Today we bring you Princess Locker; the ransomware only royalty could love. First discovered byMichael Gillespie, Princess Locker encrypts a victim’s data and then demands a hefty ransom amount of 3 bitcoins, or approximately $1,800 USD, to purchase a decryptor. If payment is not made in the specified timeframe, then the ransom payment doubles to 6 bitcoins
Not much is known about Princess Locker other than having seen a few encrypted files and ransom notes uploaded to ID-Ransomware. From what has been gather gathered, when a person is infected, the ransomware will encrypt the victim’s files and then append a random extension to encrypted files and a unique ID is created for the victim. This ID, extension, and encryption is then most likely sent up to the ransomware’s Command & Control server.
Ransom notes are also created and displayed, which are named!_HOW_TO_RESTORE_[extension].TXT and !_HOW_TO_RESTORE_[extension].html.
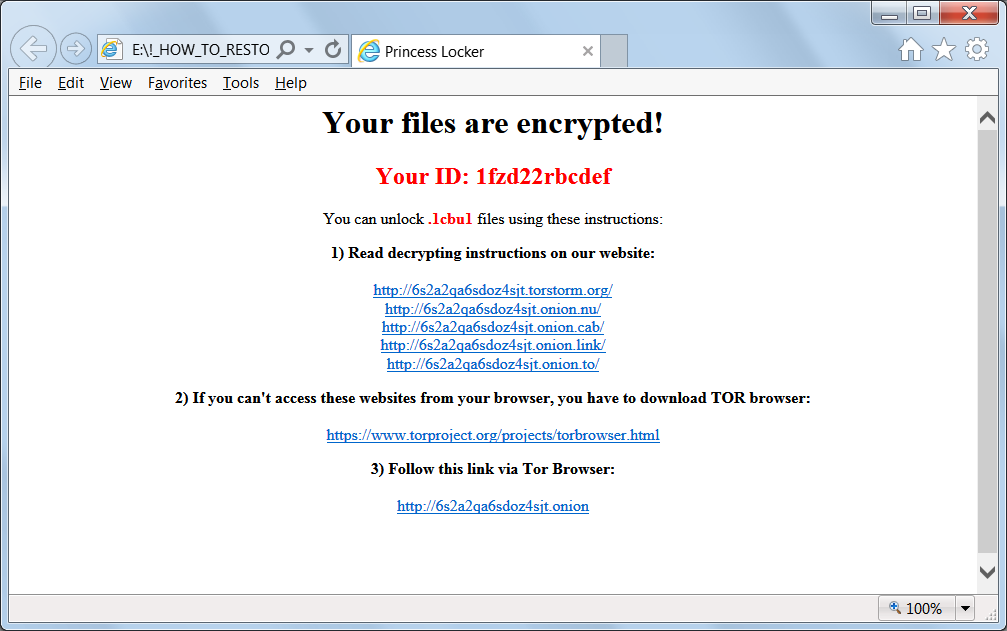
These ransom notes contain the victim’s ID and links to the TOR payment sites where a victim can login to see payment information.
The Princess Locker Payment Site
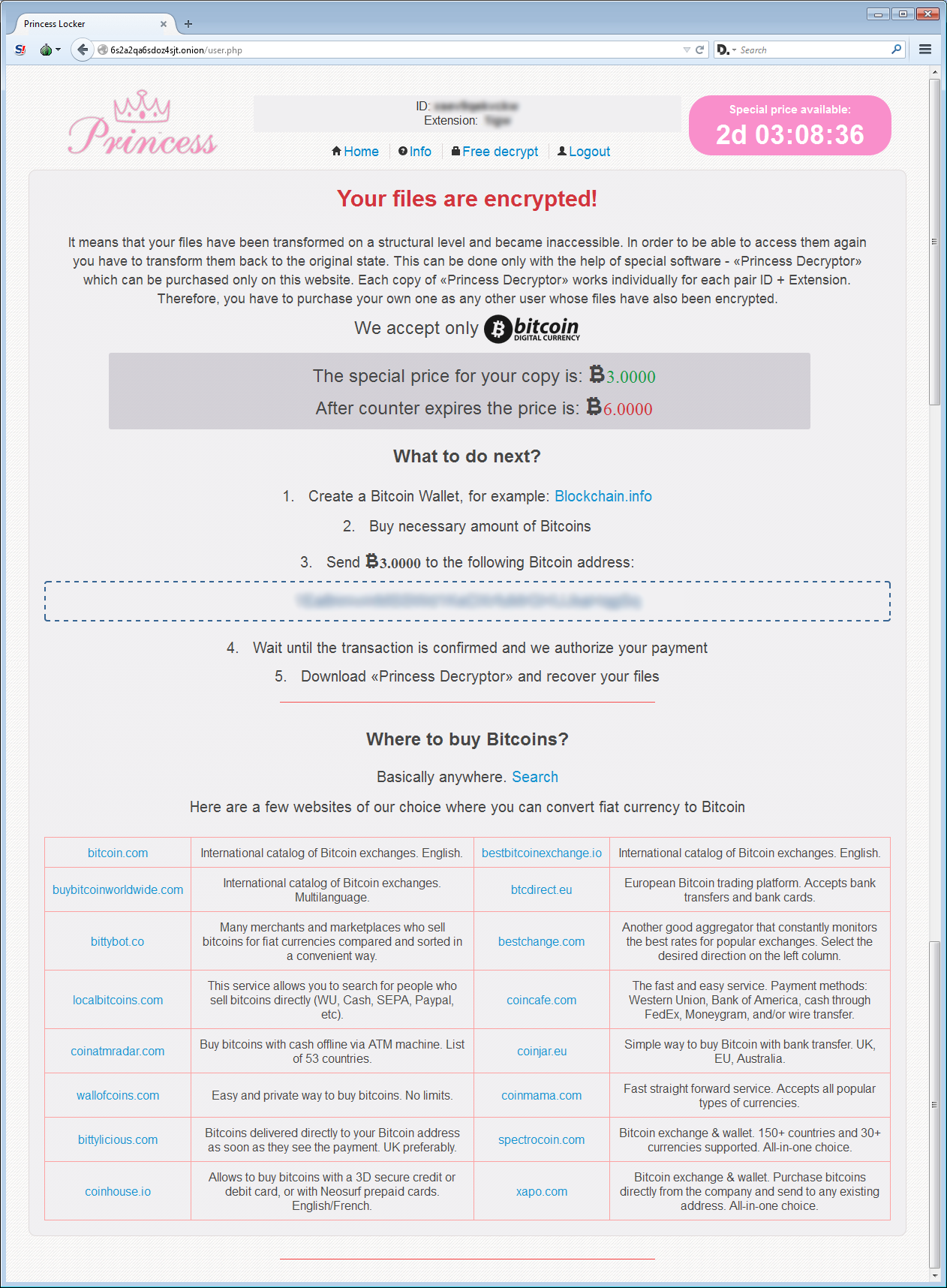
