VIRUS a piece of malicious coded file can turn your life into hell , Worlds first PC virus was created in Pakistan , Lahore by two brothers named Basit and Farooq they got popularity from a name ” Alvi Brothers ” all over the world and proved the world that nothing is safe and could be exploited easily however in one of the interview with Alvi Brothers they said this virus was not created for destruction nor to steal or spy on anyone but to show the world how we can exploit the vulnerabilities which must be patched. Hence they named it ” Brain Virus “

How To Defuse The VIRUS ?
Defusing the time bomb sounds good but defusing the virus file sounds awesome. Today i would like to share my proof of concept on how you can simply finish the access of attacker. Lets consider a viral executable file like ” virus.exe ” which is used to remotely spy on the victim pc likely controling everything including switching to the webcam , stealing files and keylogs. Such type of viruses or malwares are comonly known as ” RAT – Remote Administration Software ” which were created to control and keep record of staff working in a company but later hackers exploited this and created many malicious type of software’s and one of the famous among rat is DarkComet.
To learn defusing a virus or malware , you must first have a basic knowledge how such type of simple malware’s work ?
They have a command and control structure on the administrator or Hackers machine and on the other hand once this virus file is executed on victims machine it will send all the logs and specific information commanded by the hacker via his or her command and control structure.
The data which is sent from client side to server side or to hackers machine uses an ” IP Address” or a ” Domain name server ” which points to IP in case if IP is not static. DNS is usually used by hacker to maintain his access for a long time so even if his her ip changes he can simply update his ip by pointing the dns to his new ip. The virus mostly uses some open ports to get faster rate of transfer from client side to server side or from server side to client side.
This is how it works in 2 simple cases
1- In Hackers Case if command is sent
Command and control structure > Command > DNS > IP > Victim Virus >..>Command and Control Structure ( executed successfully )
2- In Victims case if Data is requested > File.doc > DNS > IP > Command and control structure ( file received )
In Both cases IP and DNS are playing vital role and is the backbone for communication between virus file and command and control structure. To exploit the weakness if server is not on stealth mode and victim is himself as administrator he can use our today’s trick to get rid of that virus.
As i mentioned that in both cases virus is using DNS or IP to send the data to his owner or Hacker so first of all we need to find or to configure what is the IP Address or DNS of that virus which he is using which in term comes in Malware analysis but dont worry i have a simple solution for your malware analysis if you are not an expert.
There are many online companies which offer free malware analysis to your specified file. one of the best which i found is Malwr – https://malwr.com/. Visit the website of Malwr ” malwr.com “click on submit and upload the virus file. it will take some time to analyze your virus after you can goto analysis and can can check the detail of the virus including the servers.
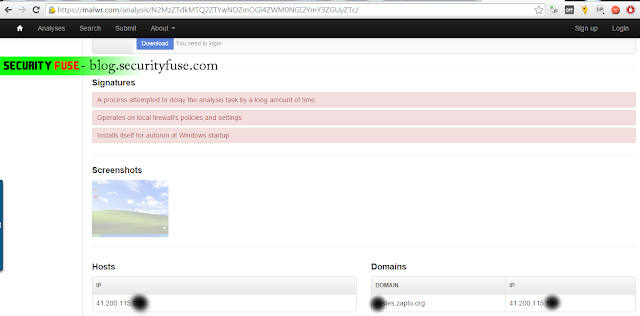
Now here as you can see that file is being detected as a virus file and it is using a DNS server zapto.org and DNS is pointing to attackers remote ip where the virus file is sending the data. However in other case like if the virus is running in stealth mode and let me also share this little knowledge with you that virus is not always sending ping requests to the attackers ip as it only works when attacker commands it and in the rest of time it is on sleep mode which makes its behavior normal to anti virus and make it hard for anti virus to detect it.
In case is virus is on stealth mode you can use different type of softwares to monitor DNS servers linked with your machine. Softwares like wireshark is also good to monitor the DNS Servers for which you need to open your Wireshark software and start capturing after it will show you the list of DNS Servers which are linked with your computer and are connected plus working but wait it may also show you some other sniffed stuff to so to avoid it use the dns filter to simply list only DNS servers for which type ” dns ” in the filters bar and hit enter.
As you can see that another virus is sending some of my private files to a no-ip server which mostly used by hackers because its free and also you can configure all the dns servers which are not verified to be linked with your installed programs. Keep in mind that in the rest of time the virus may be in sleep mode so you can wait for the time till attacker do some messy step with your machine once he will send any command to his virus then in reverse virus will send the acknowledgement command to the attackers dns or ip and as soon as possible it will list the dns server and at that time server will be in wake up position and will be responding to his hacker or owner.
