Compromised WordPress websites are delivering spyware and PUAs (potentially unwanted applications) to users via fake Flash update messages and fake browser plugins.
Zscaler researchers have uncovered a covert spyware distribution campaign that relies on hacked WordPress websites to redirect users to spyware-infested URLs.
According to their findings, the campaign has been active since the first week of August and has been seen on over 2,000 sites, infecting over 20,000 users.
A closer look at the infected websites reveals that they are running the latest version of the WordPress CMS, version 4.3.1. Being the most recent and security-hardened release, Zscaler’s staff thinks most of the sites were infected in earlier versions, before the core was updated.
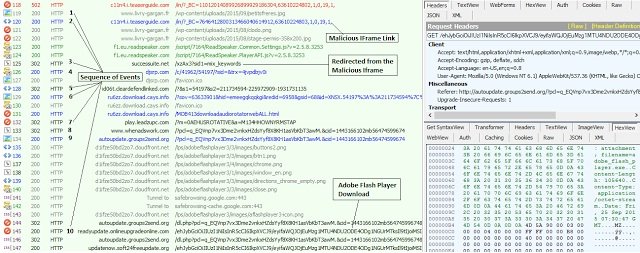
The infected sites are delivering malicious JavaScript code
In this most recent campaign, the infected websites are serving users a piece of malicious JavaScript code.
This code, when executed in the user’s browser, will load an iframe that in turn loads some more JavaScript code that allows it to collect user information and send it to a C&C server.
According to Zscaler, attackers are collecting data like the user’s system timestamp, timezone, and Adobe Flash Player version.
This information is sent to various domains, but all of which resolve to the same IP address, 91.226.33.54, allocated to a Latvian VPS hosting provider.
Once data on the user’s local system is collected and sent to the C&C server, the user is forwarded via a series of quick consecutive redirects to a Web page where, most of the times, the user is served spyware in the form of an Adobe Flash Player update.
On this page, the attackers show a message through which they hope to convince users to install or update their Flash Player. If users take any of these actions, they’re delivered an EXE file that installs a variant of the Win32.InstallCore PUA.
Attackers also use fake browser extensions to infect users
Once this PUA installed, the user is redirected to the real Adobe website, where they are informed that their Flash Player installation failed, and asked to try again, this time from the original & authentic source.
Zscaler researchers also observed that, in some cases, instead of the fake Adobe Flash Player update, users were asked to install various browser add-ons.
All of these are low-level spyware, scareware, adware, and PUAs, but dangerous nevertheless, mainly because they can later be used as entry points for more damaging malware. This is because almost all recent malware strands these days come with the ability to download other viruses and trojans on infected machines.
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.