The Princess Locker payment site is your standard ransomware site with no special features. When victim’s access the Princess Locker payment site they will be greeted with a page asking them to select a language that looks almost identical to Cerber’s language selection page.

They will then be presented with a login prompt where they need to enter the victim ID provided in the ransom note. Once logged in they will see the main payment site, which contains information such as the ransom amount, the bitcoin address to send payment to, and the answers to common questions.
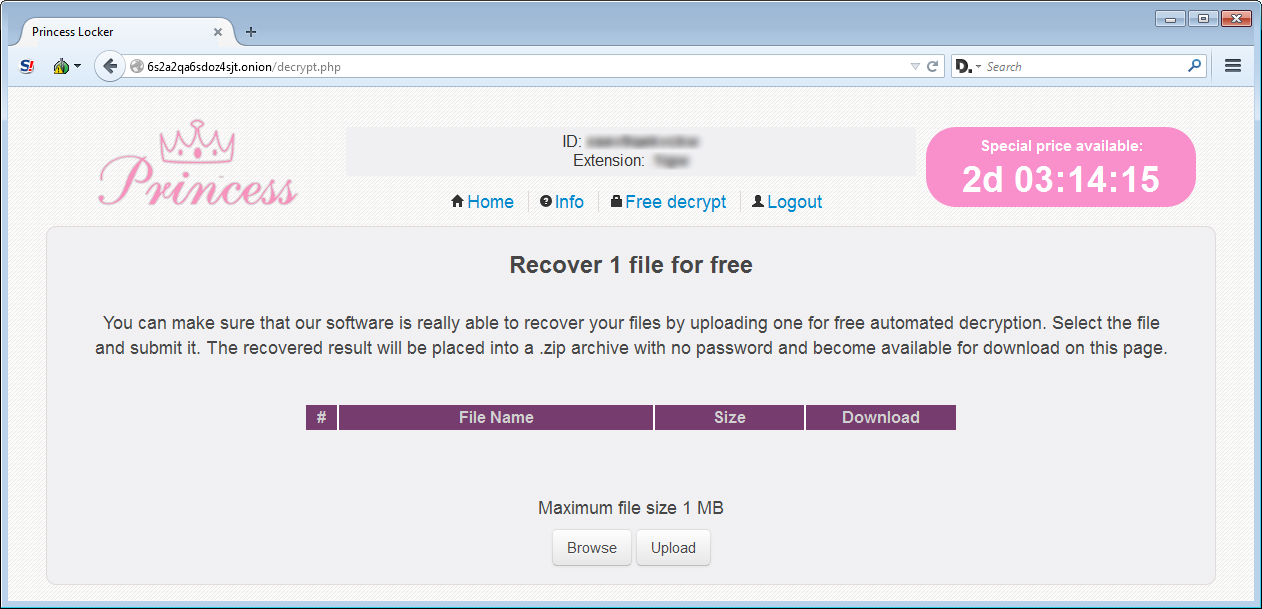
The payment site also provides the ability to decrypt 1 file free. Unfortunately, since we do not have a sample of the ransomware, and I didn’t want to waste a victim’s free decryption, I do not know if this feature works or not.
The one item that is missing from the payment site is a support page that victim’s can use to contact the malware developers. If this ransomware goes into wider distribution, I would not be surprised to see one added.
We are still actively looking for a sample of this ransomware, so if one is encountered.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











