We had 4 new ransomware infections, 2 updates, and one TeslaCrypt news item this week, but for the most part there was nothing that interesting released. When I write these weekly roundups, I try to credit the source of the discovery. If I missed anyone, please let me know.
A big thanks to all the people who have been hammering at ransomware on Twitter and elsewhere! This article is the combined effort of all of them,
May 21st 2016
CryptXXX was updated to Vesion 3.x and broke all of the Decryptors including their Own.
On May 21st, the developers behind CryptXXX released version 3.0 of their ransomware. This version fixed the weakness that Kaspersky was exploiting to allow victims to decrypt their files for free. At the same time, it also broke the decryptor the malware developers were providing to those who paid the ransom. It wasn’t until May 25th, that the malware devs released a properly working decryptor.
May 22nd 2016
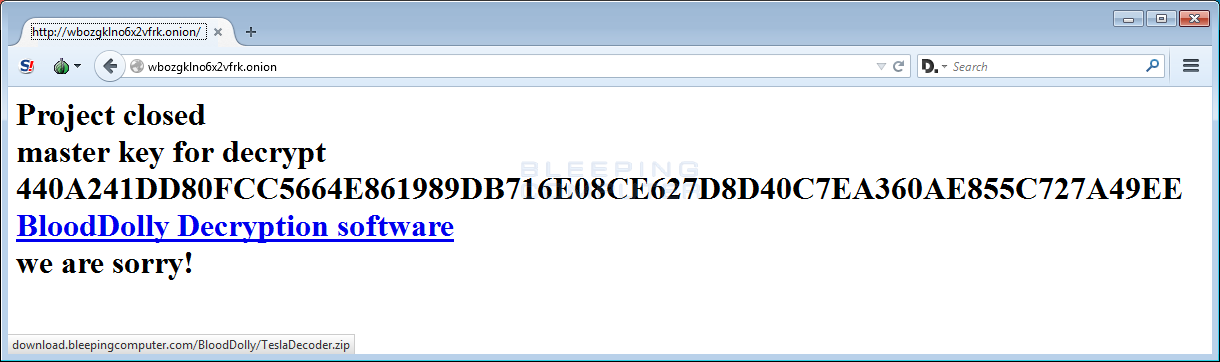
TeslaCrypt links to BloodDolly’s TeslaDecoder from their defunct Payment Site
The TeslaCrypt authors changed the message on their last remaining TOR site to suggest that victim’s download BloodDolly’s TeslaDecoder program in order to decrypt Teslacrypt encrypted files. More info here: TeslaCrypt Developers recommend TeslaDecoder to Decrypt Files.
