On Tuesday, Facebook CEO Mark Zuckerberg posted a cutesy photo to Facebook celebrating Instagram’s now having half a billion users. It featured Zuck posing inside an IRL Instagram frame. It also featured, in the background, what we can assume is Zuck’s computer. And it features a couple of paranoid add-ons, as noted by Twitter user Chris Olson.
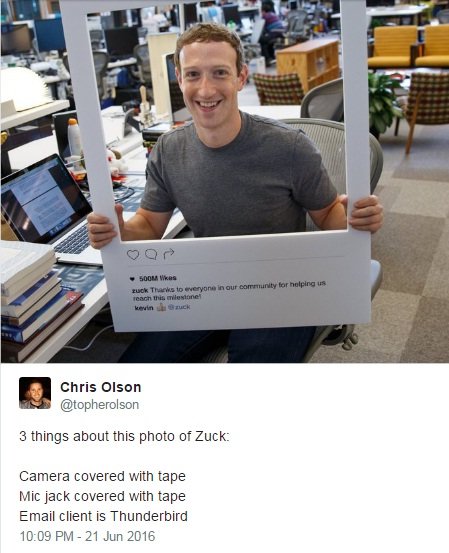
Indeed. His Macbook has tape on it.

One of these is well-placed tape; the other, not necessarily.

Putting tape over your webcam is a great idea and EVERYONE should do it. Even the FBI director does it. If a hacker manages to get into your computer, it will be hell for you, but this is a super simple way to keep them from taking photos of you, especially naked ones that could later be used to embarrass, harass or blackmail you. (It won’t prevent them from stealing existing photos from your computer, however, so make sure you’re encrypting your naked selfies.)
So, good job, Zuck. It almost makes us forgive your alleged mistake of using the password “dadada” on multiple accounts.
However, putting tape over your microphone jack is not going to be effective in making your computer hacker-proof. That’s just going to keep someone from plugging their headphones into your machine. If Olson is wrong, and Zuck has in fact put tape over the mic holes, though, that will muffle the computer’s hearing ability, per a test conducted in our office.
If you’re really paranoid and want to completely kill the omnidirectional microphone, you’d actually need to do some computer surgery.
“The paranoid people I know either cut the wire or use hot glue,” said ACLU technologist Chris Soghoian via Twitter direct message. Try at your own risk.
It’s more likely that Zuckerberg has tape over the mic holes, because tape alone over the mic jack is just going to make it annoying for you to listen to music privately, not make it impossible for hackers to listen to you.

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











