\explorer.exe command as shown by the highlighted entry below.
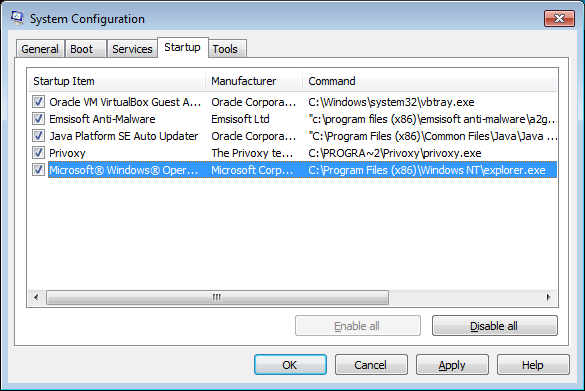
Once you have unchecked the associated entries, click on the Apply and OK button, but do not allow the computer to reboot yet.
We now need to start the Task Scheduler control panel and remove an associated task that may have been created. To start Task Scheduler, simply search for task scheduler in the start menu and click on its search result. When the Task Scheduler opens, search for a task that contains a series of characters and numbers. For example, on my test computer the task was named CA334104-D8EF-4C36-BCD7-2ECE003D03B6}.
To make sure you find the correct task, you can double-click on it to open its properties. You then should click on the Action tab to confirm that the program that will run is the executable for the Kangaroo ransomware. You can see an example of this task in the screenshot below.
Note: If you need help with this process, feel free to ask us in the forums or here. Before asking for help, though, please create a screenshot of the various tasks so we can help you identify the correct one.
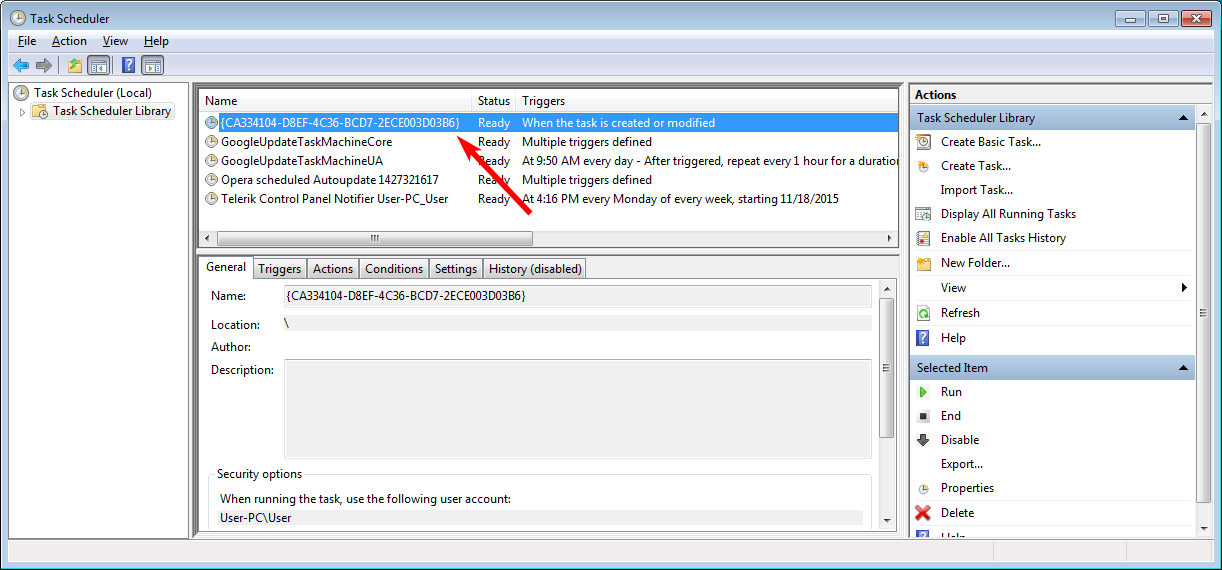
Once you have identified the proper task, you can right click on it and delete it.
The Kangaroo ransomware will now be removed from the computer and you can reboot back your computer so that Windows starts normally. Once you are logged back into Windows, you should perform a security scan with your preferred anti-virus or anti-malware product.
Kangaroo encrypted files cannot be decrypted for free.
Unfortunately, files encrypted by the Kangaroo ransomware cannot be decrypted for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Kangaroo does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
Files associated with the Kangaroo Ransomware:
C:\Program Files (x86)\Windows NT\explorer.exeRegistry entries associated with the Kangaroo Ransomware:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Windows Explorer"="C:\Program Files (x86)\Windows NT\explorer.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "Windows Explorer"="C:\Program Files (x86)\Windows NT\explorer.exe"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon "LegalNoticeCaption"="Attention!"
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon "LegalNoticeText"="Windows has encountered a critical problem and needs your immediate action to recover your data. The system access is locked and all the data have been encrypted to avoid the information be published or misused. You will not be able to access to your files and ignoring this message may cause the total loss of the data. We are sorry for the inconvenenience.
You have to contact the email below along with your Personal Identification ID to restore the data of your system.
Your Personal Identification ID: E557162BUS
Email: kangarooencryption@mail.ru
You will have to order the Unlock-Password and the Kangaroo Decryption Software. All the instructions will be sent to you by email."
Associated email addresses with the Kangaroo Ransomware:
kangarooencryption@mail.ru Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