New ransomware discovered called ODCODC
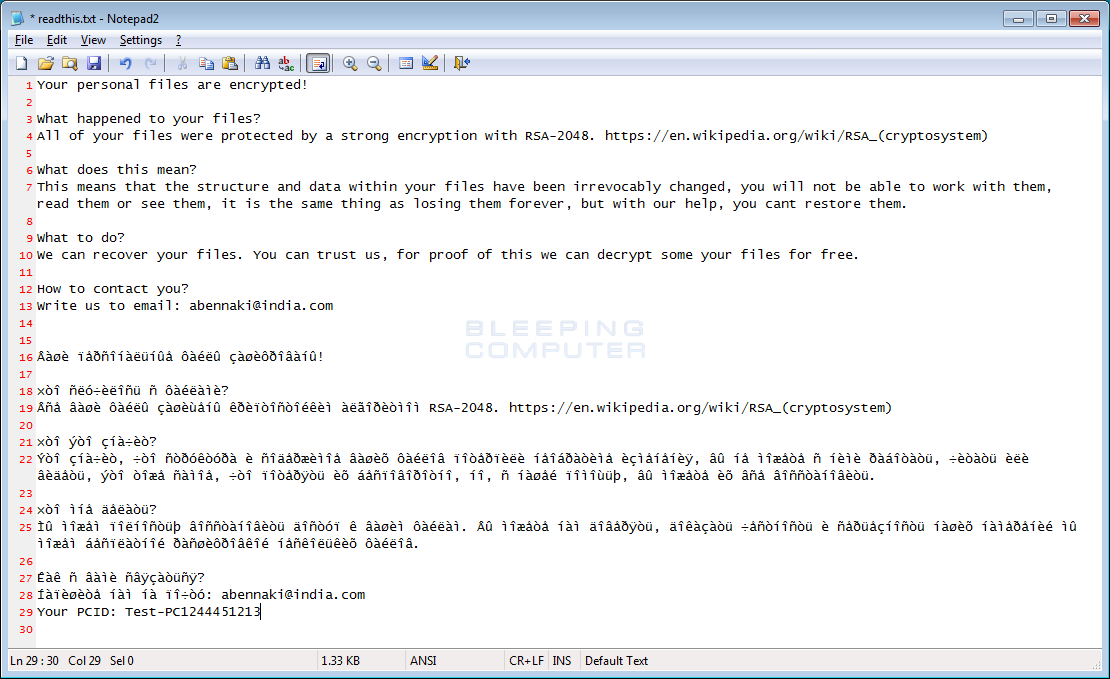
A new ransomware was discovered by security researcher MichaelGillespie that we have dubbed ODCODC after the extension it appends to encrypted files. According to MalwareHunterTeam, when infecting a computer it will encrypt its data and change the filename to something like [single_character]-email-abennaki@india.com-test.jpg.odcodc or in the format %emailaddress%-%originalfilename%.odcodc. The single character in the first renaming pattern may be the drive letter that file was located on.
Furthermore, MalwareHunterTeam also stated that the Command & Control server is inststats[.]com and the same server hosts a ton of phishing pages and malware downloads.
Unfortunately, there is no solution for this ransomware as of yet.
May 24th 2016
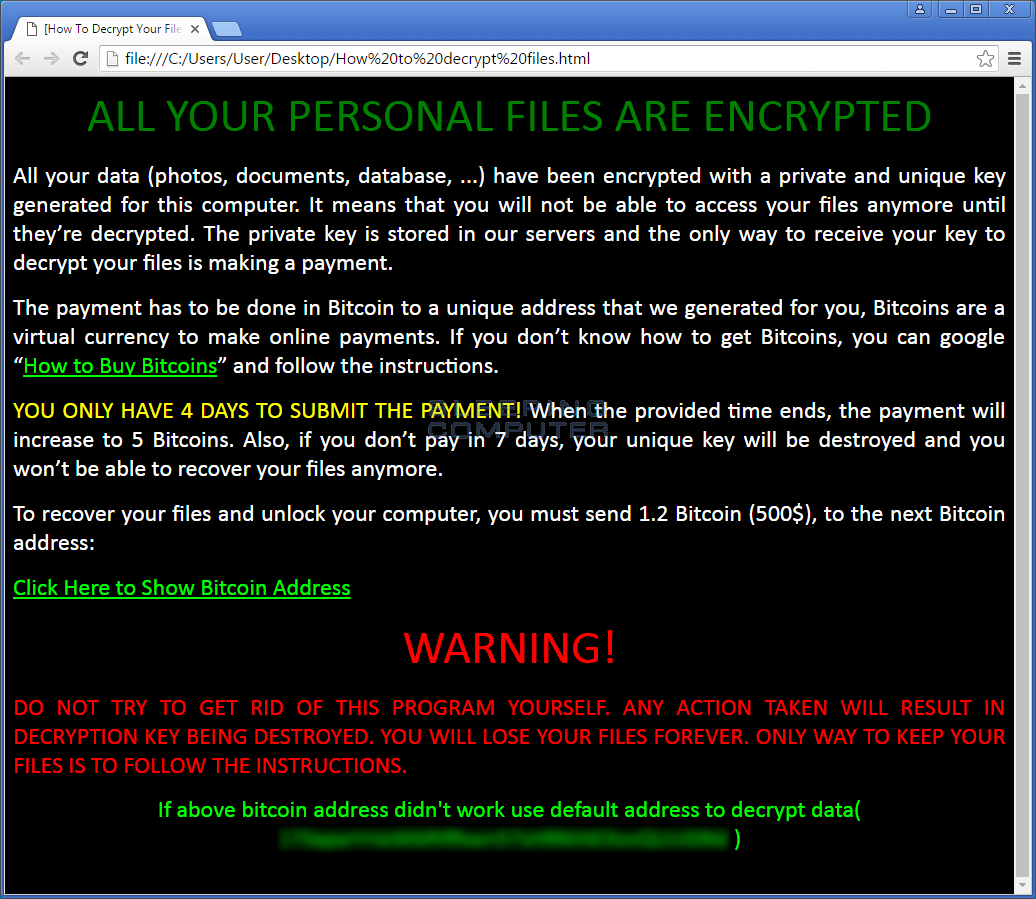
The Zcrypt Ransomware is Released
A new ransomware called Zcrypt was discovered by security researcher Jack. When infected with Zcrypt it will encrypt your data and append the .zcrypt extension to the filenames. It will then ransom the decryption key for 1.2 bitcoins.
