In a surprise move, the master decryption keys for the CrySiS Ransomware have been released early this morning in a post on the BleepingComputer.com forums. At approximately 1 AM EST, a member named crss7777 created a post in the CrySiS support topic at BleepingComputer with a Pastebin link to a C header file containing the actual master decryption keys and information on how to utilize them,
These keys have already been used by Kaspersky Labs to update their RakhniDecryptor program so that it can be used to decrypt victim’s files.
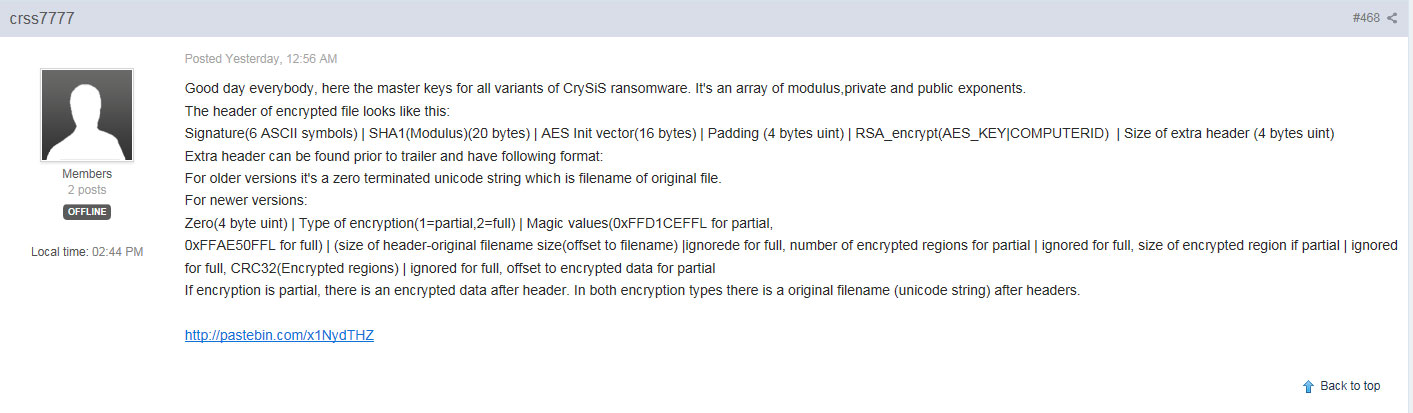
Though the identity of crss7777 is not currently known, the intimate knowledge they have regarding the structure of the master decryption keys and the fact that they released the keys as a C header file indicates that they may be one of the developers of the CrySiS ransomware. Why the keys were released is also unknown, but it may be due to the increasing pressure by law enforcement on ransomware infections and the developers behind them.
When the released keys were examined by Kaspersky Lab it was determined that these keys were legitimate. Using these keys, Kaspersky have updated their RakhniDecryptor program so that it can now decrypt CrySiS encrypted files.
Using RakhniDecryptor to decrypt CrySiS Encrypted Files
Victims of the CrySiS ransomware can be identified by their files being encrypted and renamed to the format of [filename].id-[id].[email_address].xtbl. For example, the most recent variants would have a file named test.jpg renamed and encrypted as test.jpg.id-ABADG125.alex-king@india.com.xtbl.
Some other variants that have previously been seen include Vegclass@aol.com.xtbl, gerkaman@aol.com.xtb, johnycryptor@hackermail.com.xtbl, and Milarepa.lotos@aol.com.xtbl.
To decrypt files encrypted by the CrySiS ransomware, you need to first download the RakhniDecryptor. Once downloaded, you should extract the program and run it. Once running it will display the main screen as shown below.
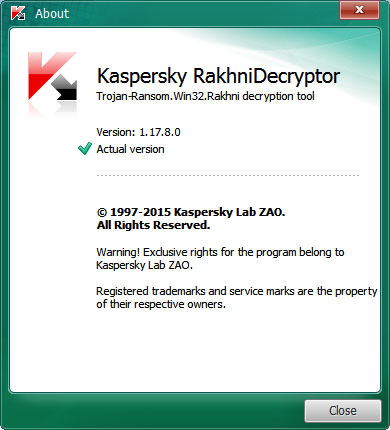
Before starting, you need to make sure that you are using version 1.17.8.0, which supports the CrySiS ransomware. To check the version of the RakhniDecryptor you can click on the About link at the bottom left of the above screen. This will display a small window that shows the version of RakhniDecryptor.
If you are using version 1.17.8.0 or greater, then you should click on the Start scan button and RakhniDecryptor will prompt you to select an encrypted file. Browse to a folder that contains CrySiS encrypted files and select a .Word, Excel, PDF, music, or image file. Do not select a text file as it cannot be used to decrypt the rest of your files.
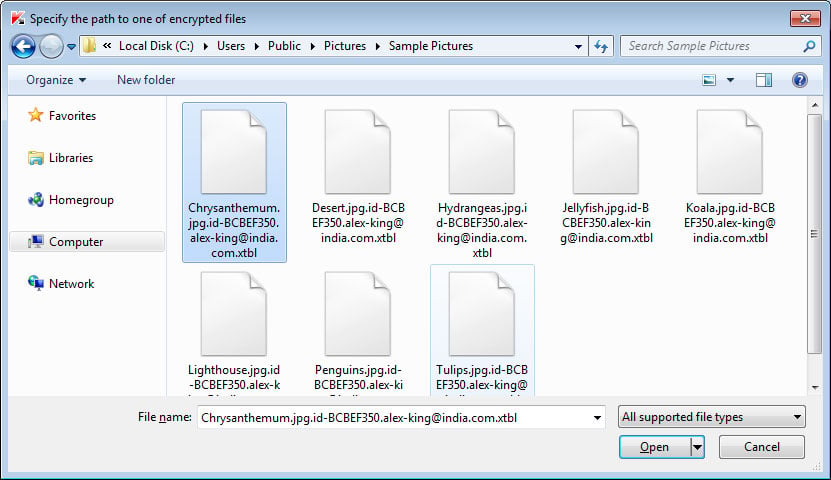
Once you have selected a file, click on the Open button. RakhniDecryptor will now scan the entire computer for encrypted files and decrypt them.
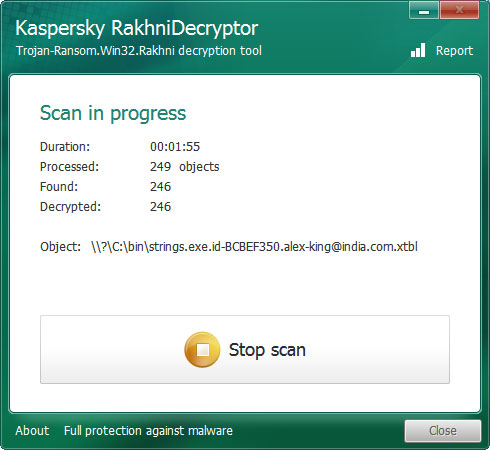
This process can take quite a long time, so please be patient while it scans your computer and decrypts the files.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











