A new piece of adware that serves as an entry point for future trojan infections was discovered by Dr.Web security researchers.
This new malware was named Adware.Mac.WeDownload.1 because it was first spotted on the WeDownload.com domain, packed with a modified version of Adobe Flash Player.
As Dr.Web researchers found out, the package was signed with “Developer ID Application: Simon Max (GW6F4C87KX)” and was being actively distributed as part of one of those shady affiliate programs that reward developers based on the number of file downloads.
Taking a closer look at the file, researchers found out that, once double-clicked, the adware would first want administrator privileges on the infected machine, with the purpose of installing the Flash Player package.
If this was granted, it would then start initiating communications with a C&C server whose address was hard-coded in its source code, getting the information needed to prompt the user to install all kinds of nasty applications on their Mac.
From the few observed instances, Adware.Mac.WeDownload.1 was recorded trying to install Mac applications infected with trojans like Program.Unwanted.MacKeeper, Mac.Trojan.Crossrider, Mac.Trojan.Genieo, Mac.BackDoor.OpinionSpy, and various Trojans belonging to the Trojan.Conduit family.
The types of applications a victim receives to install depends on their geographical coordinates, which is a twist in regular adware strategy, which usually tries to achieve a quota of installations before moving to the next malicious app in its queue.
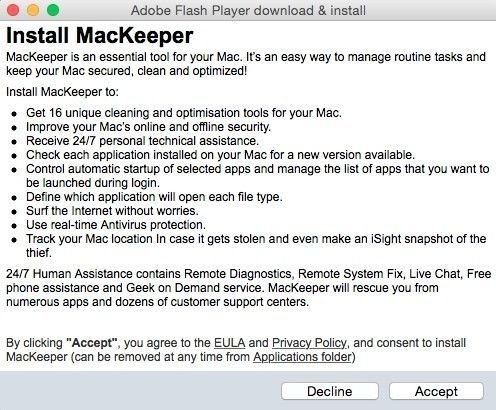
Source:https://news.softpedia.com/

He is a well-known expert in mobile security and malware analysis. He studied Computer Science at NYU and started working as a cyber security analyst in 2003. He is actively working as an anti-malware expert. He also worked for security companies like Kaspersky Lab. His everyday job includes researching about new malware and cyber security incidents. Also he has deep level of knowledge in mobile security and mobile vulnerabilities.