This ransomware was almost over before it started. In the variant I looked at, the communication with the Command & Control server was broken and I had to use some creative request edits to get it to download the correct files. For the most, I do not currently see a wide distribution of this ransomware.
On May 26th, Microsoft released a blog post about Zcrypt. Microsoft states that Zcrypt can spread via create autorun.inf files on USB drives and via network shares. I see evidence of the autorun.inf, but not sure where they are seeing the network drive propogation.
Zyklon Ransomware starts to use the .Zyklon Extension for Encrypted Files
A new version of Zyklon Ransomware was released that appends the .Zyklonextension to encrypted files. Otherwise, it’s pretty much the same ransomware as the previous release.
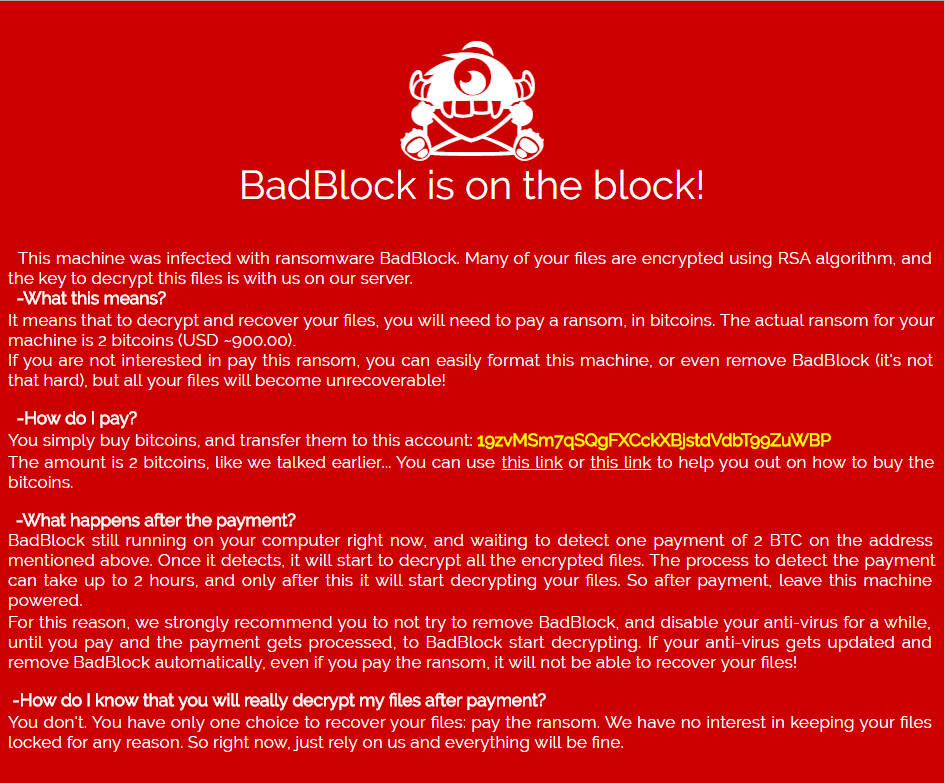
New ransomware called BadBlock was released
A new ransomware called BadBlock was discovered by security researcher S!Ri with analysis by Mosh. When infected, it encrypts your data and then requests 2 bitcoins to get your encryption. When it encrypts your files it willnot append a special extension to the files. An example of the BadBlock ransom note can be seen below.