After finding the DNS Server of the attacker open cmd to find its ip server where it is pointing and simply send the ping request to that DNS server by typing ” ping server.com ” replace server.com with your DNS
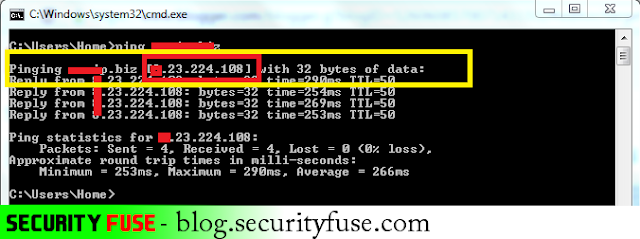
As you can see in the above picture that DNS of attacker is pointing to his remote IP where his command and control structure is located.
Now you have configured the DNS server , next is to defuse the server by simply cutting the supply of owner / attacker / hacker which his virus is working.
We are aware of HOST files which are responsible for editing the DNS – Domain Name servers on locally. We will simply goto the location of HOST files likely the HOST file in windows OS is located in ” C:\Windows\System32\drivers\etc ” There will be a file with a name ” HOST ” in which if you will type any Domain name server in it at the end and if you will also specify the servers ip to that DNS it will simply work with that ip server and ignoring the remote IP server. which is also known as local dns hijacking in cyber security.

Now Open your notepad as Administrator and open that Host file in text editor. You need to hijack that DNS server locally and point that DNS server to your localhost so when attacker will send command to dns and dns will resolve the ip and after resolving the ip virus will try to respond the attacker and when that virus file will try to resolve the IP it will be pointing to our localhost server which is 127.0.0.1
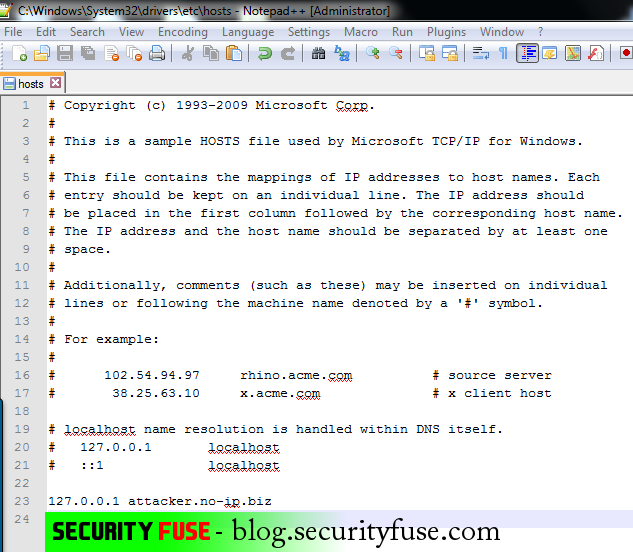
In the above picture you can see i have locally hijacked the DNS of the attacker and have pointed it to 127.0.0.1 so when my machine will try to respond to the attackers DNS it will respond to localhost not to the original ip address of the attacker. Save this host file and check the dns either its pointing to attackers ip or to our localhost.
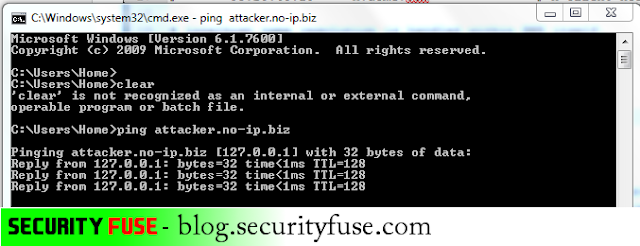
Now as you can see that attackers DNS is now successfully pointing to our Localhost IP which seems a bit safe now because each type of data which virus was sending to attacker was using a DNS which was pointing to attackers machine IP and now its resolving to localhost mean all the data is sending at 127.0.0.1
In case if attacker is using a static IP address and no DNS , you can use different type of softwares to block specific IP address either remote or local. So Simply block the ip address of attacker and defuse the virus.
I would prefer you to block both DNS and IP Address to make sure that virus is successfully defused run wireshark again and see if its sending request to dns and ping that DNS again and if DNS is pointing to localhost its safe.
Moreover you can also perform some social engineering type of attacks on attacker or hacker if you can analyze what sort of attack he is performing like if he is requesting a specific file like ” abc.doc ” a document file , you can replace that abc.doc with your viral file so according to attacker it would be a .doc file but if he opens he will be hacked. such type of attacks are performed using 0day doc exploits commonly known as silent doc exploits.
Source:https://blog.securityfuse.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.