Tor has been the go-to for anonymous communication online for years now — and that has made it one of the juiciest targets possible to the likes of the NSA and FBI. A new anonymizing protocol from MIT may prove more resilient against such determined and deep-pocketed attackers.
The potential problem with Tor is that if an adversary gets enough nodes on the network, they can work together to track the progress of packets. They might not be able to tell exactly what is being sent, but they can put together a breadcrumb trail tying a user to traffic coming out of an exit node — at least, that’s the theory.
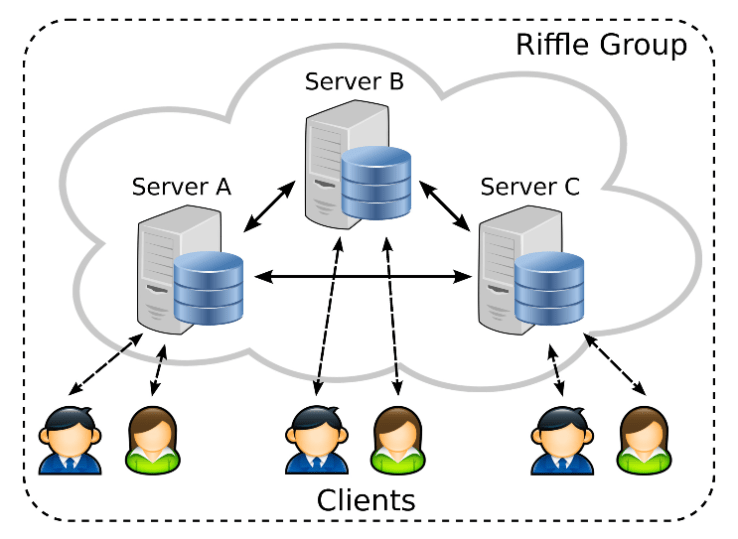
A team of researchers led by MIT grad student Albert Kwon (with help from EPFL) aims to leapfrog Tor’s anonymizing technique with a brand new platform called Riffle.
“Tor aims to provide the lowest latency possible, which opens it up to certain attacks,” wrote Kwon in an email to TechCrunch. “Riffle aims to provide as much traffic analysis resistance as possible.”

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.