May 26th 2016
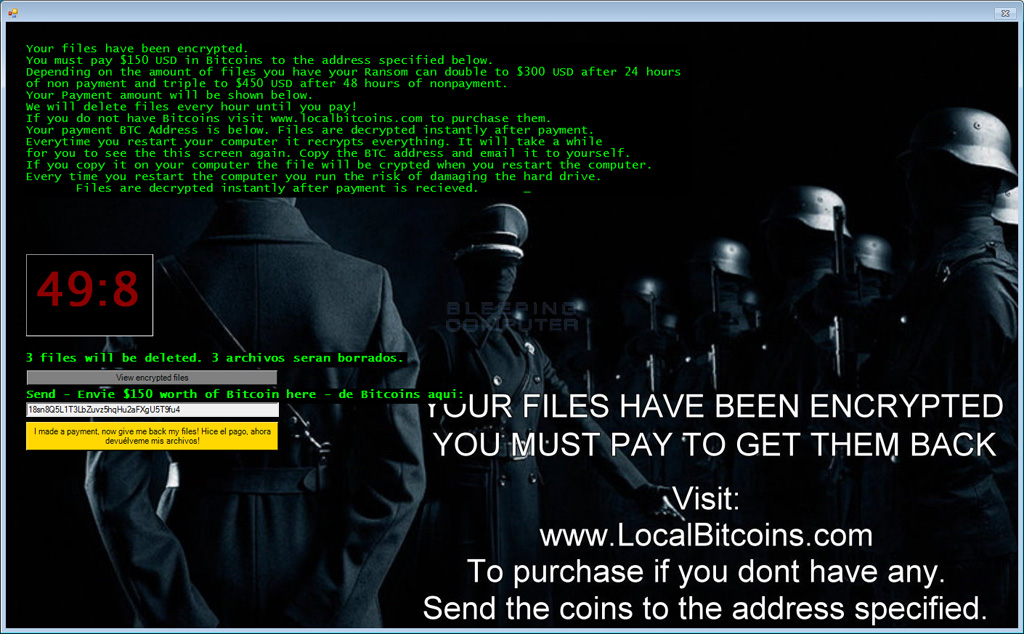
New Invisible Empire variant of Jigsaw Discovered
A new variant of the Jigsaw Ransomware was discovered that uses artwork from Juha ArvidHelminen called the Invisible Empire. The Invisible Empire theme is really appropriate for the ransomware, as it depicts how people can hide behind uniforms when performing atrocities or criminal acts. Just like previous Jigsaw variants, this ransomware will delete files periodically until you make the payment. Thankfully, the Jigsaw decryptor was updated to handle this variant.
More info here: Invisible Empire themed Jigsaw Ransomware Variant Released.
That’s it for this week. As always if any new ransomware is released, please feel free to contact me.
Source:https://www.bleepingcomputer.com/

Working as a cyber security solutions architect, Alisa focuses on application and network security. Before joining us she held a cyber security researcher positions within a variety of cyber security start-ups. She also experience in different industry domains like finance, healthcare and consumer products.











